Introduction to AWS Config with CFN – Auditing S3 Bucket Logging Settings
AWS Config is a service for evaluating and auditing resource configurations.
AWS Config is a fully managed service that provides you with an AWS resource inventory, configuration history, and configuration change notifications to use security and governance.
AWS Config FAQs
The goal of this page, an introduction to AWS Config, is to audit the enable/disable of S3 bucket logging settings.
Environment
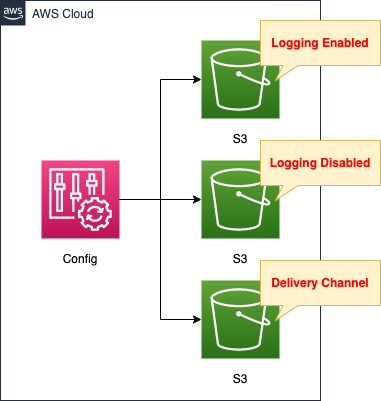
Create a rule in AWS Config to audit the logging settings status of S3 buckets.
Create three S3 buckets.
Two of the buckets are to be audited.
Each has logging enabled/disabled.
The remaining one is the bucket used for AWS Config action.
It stores data regarding the configuration and modification status of AWS resources.
CloudFormation template files
The above configuration is built using CloudFormation.
The CloudFormation template is located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/097
Explanation of key points of the template files
S3 Buckets
Bucket for Delivery Channel
Resources:
ConfigBucket:
Type: AWS::S3::Bucket
Properties:
BucketName: !Sub "${Prefix}-config"
AccessControl: Private
Code language: YAML (yaml)To enable AWS Config, a delivery channel must be created, described below.
One of the parameters of the delivery channel is the S3 bucket.
The S3 bucket is used to store data about the configuration and change status of AWS resources.
This bucket is for the delivery channel, but no special configuration is required.
Resources:
ConfigBucketPolicy:
Type: AWS::S3::BucketPolicy
Properties:
Bucket: !Ref ConfigBucket
PolicyDocument:
Statement:
- Principal:
Service: config.amazonaws.com
Action: s3:GetBucketAcl
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}"
Condition:
StringLike:
AWS:SourceAccount: !Ref AWS::AccountId
- Principal:
Service: config.amazonaws.com
Action: s3:ListBucket
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}"
Condition:
StringLike:
AWS:SourceAccount: !Ref AWS::AccountId
- Principal:
Service: config.amazonaws.com
Action: s3:PutObject
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}/*"
Condition:
StringLike:
s3:x-amz-acl: bucket-owner-full-control
AWS:SourceAccount: !Ref AWS::AccountId
Code language: YAML (yaml)The S3 bucket used for the delivery channel must be allowed various accesses from AWS Config.
In this case, we will use the following page to grant access using a bucket policy.
https://docs.aws.amazon.com/config/latest/developerguide/s3-bucket-policy.html
Specify “config.amazonaws.com” as the principal and grant three permissions (s3:GetBucketAcl, s3:ListBucket, s3:PutObject) for this bucket.
(Reference) Bucket to be audited
Resources:
Bucket1:
Type: AWS::S3::Bucket
Properties:
BucketName: !Sub "${Prefix}-logging-enable"
AccessControl: Private
LoggingConfiguration:
DestinationBucketName: !Ref LogBucket
Bucket2:
Type: AWS::S3::Bucket
Properties:
BucketName: !Sub "${Prefix}-logging-disable"
AccessControl: Private
Code language: YAML (yaml)Create two S3 buckets for this audit.
One will have logging settings enabled and the other will be disabled.
For more information on the logging functionality of S3 buckets, please also check the following page
AWS Config
To audit resources in AWS Config, create the following three resources
- Distribution Channel
- Config Recorder
- AWS Config Rules
Delivery Channel
The delivery channel is where data about the configuration and change status of an AWS resource is stored.
Resources:
DeliveryChannel:
Type: AWS::Config::DeliveryChannel
Properties:
Name: !Sub "${Prefix}-DeliveryChannel"
S3BucketName: !Ref ConfigBucket
Code language: YAML (yaml)As AWS Config continually records the changes that occur to your AWS resources, it sends notifications and updated configuration states through the delivery channel. You can manage the delivery channel to control where AWS Config sends configuration updates.
