ECR Lifecycle Policy to automatically delete outdated images
Lifecycle policies can be set for images pushed to ECR.
This page aims to set up a lifecycle policy to automatically delete outdated images.
Environment
Create an ECR.
Set a lifecycle policy and delete images so that if there are two or more untagged images, there will be only one.
CloudFormation template files
Build the above configuration with CloudFormation.
The CloudFormation templates are located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/077
Explanation of key points of the template files
ECR
Resources:
ECRRepository:
Type: AWS::ECR::Repository
Properties:
LifecyclePolicy:
LifecyclePolicyText: |
{
"rules": [
{
"rulePriority": 1,
"description": "Keep only one untagged image, expire all others",
"selection": {
"tagStatus": "untagged",
"countType": "imageCountMoreThan",
"countNumber": 1
},
"action": {
"type": "expire"
}
}
]
}
RegistryId: !Ref AWS::AccountId
RepositoryName: !Ref Prefix
Code language: YAML (yaml)The LifecyclePolicy property is the key.
The LifecyclePolicyText property within this property defines the lifecycle policy.
The notation of the lifecycle policy is detailed on the official AWS page.
https://docs.aws.amazon.com/AmazonECR/latest/userguide/lifecycle_policy_examples.html
In this case, images will be expired/deleted based on the number of images.
Specifically, if the number of untagged images is greater than 1, the lifecycle policy will expire and delete the oldest image.
Architecting
Use CloudFormation to build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create a CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created in this case is as follows
- ECR: fa-077
Check the created resources from the AWS Management Console.
Check the ECR.
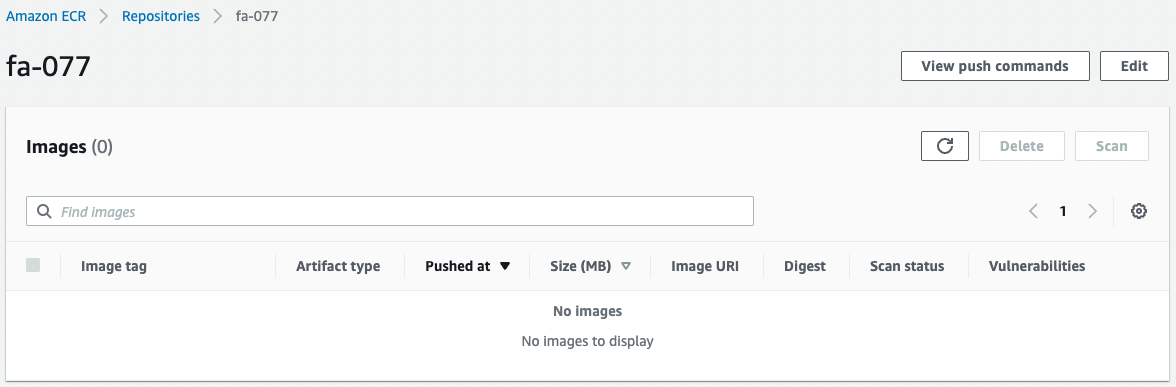
The ECR has been successfully created.
Next, check the lifecycle policy of the ECR.
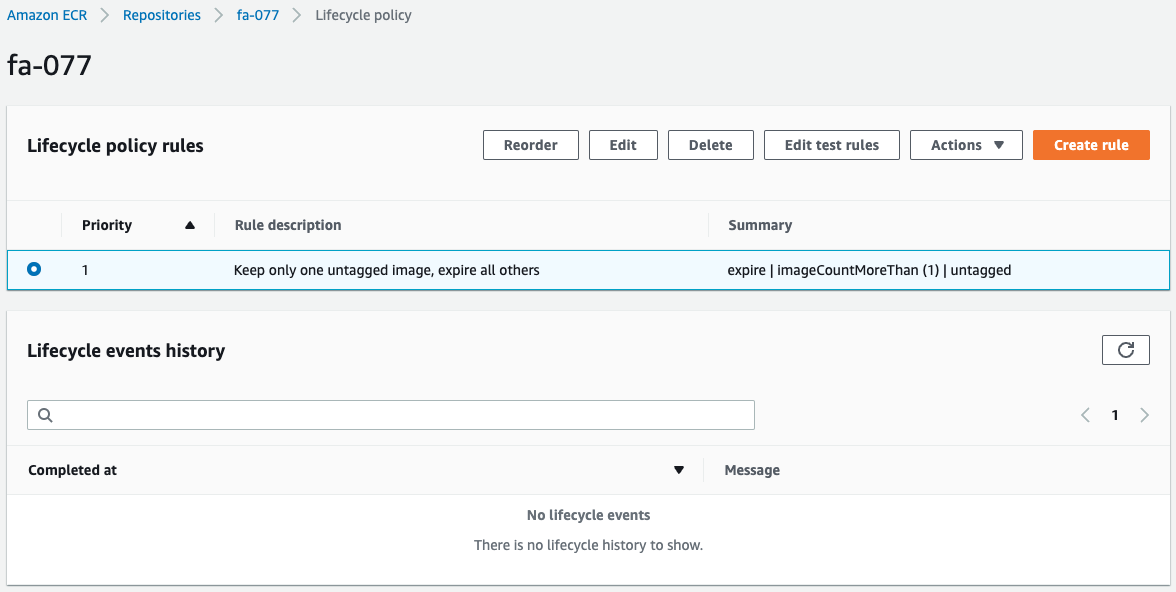
If the number of untagged images is greater than 1, the policy is to expire the oldest image.
