Email notifications via SNS when resources are changed using AWS Config
The following page shows you how to use AWS Config to check the change history of a resource.

In this article, we will check how to notify an email via SNS when a resource is changed.
Environment
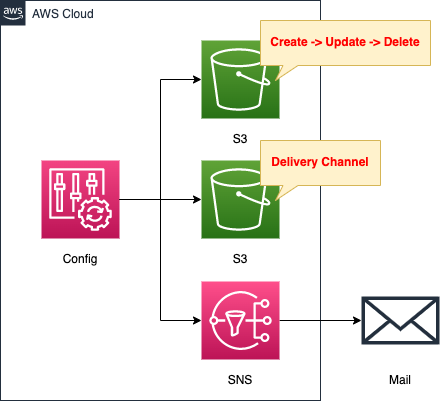
The configuration is generally the same as in the page introduced at the beginning of this article.
Create an S3 bucket as a target to monitor the change history in AWS Config.
Associate an SNS topic with AWS Config and configure it to send an email notification each time a resource change occurs.
CloudFormation template files
Build the above configuration with CloudFormation.
The CloudFormation templates are located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/101
Explanation of key points of the template files
Basically the same as the page introduced at the beginning of this document.
This page focuses on the contents related to email notifications.
SNS Topics
Resources:
Topic:
Type: AWS::SNS::Topic
Properties:
Subscription:
- Endpoint: !Ref MailAddress
Protocol: email
TopicName: !Ref Prefix
Code language: YAML (yaml)Create an SNS topic and specify your email address as the subscriber.
For more information, please see the following page

AWS Config
Resources:
DeliveryChannel:
Type: AWS::Config::DeliveryChannel
Properties:
Name: !Sub "${Prefix}-DeliveryChannel"
S3BucketName: !Ref ConfigBucket
SnsTopicARN: !Ref TopicArn
Code language: YAML (yaml)In the SnsTopicARN property, specify the ARN of the SNS topic you defined earlier for the delivery channel.
Check AWS Config regarding access rights.
Resources:
ConfigurationRecorder:
Type: AWS::Config::ConfigurationRecorder
Properties:
Name: !Sub "${Prefix}-ConfigurationRecorder"
RecordingGroup:
AllSupported: false
IncludeGlobalResourceTypes: false
ResourceTypes:
- AWS::S3::Bucket
RoleARN: !GetAtt ConfigRole.Arn
ConfigRole:
Type: AWS::IAM::Role
DeletionPolicy: Delete
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
Service:
- config.amazonaws.com
ManagedPolicyArns:
- arn:aws:iam::aws:policy/service-role/AWS_ConfigRole
Policies:
- PolicyName: SNSPublishPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- sns:Publish
Resource:
- !Ref TopicArn
Code language: YAML (yaml)In order to be notified of changes via SNS, you must have permission to publish messages to SNS topics (sns:Publish).
The page introduced at the beginning of this article used a Service Linked Role (SLR), but this role does not allow this action.
So we will prepare a role based on the AWS management policy AWS_ConfigRole, with sns:Publish added as an inline policy.
Specify this role to the AWS Config configuration recorder.
(Reference) S3 bucket
Resources:
Bucket:
Type: AWS::S3::Bucket
Properties:
BucketName: !Sub "${Prefix}-encryption-enabled"
AccessControl: Private
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
Code language: YAML (yaml)Prepare an S3 bucket as a verification resource.
Enable SSE.
Architecting
Use CloudFormation to build this environment and verify actual behavior.
Create CloudFormation stacks and verify resources in stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- SNS topic: fa-101
- Bucket for verification: fa-101-encryption-enabled
Authentication of email address
If an e-mail address is specified as a subscriber to an SNS topic, the e-mail address must be authenticated.
The following authentication email will be sent to the specified email address.
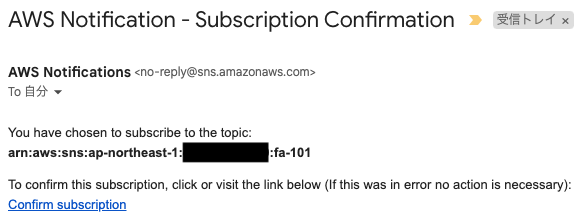
Click “Confirm subscription” to proceed with the authentication.
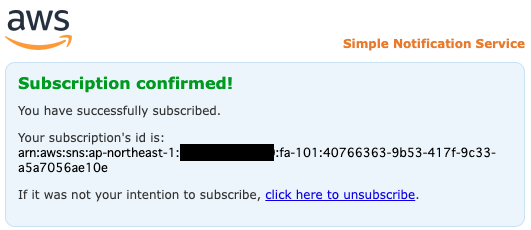
The above page will appear, indicating that the authentication has been completed.