Managing the Delivery Channel
In the S3BucketName property, specify the bucket for which you defined the bucket policy described earlier.
Configuration Recorder
The configuration recorder is a resource that specifies the target resource for detecting configuration and change status.
Resources:
ConfigurationRecorder:
Type: AWS::Config::ConfigurationRecorder
Properties:
Name: !Sub "${Prefix}-ConfigurationRecorder"
RecordingGroup:
AllSupported: false
IncludeGlobalResourceTypes: false
ResourceTypes:
- AWS::S3::Bucket
RoleARN: !Sub "arn:aws:iam::${AWS::AccountId}:role/aws-service-role/config.amazonaws.com/${AWSServiceRoleForConfig}"
Code language: YAML (yaml)AWS Config uses the configuration recorder to detect changes in your resource configurations and capture these changes as configuration items. You must create a configuration recorder before AWS Config can track your resource configurations.
Managing the Configuration Recorder
In this case, we will configure it to detect situations related to S3 buckets.
A particularly important parameter is the RoleARN property.
In order for the configuration recorder to detect the status of an AWS resource, it must be authorized to access the target resource.
The AWS official best practice is to use a service-linked role (SLR).
A service-linked role (SLR) makes setting up AWS Config easier because you don’t have to manually add the necessary permissions for Config to record the configuration of AWS services that Config supports. AWS Config uses the service-linked role named AWSServiceRoleForConfig. AWS Config uses this service-linked role to call other AWS services on your behalf. The permissions policy for this role contains read-only and write-only permissions on the AWS Config resources and read-only permissions for resources in other services that AWS Config supports.
AWS Config best practices
Below are the SLR for AWS Config.
Resources:
AWSServiceRoleForConfig:
Type: AWS::IAM::ServiceLinkedRole
DeletionPolicy: Delete
Properties:
AWSServiceName: config.amazonaws.com
Code language: YAML (yaml)Note the Type property.
For a normal IAM role, specify “AWS::IAM::Role”, but to create a SLR, specify “AWS::IAM::ServiceLinkedRole”.
Specify “config.amazonaws.com” for the AWSServiceName property.
AWS Config Rules
AWS Config rules are resources that define audit content.
Resources:
S3BucketLoggingEnabledConfigRule:
Type: AWS::Config::ConfigRule
DependsOn:
- ConfigurationRecorder
Properties:
ConfigRuleName: !Sub "${Prefix}-S3-Bucket-Logging-Enabled"
Scope:
ComplianceResourceTypes:
- AWS::S3::Bucket
Source:
Owner: AWS
SourceIdentifier: S3_BUCKET_LOGGING_ENABLED
Code language: YAML (yaml)Configure the S3 bucket logging settings to be evaluated for enable/disable.
This can be accomplished by using the AWS managed rule “s3-bucket-logging-enabled”.
Checks whether logging is enabled for your S3 buckets.
s3-bucket-logging-enabled
For a list of AWS managed rules, please see the following page
https://docs.aws.amazon.com/config/latest/developerguide/managed-rules-by-aws-config.html
Architecting
Use CloudFormation to build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create a CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- Bucket for AWS Config: fa-097-config
- AWS Config rule: fa-097-Bucket-Logging-Enabled
- Role for AWS Config: AWSServiceRoleForConfig
- Bucket to be audited 1: fa-097-logging-enabled
- Bucket to be audited2: fa-097-logging-disabled
Confirm the created resource from the AWS Management Console.
Check the bucket policy of the bucket for AWS Config.
