Email notification via SNS when Nocompliant resources are detected by AWS Config
The following page covers how EventBridge receives event data sent out from AWS Config and only those that match the rules are notified via email by SNS.

A similar configuration can be used to send email notifications via SNS when a resource is detected in an AWS Config audit that does not comply with the rules.
Specifically, the following official AWS page covers how to set this up
https://aws.amazon.com/premiumsupport/knowledge-center/config-resource-non-compliant/?nc1=h_ls
This time, the above configuration will be built using CloudFormation.
Specifically, we will set up rules regarding SSE for S3 buckets in AWS Config, and configure the system to send an email notification when a bucket that does not conform to these rules is detected.
Environment
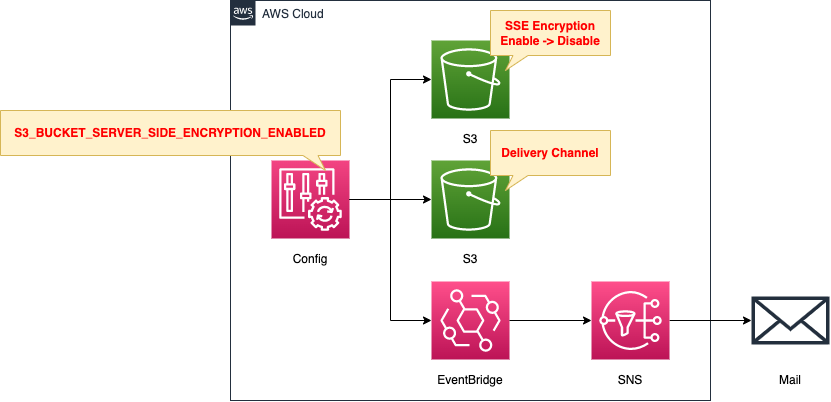
The configuration is generally the same as in the page introduced at the beginning of this page.
Create rules for SSE for S3 buckets in AWS Config.
When an S3 bucket with SSE disabled is detected, event data will be generated as a non-compliant resource.
If the EventBridge rule receives data that satisfies the above, it sends the data to the SNS topic.
Specify an email address as a subscriber to the SNS topic and email notification will be sent.
CloudFormation Template Files
The above configuration is built with CloudFormation.
The CloudFormation templates are located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/104
Explanation of key points of the template files
Basically, it is the same as the page introduced at the beginning of this document, so only the different parts will be covered.
AWS Config Rules
Resources:
S3BucketSSEEnabledConfigRule:
Type: AWS::Config::ConfigRule
DependsOn:
- ConfigurationRecorder
Properties:
ConfigRuleName: !Sub "${Prefix}-S3-Bucket-SSE-Enabled"
Scope:
ComplianceResourceTypes:
- AWS::S3::Bucket
Source:
Owner: AWS
SourceIdentifier: S3_BUCKET_SERVER_SIDE_ENCRYPTION_ENABLED
Code language: YAML (yaml)Configure the rules regarding SSE for the S3 bucket.
In this case, we will use the managed rule “s3-bucket-server-side-encryption-enabled”.
Specify this rule in the Source property.
For more information about AWS Config rules, please also check the following page

EventBridge Rules
Resources:
EventsRule:
Type: AWS::Events::Rule
Properties:
EventBusName: !Ref EventBusName
EventPattern:
source:
- aws.config
detail-type:
- Config Rules Compliance Change
detail:
messageType:
- ComplianceChangeNotification
configRuleName:
- !Ref S3BucketSSEEnabledConfigRule
resourceType:
- AWS::S3::Bucket
newEvaluationResult:
complianceType:
- NON_COMPLIANT
Name: !Sub "${Prefix}-EventsRule"
State: ENABLED
Targets:
- Arn: !Ref TopicArn
Id: !Ref TopicName
InputTransformer:
InputPathsMap:
"awsRegion": "$.detail.awsRegion"
"resourceId": "$.detail.resourceId"
"awsAccountId": "$.detail.awsAccountId"
"compliance": "$.detail.newEvaluationResult.complianceType"
"rule": "$.detail.configRuleName"
"time": "$.detail.newEvaluationResult.resultRecordedTime"
"resourceType": "$.detail.resourceType"
InputTemplate: |
"On <time> AWS Config rule <rule> evaluated the <resourceType> with Id <resourceId> in the account <awsAccountId> region <awsRegion> as <compliance> For more details open the AWS Config console at https://console.aws.amazon.com/config/home?region=<awsRegion>#/timeline/<resourceType>/<resourceId>/configuration"
Code language: YAML (yaml)When a resource is determined to be non-compliant by an AWS Config rule, data is sent to EventBridge.