Resource Confirmation
Check each resource from the AWS Management Console.
First, check the SNS topic.
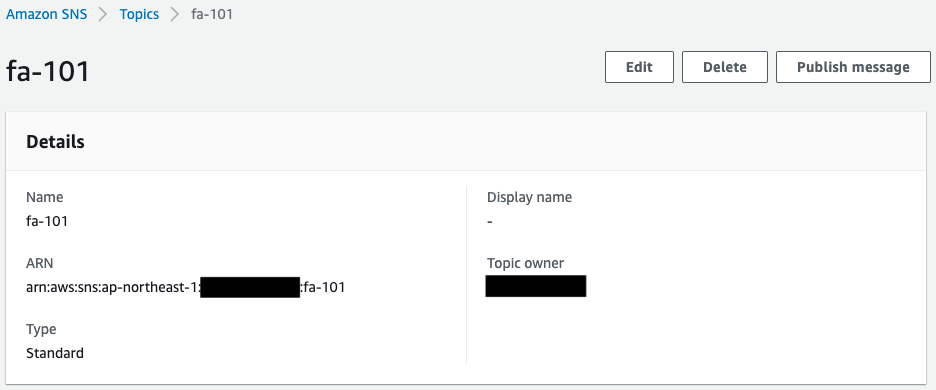
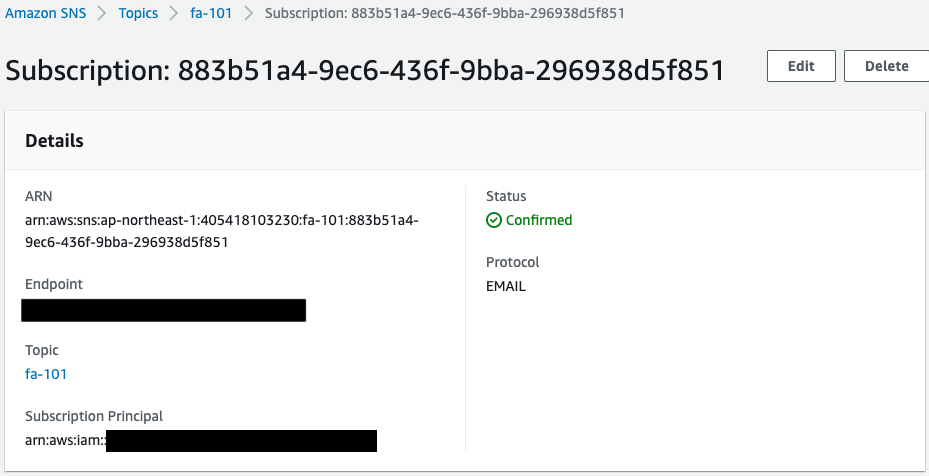
You can see that the SNS topic has been successfully created.
In addition, you can see that the email address you specified as a subscriber has been registered.
The Status value of the email address is “Confirmed,” indicating that the authentication has been completed.
Check the AWS Config settings.
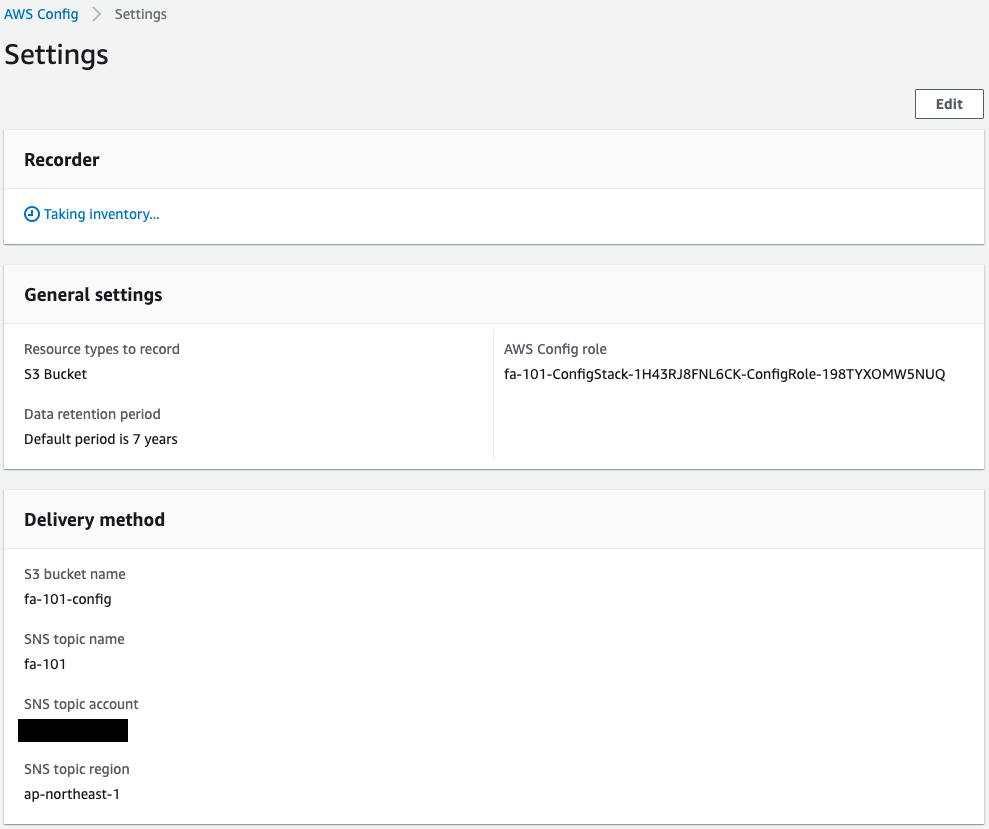
Looking at the SNS topic name in the Delivery method, the aforementioned SNS topic name can be confirmed.