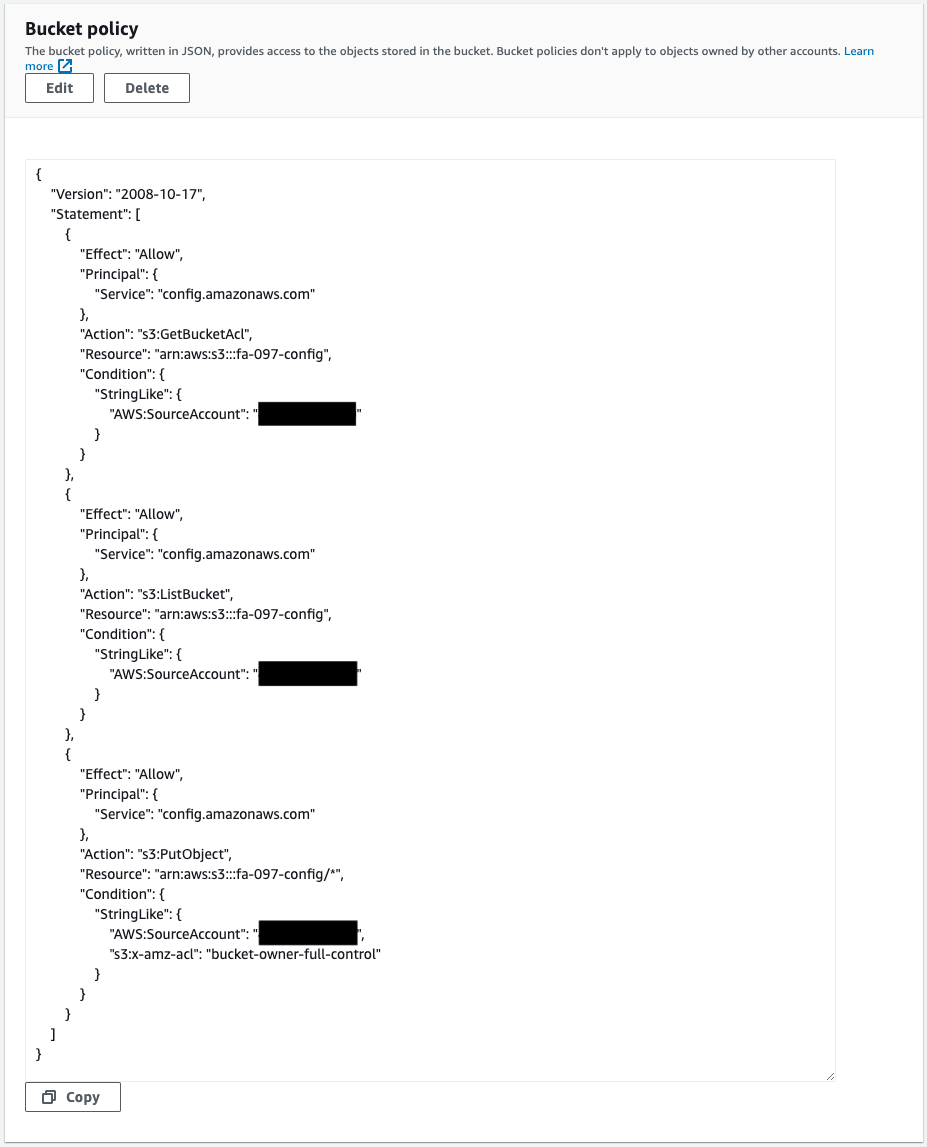
The bucket policy defined in the CloudFormation template is applied.
Check the two buckets to be audited.
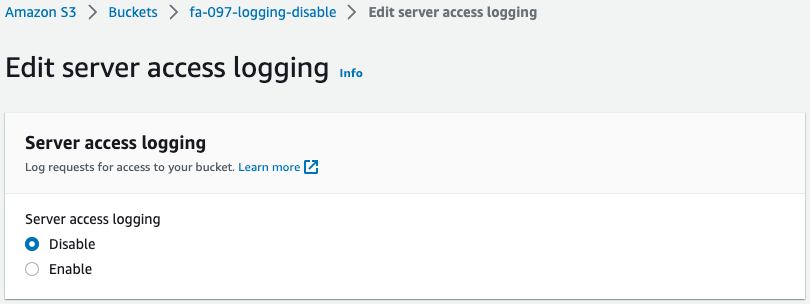
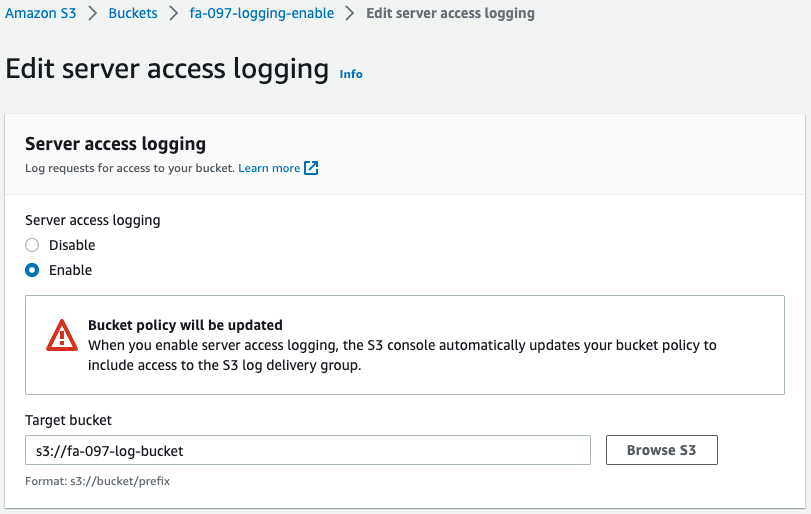
You can see that the logging function is enabled/disabled for each of them.