Create an EventBridge rule for SSE in the S3 bucket and configure it to send a message to the SNS topic when the event is received.
There are two points.
The first is the EventPattern property.
Specify the data pattern that will be generated when the S3 bucket is judged as non-compliant with the rules regarding SSE.
Set as described in the official AWS page.
https://aws.amazon.com/premiumsupport/knowledge-center/config-resource-non-compliant/?nc1=h_ls
The following is a sample of data.
{
"version": "0",
"id": "e1127974-86dd-69bb-649a-1416eaa3a14a",
"detail-type": "Config Rules Compliance Change",
"source": "aws.config",
"account": "[account-id]",
"time": "2022-12-02T14:39:46Z",
"region": "ap-northeast-1",
"resources": [],
"detail": {
"resourceId": "fa-104-encryption-enabled",
"awsRegion": "ap-northeast-1",
"awsAccountId": "[account-id]",
"configRuleName": "fa-104-S3-Bucket-SSE-Enabled",
"recordVersion": "1.0",
"configRuleARN": "arn:aws:config:ap-northeast-1:[account-id]:config-rule/config-rule-yt5uxw",
"messageType": "ComplianceChangeNotification",
"newEvaluationResult": {
"evaluationResultIdentifier": {
"evaluationResultQualifier": {
"configRuleName": "fa-104-S3-Bucket-SSE-Enabled",
"resourceType": "AWS::S3::Bucket",
"resourceId": "fa-104-encryption-enabled"
},
"orderingTimestamp": "2022-12-02T14:39:32.966Z"
},
"complianceType": "NON_COMPLIANT",
"resultRecordedTime": "2022-12-02T14:39:45.721Z",
"configRuleInvokedTime": "2022-12-02T14:39:45.437Z"
},
"oldEvaluationResult": {
"evaluationResultIdentifier": {
"evaluationResultQualifier": {
"configRuleName": "fa-104-S3-Bucket-SSE-Enabled",
"resourceType": "AWS::S3::Bucket",
"resourceId": "fa-104-encryption-enabled"
},
"orderingTimestamp": "2022-12-02T14:33:12.486Z"
},
"complianceType": "COMPLIANT",
"resultRecordedTime": "2022-12-02T14:38:39.897Z",
"configRuleInvokedTime": "2022-12-02T14:38:29.554Z"
},
"notificationCreationTime": "2022-12-02T14:39:46.796Z",
"resourceType": "AWS::S3::Bucket"
}
}
Code language: JSON / JSON with Comments (json)The second point is the Targets property.
This specifies the SNS topic.
By default, the message to be published to the SNS topic is the JSON data shown above.
The message can be specified by setting the InputTransformer property.
This is also set as described on the official AWS page.
Architecting
Using CloudFormation, build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- SNS topic: fa-104
- AWS Config rule: fa-104-S3-Bucket-SSE-Enabled
- EventBridge rule: fa-104-EventRule
- Validation bucket: fa-104-encryption-enabled
Authentication of email addresses
If an email address is specified as a subscriber to an SNS topic, the email address must be authenticated.
The following authentication email will be sent to the specified email address.
Click “Confirm subscription” to proceed with the authentication.
The above page will appear, indicating that the authentication is complete.
Resource Confirmation
Check each resource from the AWS Management Console.
First, check the SNS topic.