Indeed, the SNS is associated with AWS Config.
Check the S3 bucket for verification.
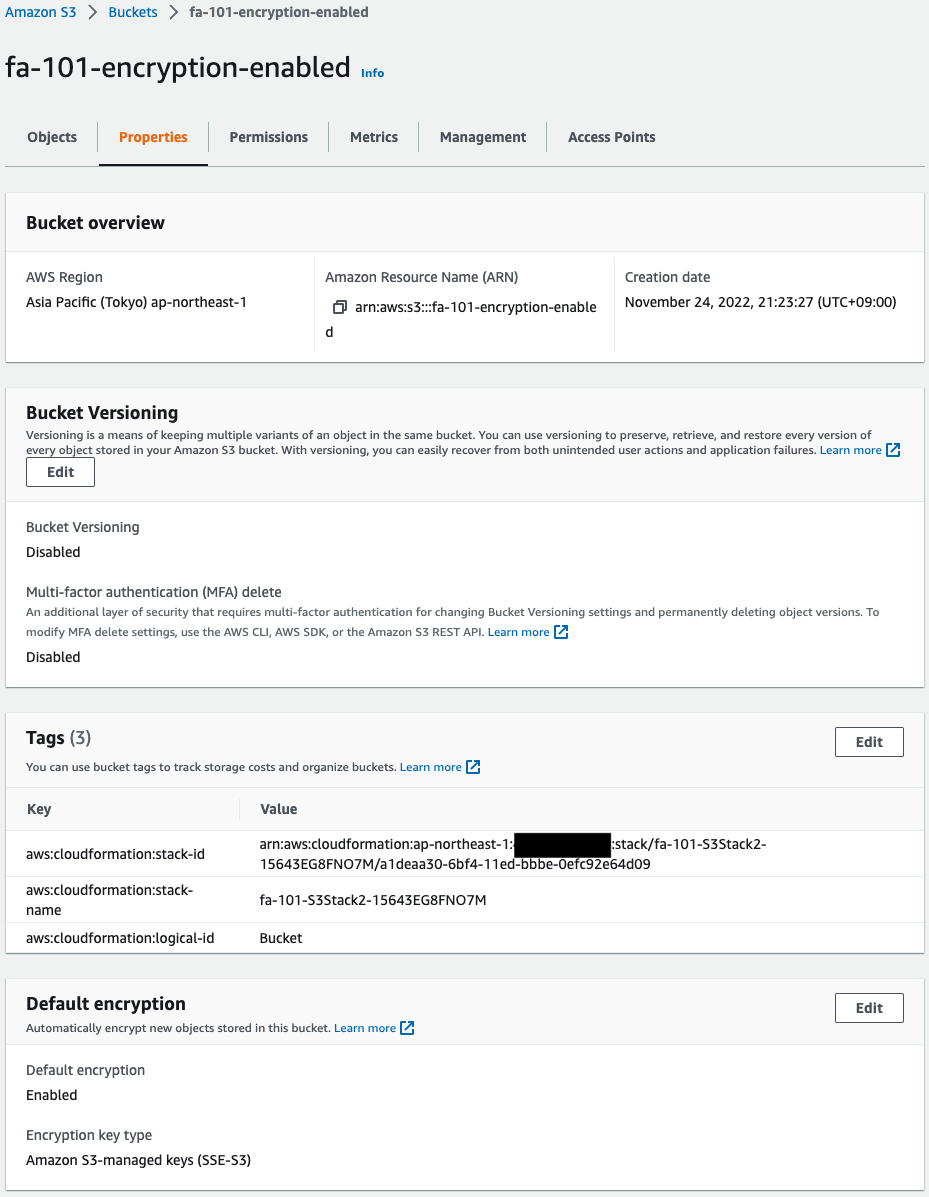
The S3 bucket is successfully created.