At this time, no images have been pushed to the ECR, so the lifecycle policy is not being enforced.
Check Action
1st image push
Now that everything is ready, push the image to the ECR.
$ aws ecr get-login-password --region ap-northeast-1 | docker login --username AWS --password-stdin [account-id].dkr.ecr.ap-northeast-1.amazonaws.com
...
Login Succeeded
$ docker build -t fa-077 .
...
Successfully built ef0e8aec8ddc
Successfully tagged fa-077:latest
$ docker tag fa-077:latest [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
$ docker push [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
The push refers to repository [[account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077]
209cb42bdfb7: Pushed
latest: digest: sha256:c9ce7208912b7897c9a4cb273f20bbfd54fd745d1dd64f5e625fff6778469e69 size: 529
Code language: Bash (bash)The image was successfully built and pushed.
Check the ECR.
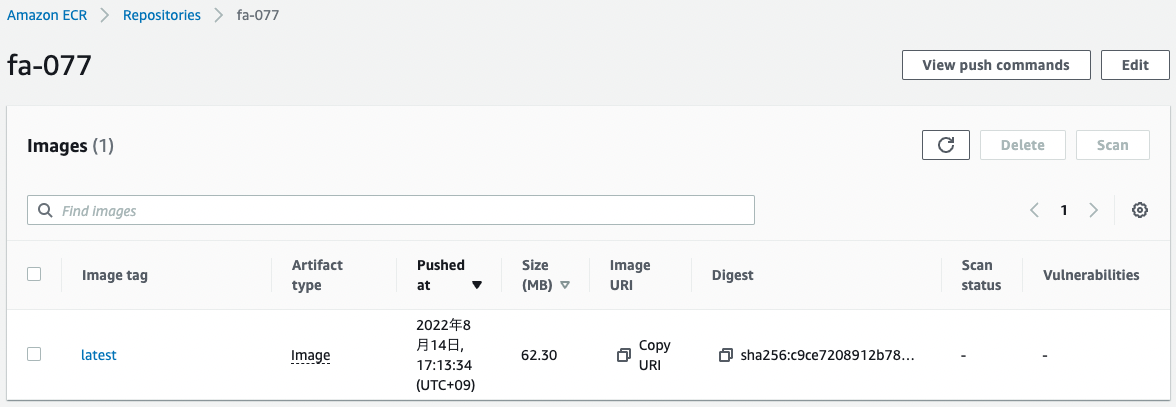
The image has indeed been pushed.
Check the execution history of the lifecycle policy.