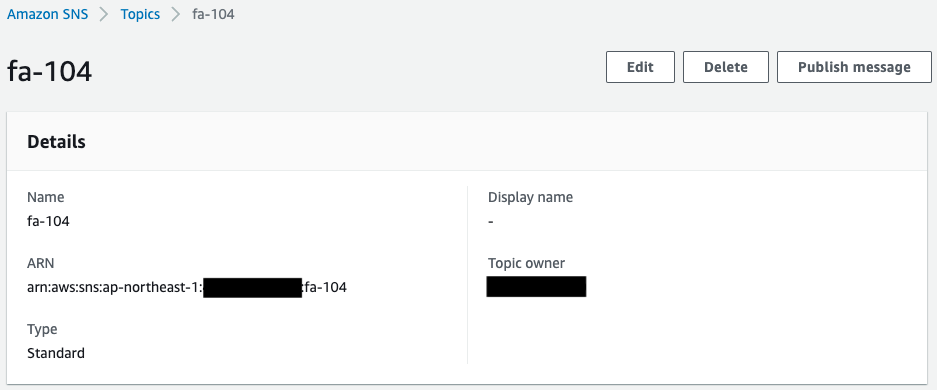
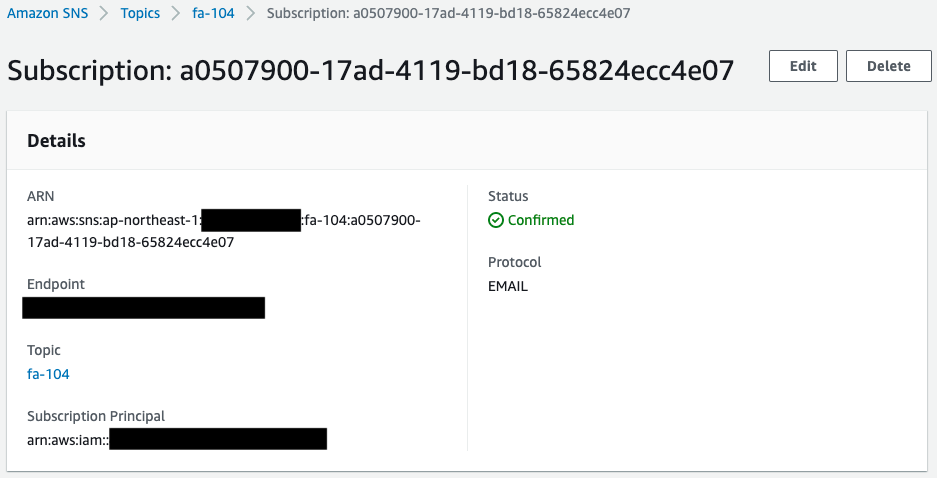
You can see that the SNS topic has been successfully created.
In addition, you can see that the email address you registered as a subscriber is registered.
The Status value of the email address is “Confirmed,” indicating that the authentication has been completed.
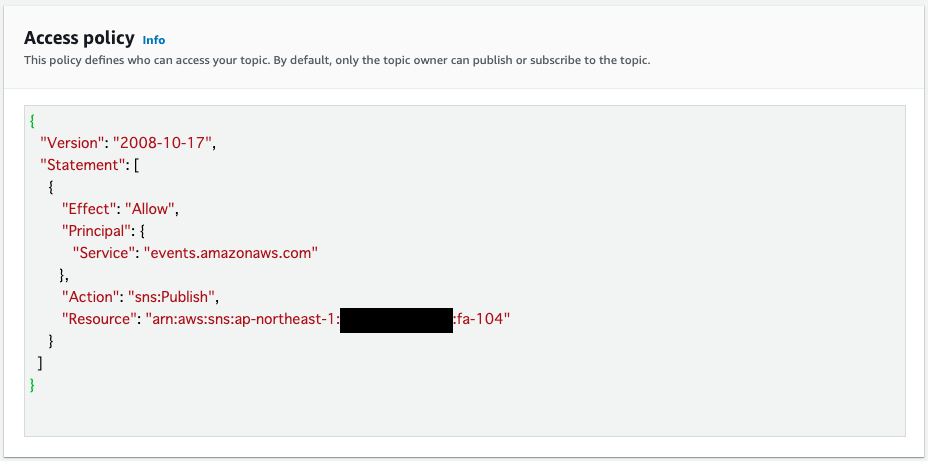
The access policy shows that EventBridge is allowed to publish messages to this topic.