In particular, the Default encryption item shows that encryption is enabled.
Checking Operation
Now that everything is ready, checking the Operation.
Resource Creation
When the S3 bucket was created as described above, the following e-mail was sent to the e-mail address specified in the SNS topic.
The following image is a part of it.
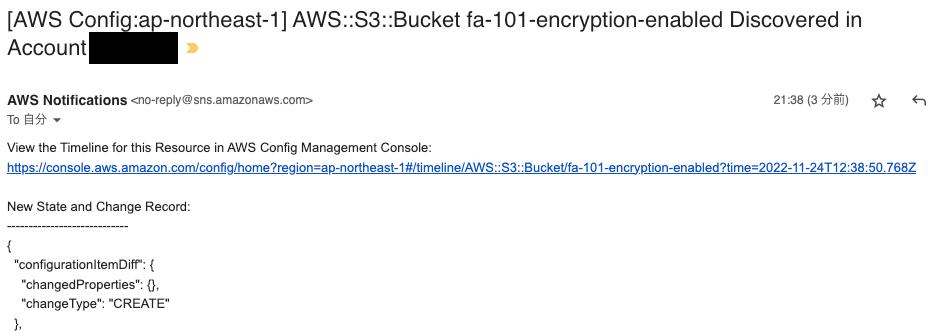
The following is a sample of the data.
{
"configurationItemDiff": {
"changedProperties": {},
"changeType": "CREATE"
},
"configurationItem": {
"relatedEvents": [],
"relationships": [],
"configuration": {
"name": "fa-101-encryption-enabled",
"owner": {
"displayName": null,
"id": "cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa"
},
"creationDate": "2022-11-24T12:36:41.000Z"
},
"supplementaryConfiguration": {
"AccessControlList": "{\"grantSet\":null,\"grantList\":[{\"grantee\":{\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\",\"displayName\":null},\"permission\":\"FullControl\"}],\"owner\":{\"displayName\":null,\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\"},\"isRequesterCharged\":false}",
"BucketAccelerateConfiguration": {
"status": null
},
"BucketLoggingConfiguration": {
"destinationBucketName": null,
"logFilePrefix": null
},
"BucketNotificationConfiguration": {
"configurations": {}
},
"BucketPolicy": {
"policyText": null
},
"BucketTaggingConfiguration": {
"tagSets": [
{
"tags": {
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09",
"aws:cloudformation:stack-name": "fa-101-S3Stack2-15643EG8FNO7M",
"aws:cloudformation:logical-id": "Bucket"
}
}
]
},
"BucketVersioningConfiguration": {
"status": "Off",
"isMfaDeleteEnabled": null
},
"IsRequesterPaysEnabled": false,
"ServerSideEncryptionConfiguration": {
"rules": [
{
"applyServerSideEncryptionByDefault": {
"sseAlgorithm": "AES256",
"kmsMasterKeyID": null
},
"bucketKeyEnabled": false
}
]
}
},
"tags": {
"aws:cloudformation:stack-name": "fa-101-S3Stack2-15643EG8FNO7M",
"aws:cloudformation:logical-id": "Bucket",
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09"
},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2022-11-24T12:38:50.768Z",
"configurationStateId": 1669293530768,
"awsAccountId": "[account-id]",
"configurationItemStatus": "ResourceDiscovered",
"resourceType": "AWS::S3::Bucket",
"resourceId": "fa-101-encryption-enabled",
"resourceName": "fa-101-encryption-enabled",
"ARN": "arn:aws:s3:::fa-101-encryption-enabled",
"awsRegion": "ap-northeast-1",
"availabilityZone": "Regional",
"configurationStateMd5Hash": "",
"resourceCreationTime": "2022-11-24T12:36:41.000Z"
},
"notificationCreationTime": "2022-11-24T12:38:50.832Z",
"messageType": "ConfigurationItemChangeNotification",
"recordVersion": "1.3"
}
Code language: JSON / JSON with Comments (json)The status of S3 bucket creation can be read.
You will also see the history of resource changes by AWS Config.