Check the role for AWS Config.
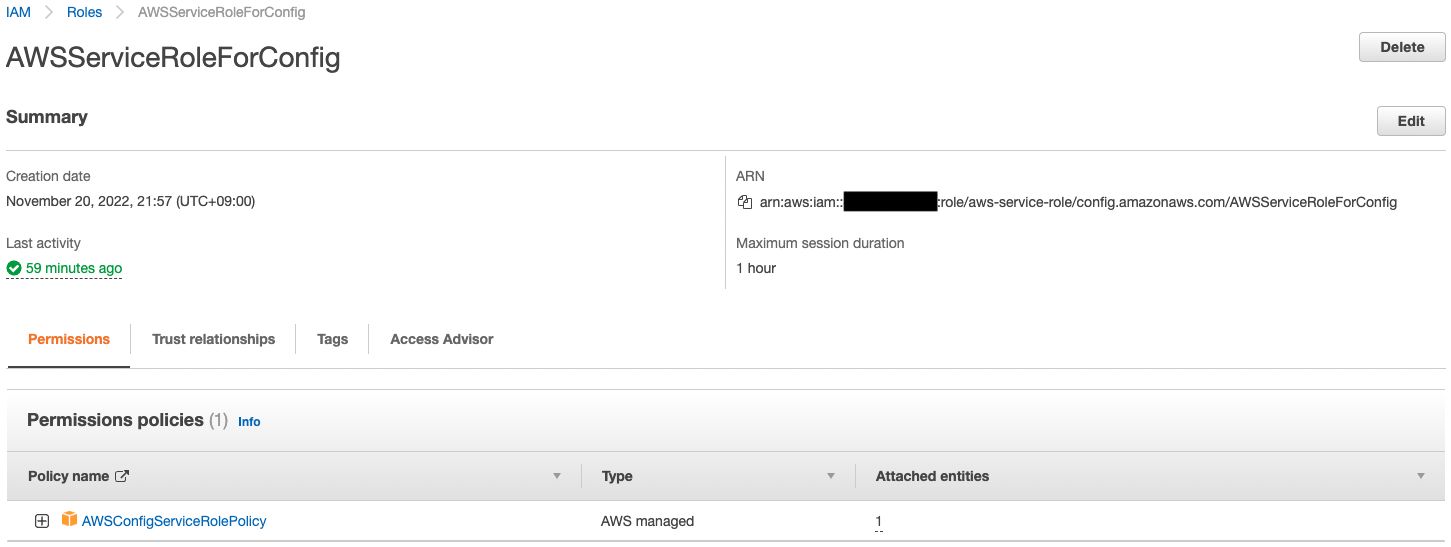
By creating a SLR for AWS Config, the AWSConfigServiceRolePolicy was automatically attached.
This policy can only be attached to SLR.
Check AWS Config.