Check the S3 bucket for verification.
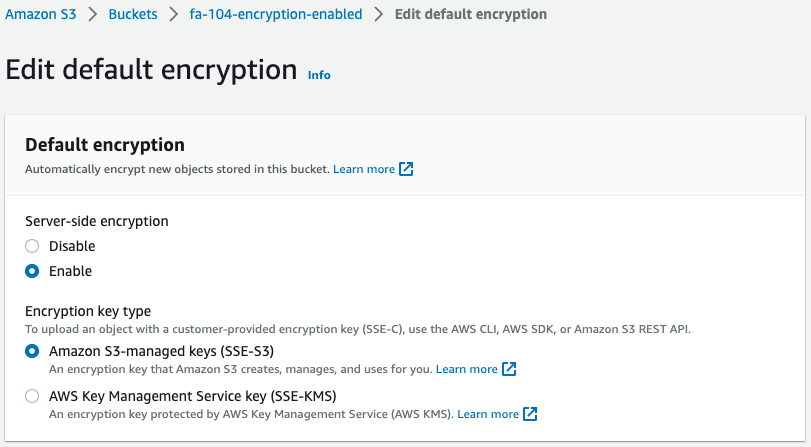
We see that SSE is indeed enabled.
Check the AWS Config settings.
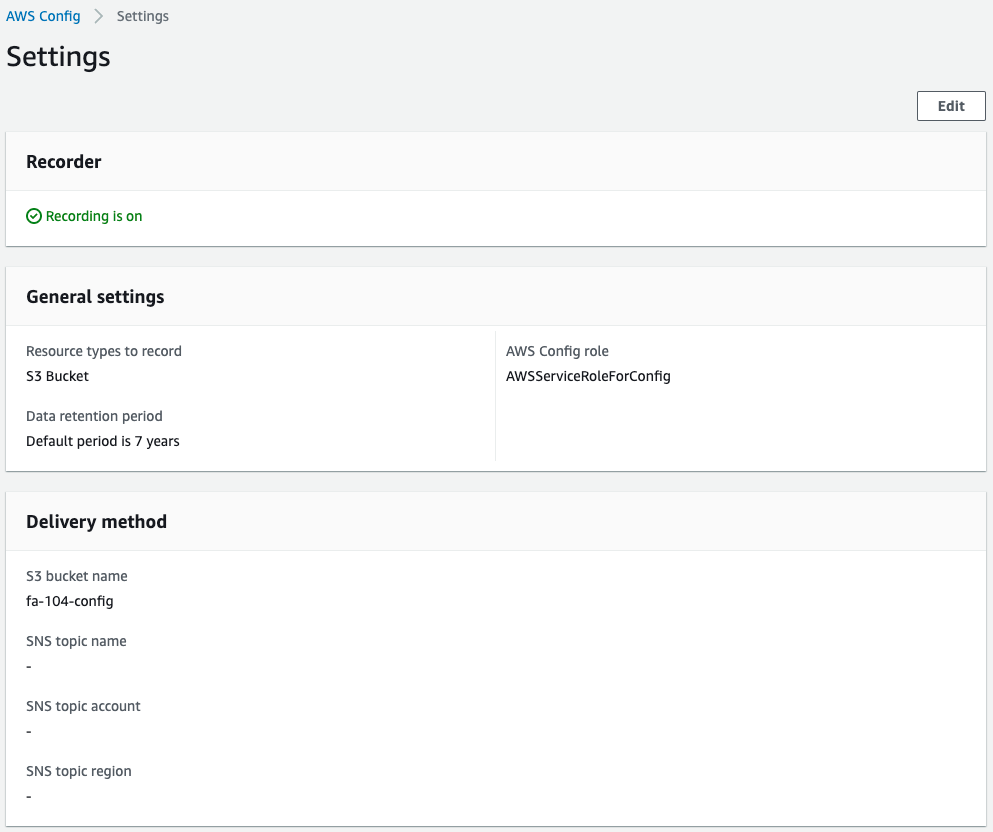
We can see that AWS Config is acting correctly and has started collecting data.