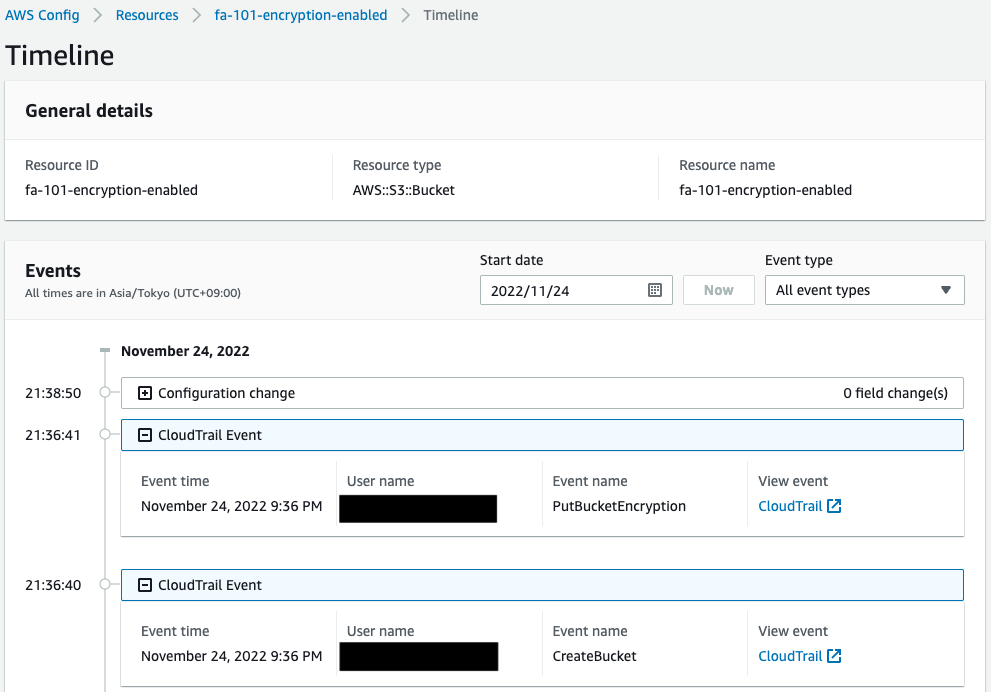
You can see that bucket creation (CreateBucket)) and encryption settings (PutBucketEncryption) were executed.
Changing Resource Settings
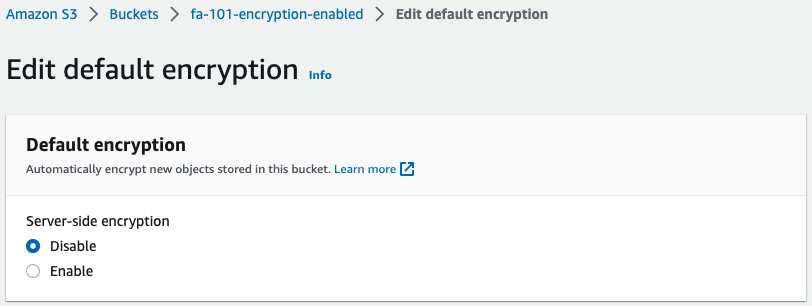
Next, we will change the settings of the S3 bucket and check the behavior of the bucket.
Specifically, disable bucket encryption.
After waiting for a while, we received the following email.
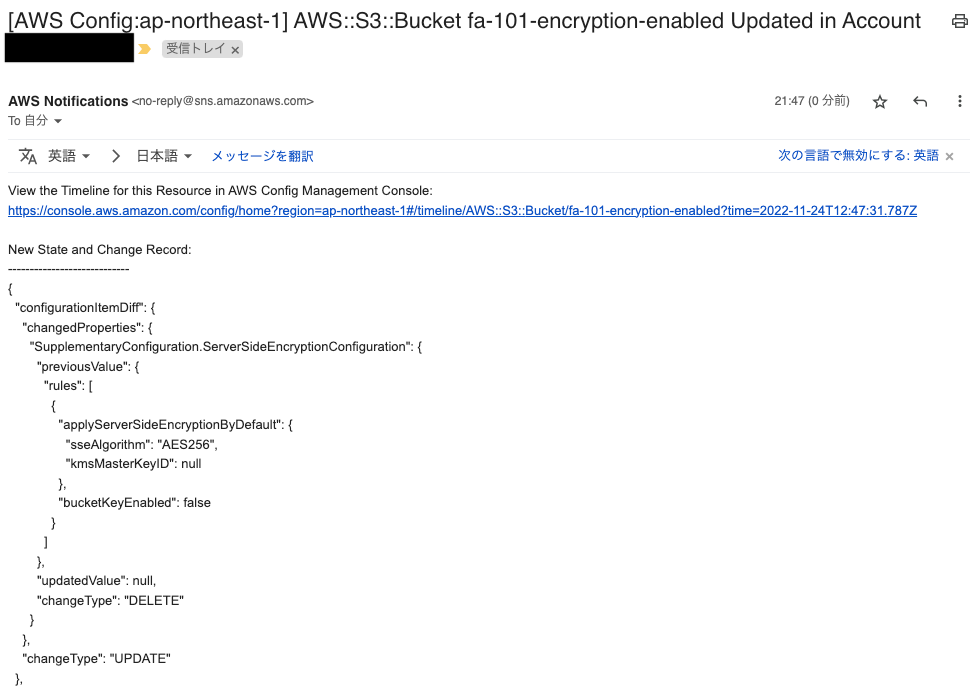
Here is the full contents
{
"configurationItemDiff": {
"changedProperties": {
"SupplementaryConfiguration.ServerSideEncryptionConfiguration": {
"previousValue": {
"rules": [
{
"applyServerSideEncryptionByDefault": {
"sseAlgorithm": "AES256",
"kmsMasterKeyID": null
},
"bucketKeyEnabled": false
}
]
},
"updatedValue": null,
"changeType": "DELETE"
}
},
"changeType": "UPDATE"
},
"configurationItem": {
"relatedEvents": [],
"relationships": [],
"configuration": {
"name": "fa-101-encryption-enabled",
"owner": {
"displayName": null,
"id": "cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa"
},
"creationDate": "2022-11-24T12:36:41.000Z"
},
"supplementaryConfiguration": {
"AccessControlList": "{\"grantSet\":null,\"grantList\":[{\"grantee\":{\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\",\"displayName\":null},\"permission\":\"FullControl\"}],\"owner\":{\"displayName\":null,\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\"},\"isRequesterCharged\":false}",
"BucketAccelerateConfiguration": {
"status": null
},
"BucketLoggingConfiguration": {