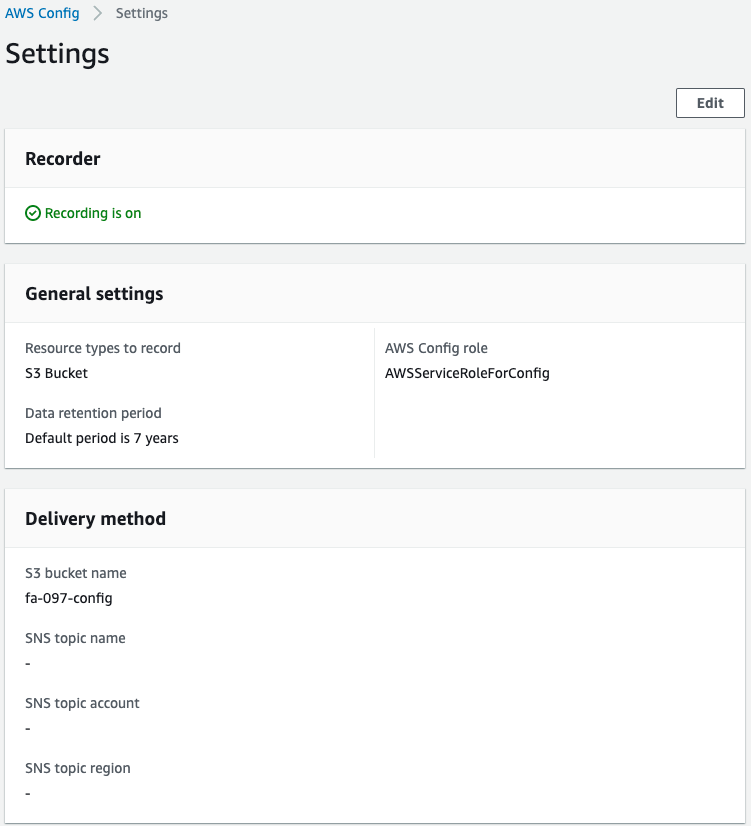
Recoder item and see that “Recording is on”.
You can see that the configuration recorder is acting correctly.
Looking at the AWS Config role in the General settings section, we see “AWSServiceRoleForConfig”.
You can see that the role linked to the aforementioned service is specified.
If you look at the S3 bucket name in the Delivery method item, you will see “fa-097-config”.
This indicates that the aforementioned bucket for AWS Config is specified.