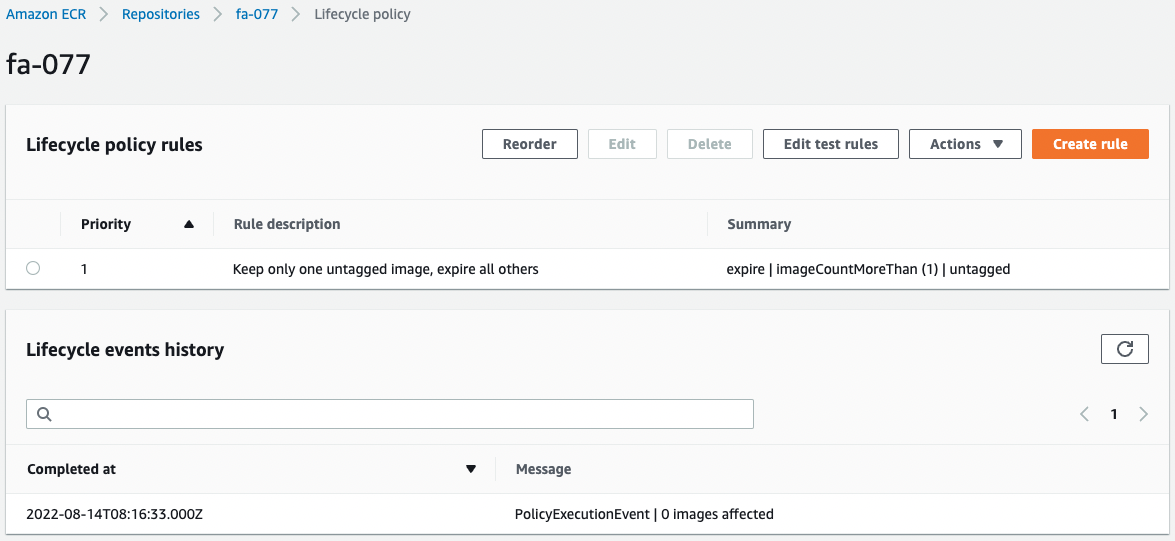
The lifecycle policy has indeed been executed.
However, nothing occurred because there were no images that satisfied the conditions.
2nd image push
Repeat the same process again.
$ docker build -t fa-077 .
...
Successfully built a4c9f809ffa5
Successfully tagged fa-077:latest
$ docker tag fa-077:latest [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
$ docker push [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
The push refers to repository [[account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077]
209cb42bdfb7: Layer already exists
latest: digest: sha256:9bbe64cb64212516c9adf5a9961a270388b6b2065b87cc878b38c1d7c77a510f size: 529
Code language: Bash (bash)Once again the image build/push was successfully executed.
Check the ECR.
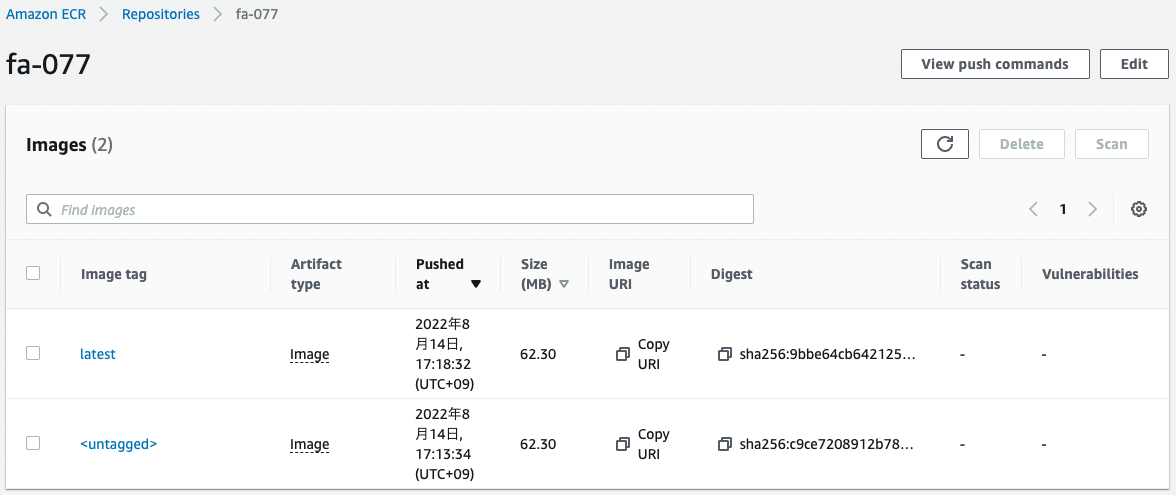
The image has indeed been pushed.
The “latest” tag is set to the newly pushed image, and the tag information of the image pushed the first time has changed to “<untagged>”.
Check the lifecycle policy.