"destinationBucketName": null,
"logFilePrefix": null
},
"BucketNotificationConfiguration": {
"configurations": {}
},
"BucketPolicy": {
"policyText": null
},
"BucketTaggingConfiguration": {
"tagSets": [
{
"tags": {
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09",
"aws:cloudformation:stack-name": "fa-101-S3Stack2-15643EG8FNO7M",
"aws:cloudformation:logical-id": "Bucket"
}
}
]
},
"BucketVersioningConfiguration": {
"status": "Off",
"isMfaDeleteEnabled": null
},
"IsRequesterPaysEnabled": false
},
"tags": {
"aws:cloudformation:stack-name": "fa-101-S3Stack2-15643EG8FNO7M",
"aws:cloudformation:logical-id": "Bucket",
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09"
},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2022-11-24T12:47:31.787Z",
"configurationStateId": 1669294051787,
"awsAccountId": "[account-id]",
"configurationItemStatus": "OK",
"resourceType": "AWS::S3::Bucket",
"resourceId": "fa-101-encryption-enabled",
"resourceName": "fa-101-encryption-enabled",
"ARN": "arn:aws:s3:::fa-101-encryption-enabled",
"awsRegion": "ap-northeast-1",
"availabilityZone": "Regional",
"configurationStateMd5Hash": "",
"resourceCreationTime": "2022-11-24T12:36:41.000Z"
},
"notificationCreationTime": "2022-11-24T12:47:31.828Z",
"messageType": "ConfigurationItemChangeNotification",
"recordVersion": "1.3"
}
Code language: JSON / JSON with Comments (json)You can see that the update has removed settings related to encryption.
We also check the history of changes made to the resource by AWS Config.