Check the detailed settings of AWS Config.
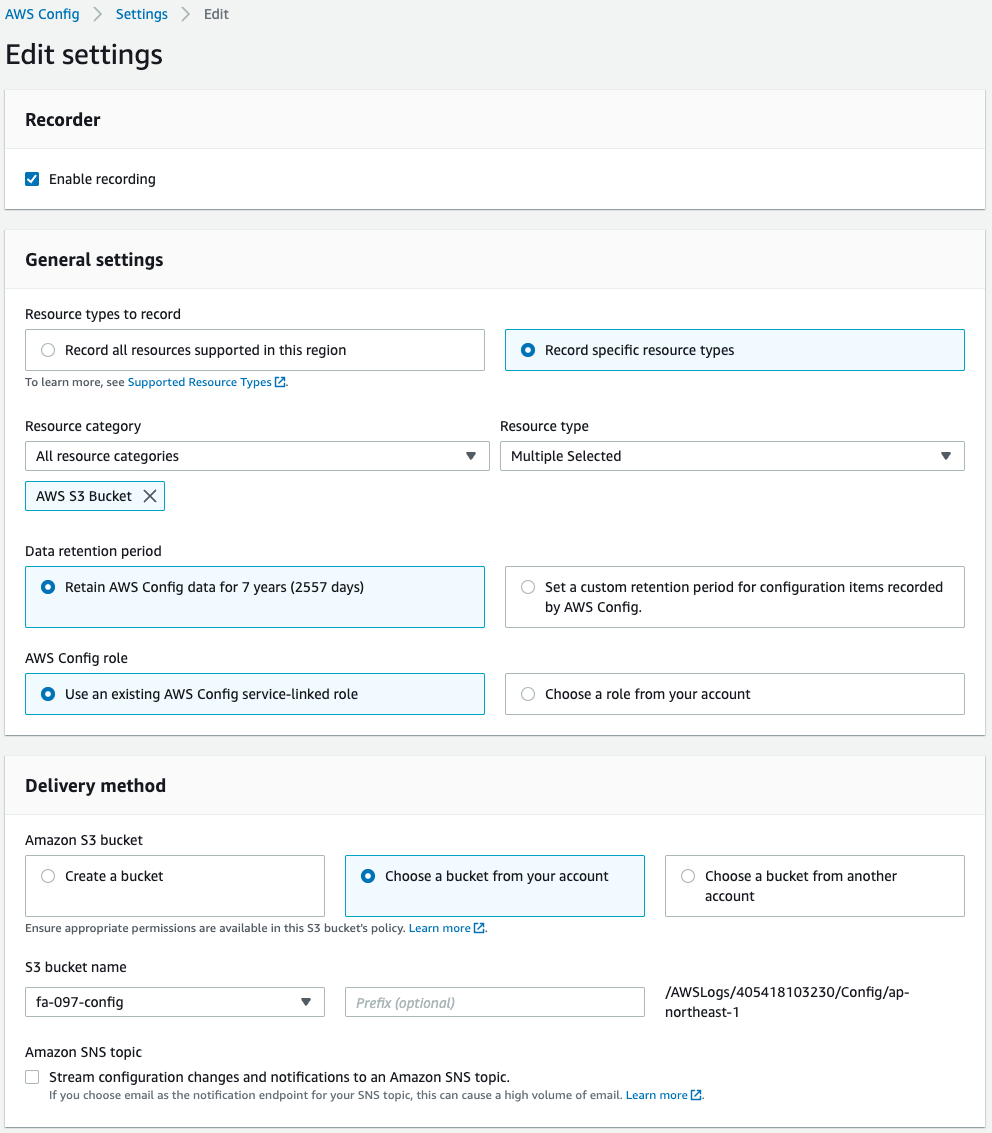
Looking at the Resource types to record and Resource category items, “AWS S3 Bucket” is specified.
This means that only data related to S3 buckets will be collected.
Check the AWS Config rule.
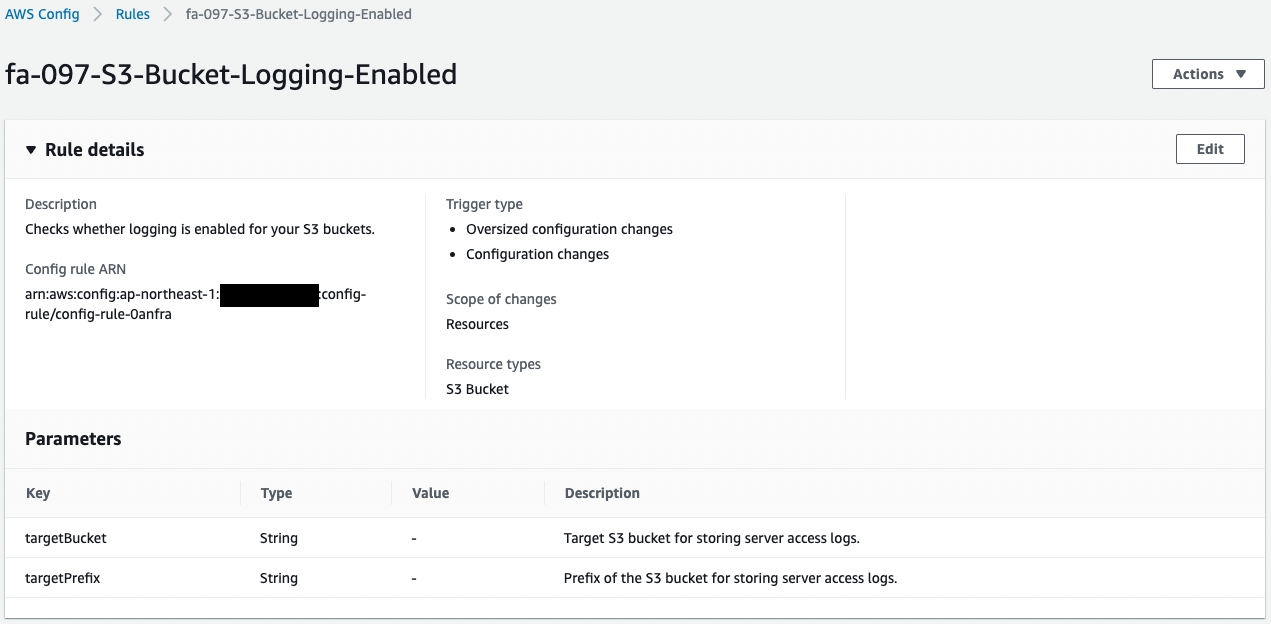
Using the AWS managed rule “s3-bucket-logging-enabled”, we created a rule to audit whether the S3 bucket logging feature is enabled or disabled.