Check the AWS Config rules.
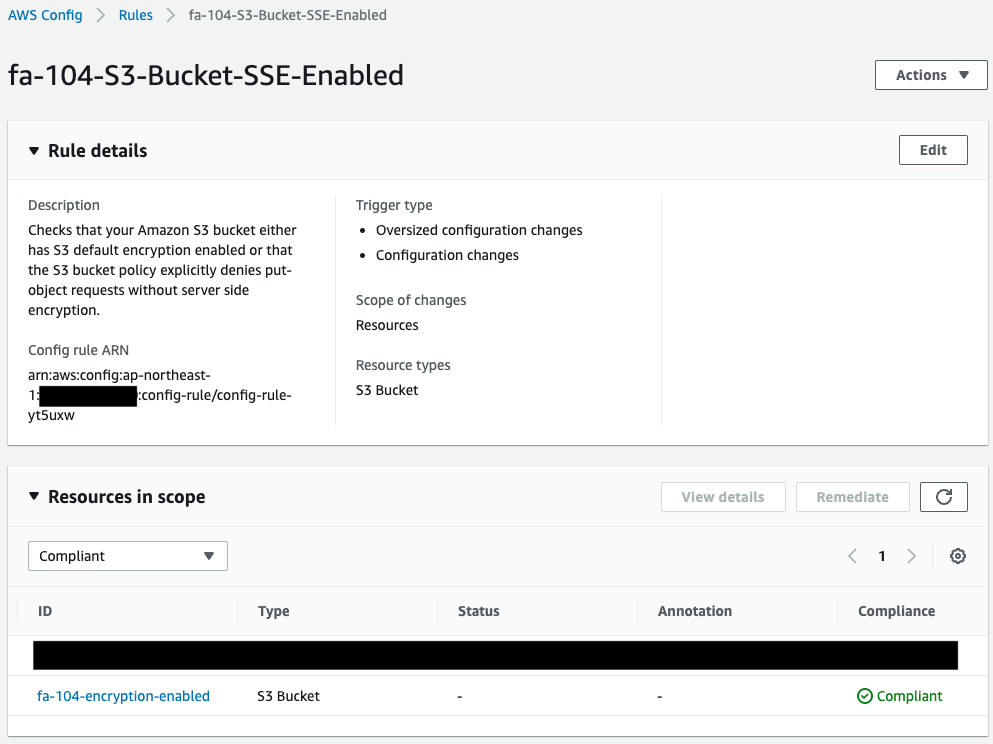
We can see that the rules for SSE have been created.
And if we look at the S3 bucket mentioned above, we see that it is “Compliant”, so we know that it is now compliant.
Check the EventBridge rule.