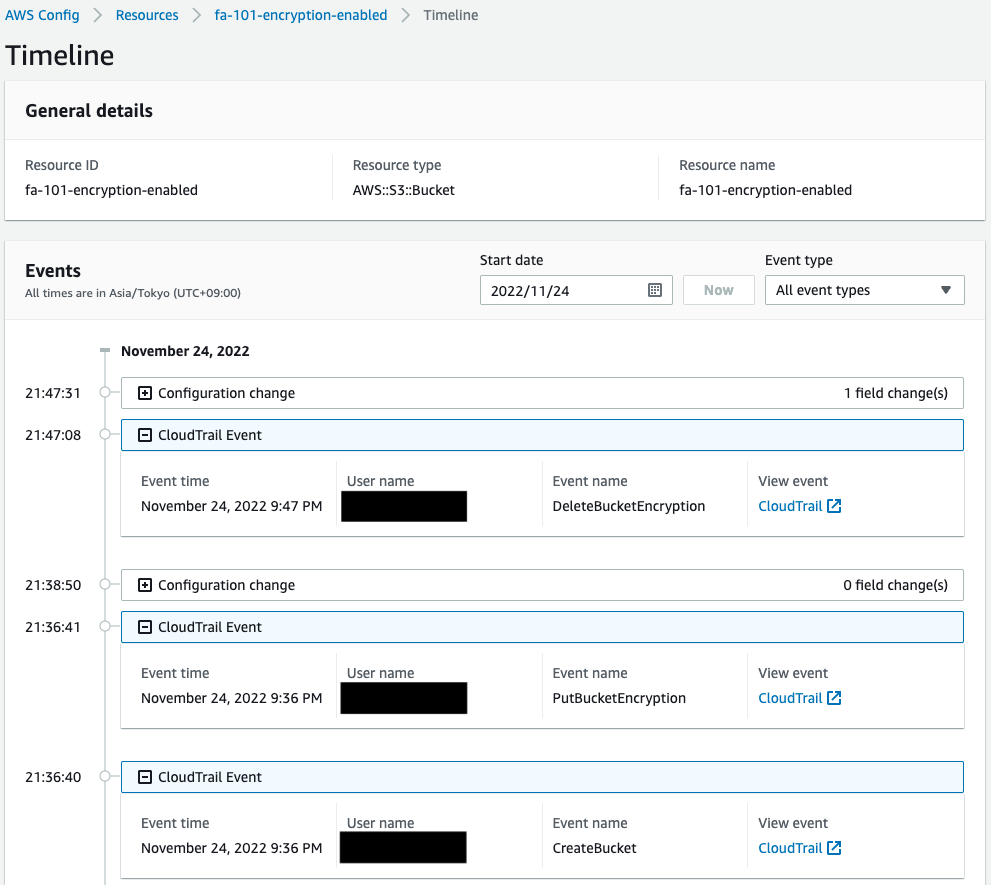
We can see that the encryption settings have been deleted (DeleteBucketEncryption).
Resource Deletion
After waiting for a while, we received the following email.
The following is the full contents
{
"configurationItemDiff": {
"changedProperties": {
"SupplementaryConfiguration.BucketAccelerateConfiguration": {
"previousValue": {
"status": null
},
"updatedValue": null,
"changeType": "DELETE"
},
"Tags.1": {
"previousValue": "Bucket",
"updatedValue": null,
"changeType": "DELETE"
},
"Tags.2": {
"previousValue": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09",
"updatedValue": null,
"changeType": "DELETE"
},
"Configuration": {
"previousValue": {
"name": "fa-101-encryption-enabled",
"owner": {
"displayName": null,
"id": "cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa"
},
"creationDate": "2022-11-24T12:36:41.000Z"
},
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.IsRequesterPaysEnabled": {
"previousValue": false,
"updatedValue": null,
"changeType": "DELETE"
},
"Tags.0": {
"previousValue": "fa-101-S3Stack2-15643EG8FNO7M",
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.BucketLoggingConfiguration": {
"previousValue": {
"destinationBucketName": null,
"logFilePrefix": null
},
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.BucketTaggingConfiguration": {
"previousValue": {
"tagSets": [
{
"tags": {
"aws:cloudformation:stack-id": "arn:aws:cloudformation:ap-northeast-1:[account-id]:stack/fa-101-S3Stack2-15643EG8FNO7M/a1deaa30-6bf4-11ed-bbbe-0efc92e64d09",
"aws:cloudformation:stack-name": "fa-101-S3Stack2-15643EG8FNO7M",
"aws:cloudformation:logical-id": "Bucket"
}
}
]
},
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.BucketPolicy": {
"previousValue": {
"policyText": null
},
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.BucketNotificationConfiguration": {
"previousValue": {
"configurations": {}
},
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.AccessControlList": {
"previousValue": "{\"grantSet\":null,\"grantList\":[{\"grantee\":{\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\",\"displayName\":null},\"permission\":\"FullControl\"}],\"owner\":{\"displayName\":null,\"id\":\"cd3b764ff044236dfe910b663c273b1f98dd3299f4d524a32909f70581c332fa\"},\"isRequesterCharged\":false}",
"updatedValue": null,
"changeType": "DELETE"
},
"SupplementaryConfiguration.BucketVersioningConfiguration": {
"previousValue": {
"status": "Off",
"isMfaDeleteEnabled": null
},
"updatedValue": null,
"changeType": "DELETE"
}
},
"changeType": "DELETE"
},
"configurationItem": {
"relatedEvents": [],
"relationships": [],
"configuration": null,
"supplementaryConfiguration": {},
"tags": {},
"configurationItemVersion": "1.3",
"configurationItemCaptureTime": "2022-11-24T12:58:58.374Z",
"configurationStateId": 1669294738374,
"awsAccountId": "[account-id]",
"configurationItemStatus": "ResourceDeleted",
"resourceType": "AWS::S3::Bucket",
"resourceId": "fa-101-encryption-enabled",
"resourceName": "fa-101-encryption-enabled",
"ARN": "arn:aws:s3:::fa-101-encryption-enabled",
"awsRegion": "ap-northeast-1",
"availabilityZone": null,
"configurationStateMd5Hash": "",
"resourceCreationTime": null
},
"notificationCreationTime": "2022-11-24T12:58:58.422Z",
"messageType": "ConfigurationItemChangeNotification",
"recordVersion": "1.3"
}
Code language: JSON / JSON with Comments (json)You can see that the bucket has been deleted.