Checking Operation
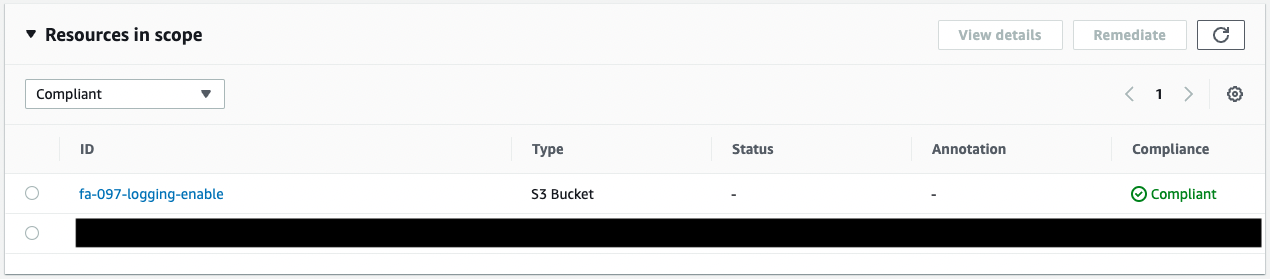
Check the audit results.
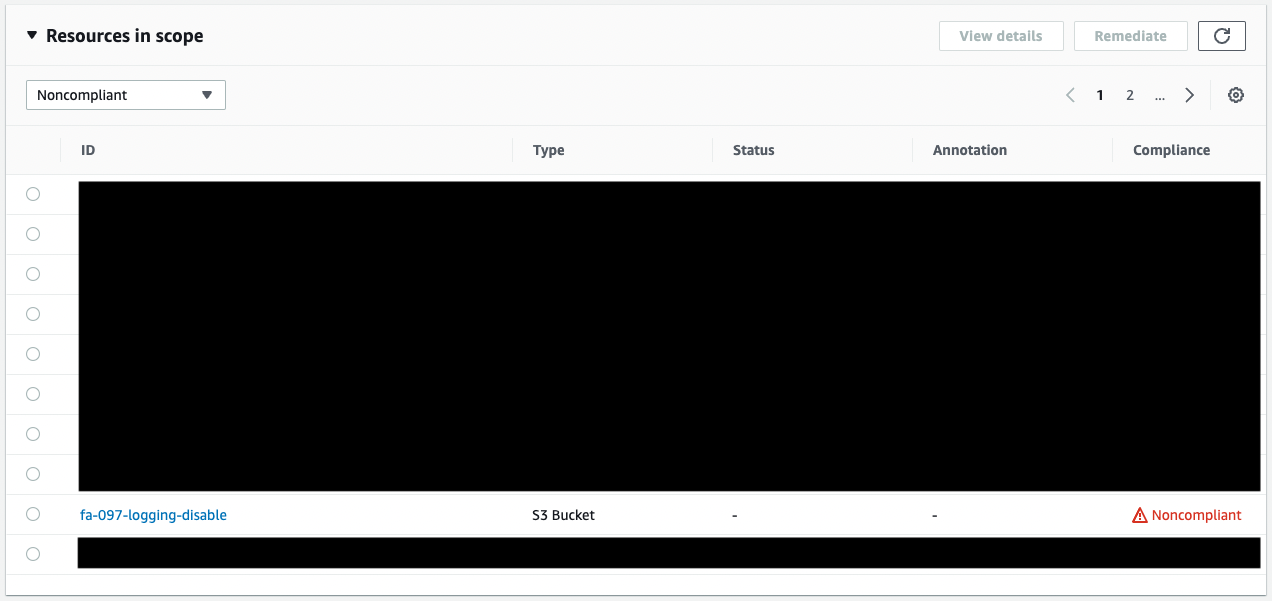
The resource judged as Noncompliant contains fa-097-logging-disable.
The resource judged as Compliant contains fa-097-logging-enabled.
This result is matched with the logging settings for the two buckets.
Using AWS Config, we were able to audit the enable/disable of the logging settings for the S3 bucket.
Summary
As an introduction to AWS Config, we have reviewed how to audit the enable/disable of logging settings for S3 buckets.