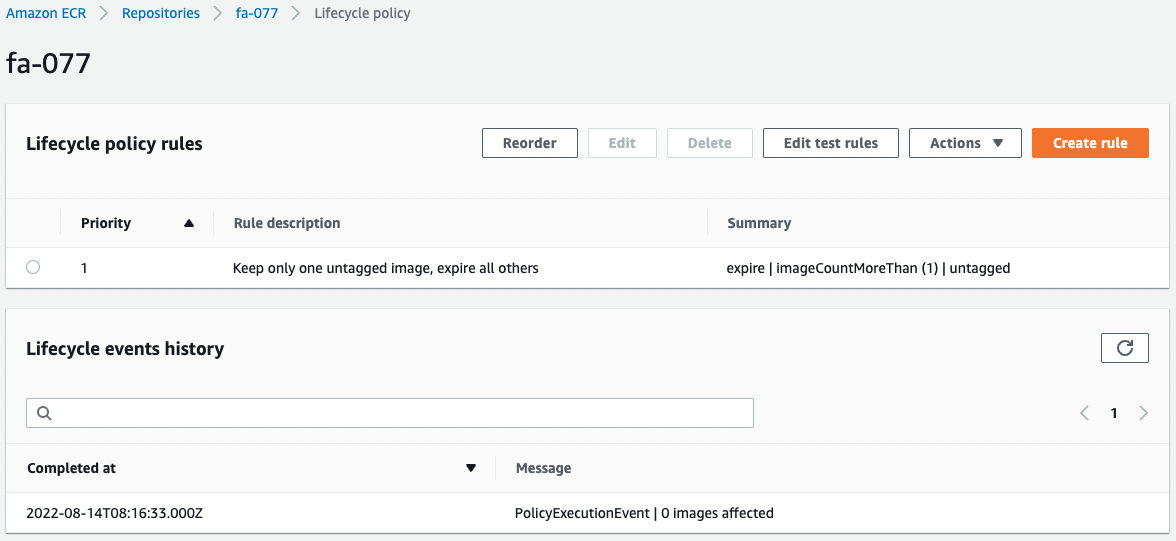
There is no change here.
We now have an untagged image, but still only one.
Therefore, the conditions for executing the lifecycle policy are not met.
3rd image push
Third image push.
$ docker build -t fa-077 .
...
Successfully built efafe9ee6cc5
Successfully tagged fa-077:latest
$ docker tag fa-077:latest [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
$ docker push [account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077:latest
The push refers to repository [[account-id].dkr.ecr.ap-northeast-1.amazonaws.com/fa-077]
209cb42bdfb7: Layer already exists
latest: digest: sha256:4adf0089f316607778fd6a5e073205b767bd849ac8a2234921fddc4351139b96 size: 529Three times the image was successfully built and pushed.
Check the ECR.
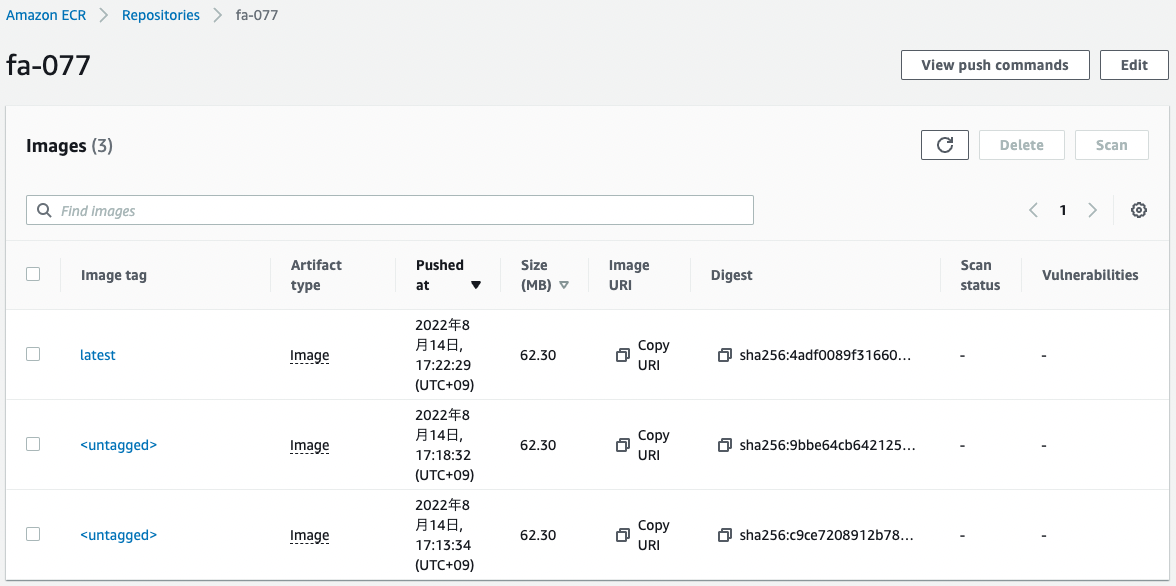
The image has indeed been pushed.
The “latest” tag is set to the newly pushed image, and the tag information for the images pushed the first and second time has changed to “<untagged>”.
This satisfies the condition for the lifecycle policy to act.