We also check the history of resource changes by AWS Config.
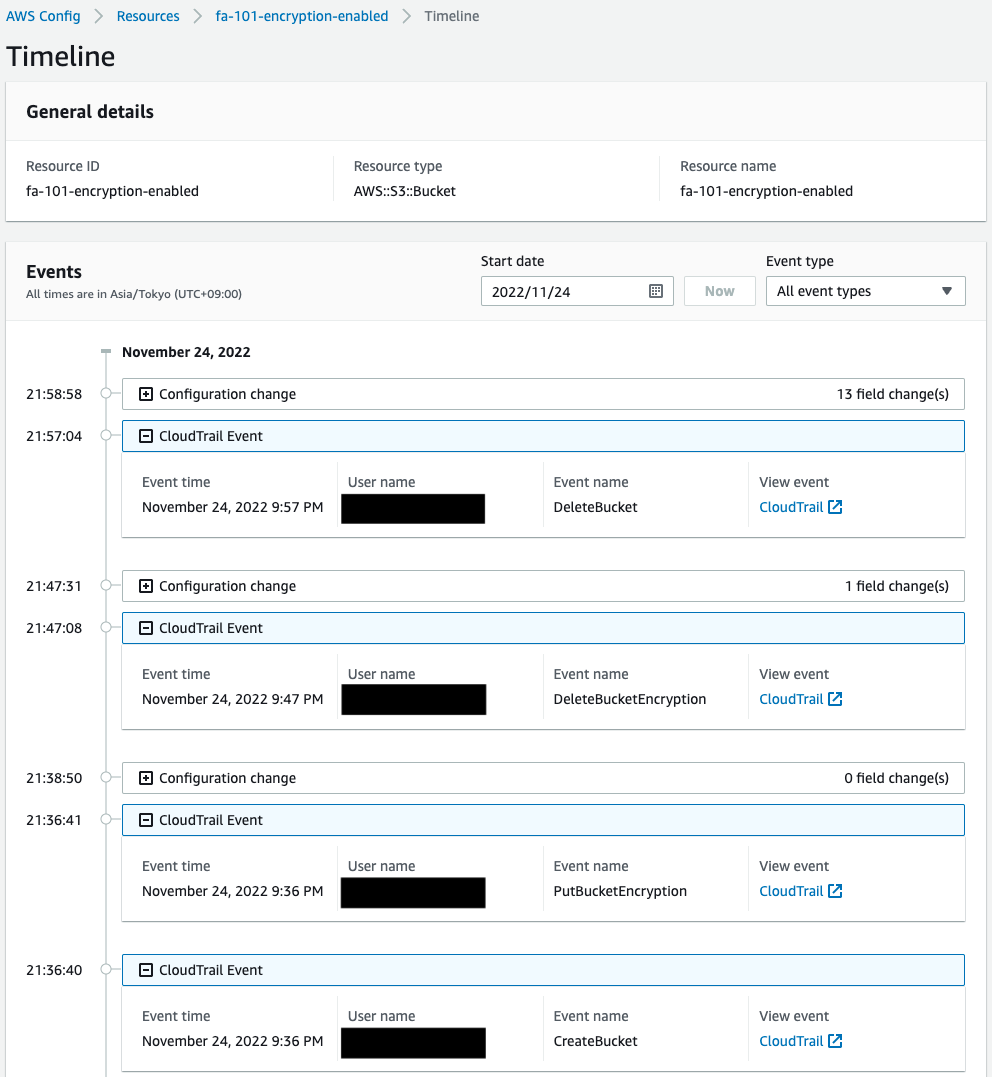
You can see that the bucket deletion (DeleteBucket) was executed.
By associating SNS with AWS Config, you can be notified by e-mail when a resource is changed.
Summary
We have confirmed how to send email notifications via SNS when a resource is changed.