After waiting for a while, check the Lifecycle Policy.
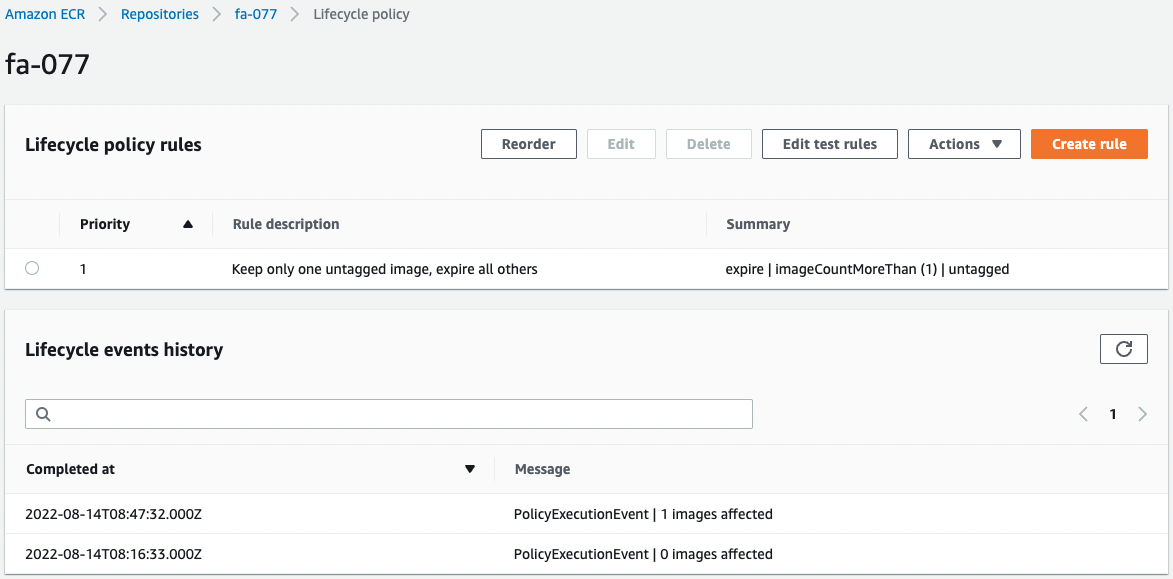
The execution history has been added to the lifecycle policy.
The message indicates that one image that satisfies the condition has been deleted.
Check the ECR again.
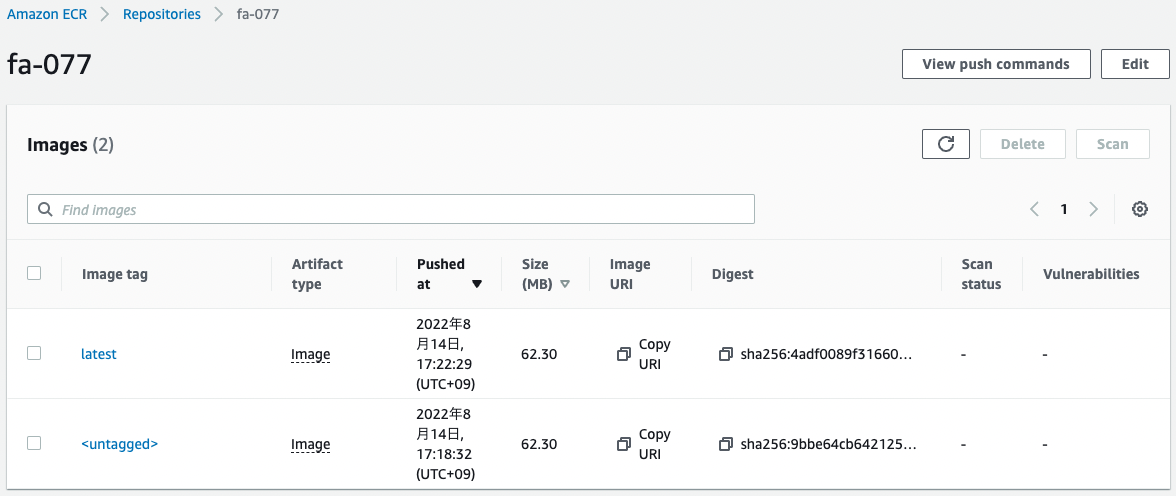
Two images can be seen.
The two untagged images are now one.
This indicates that the lifecycle policy has acted correctly and automatically deleted the old image that met the criteria.
Summary
We have confirmed how to set up a lifecycle policy to automatically delete old images.