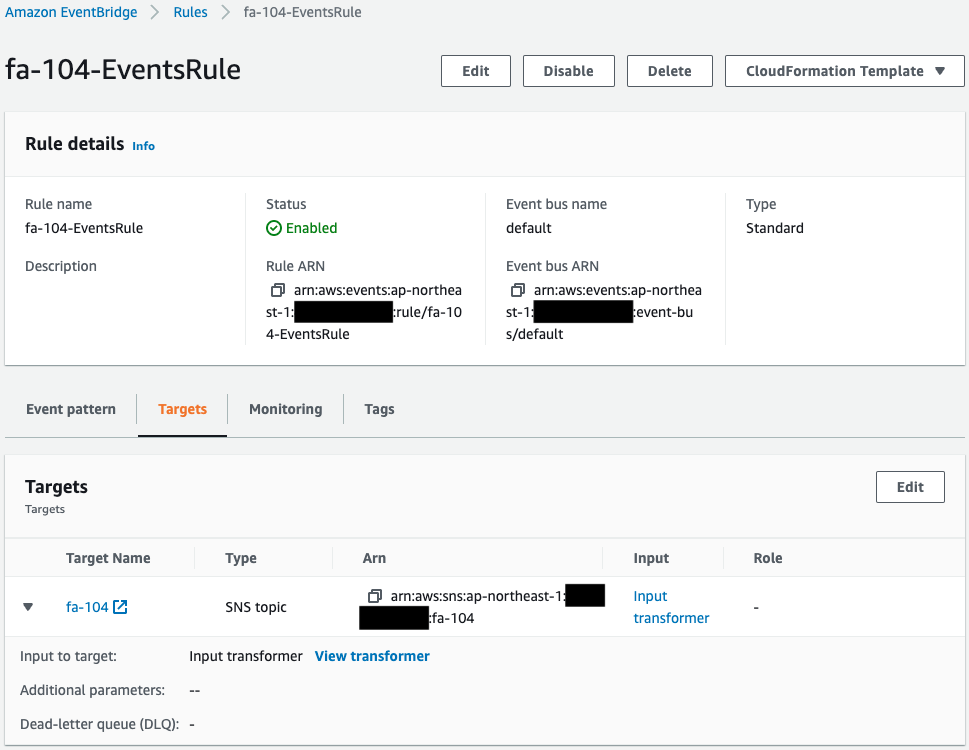
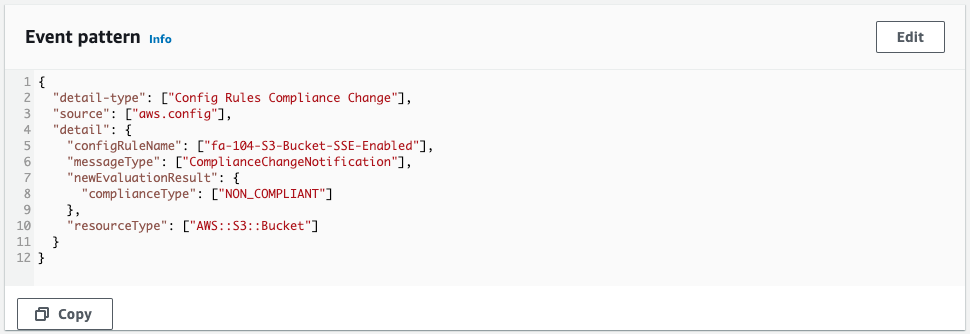
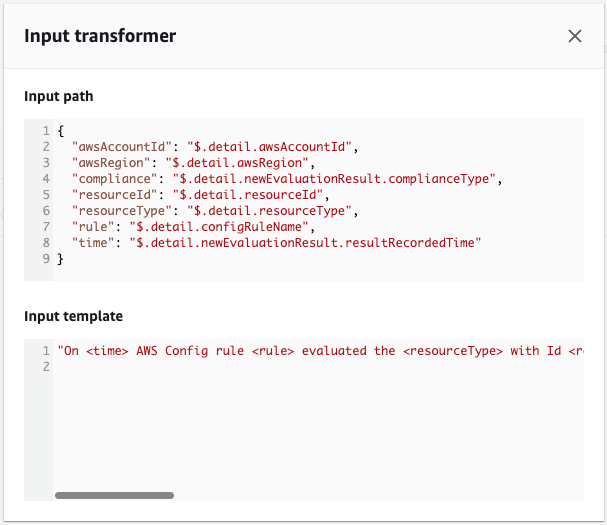
We can see that the EventBridge rule has been successfully created.
Looking at Target, we can see that the SNS topic mentioned earlier is specified.
This means that when event data that satisfies the pattern is sent, it will be notified via email by SNS.
The Event Pattern shows that the pattern is defined as per the CloudFormation template.
This means that if a resource is detected that does not conform to the AWS Config rules for SSE configuration of S3 buckets, it will satisfy the condition.
Looking at the Input transformer, we see that a template for the string to be sent by email and the parameters to be embedded are defined.
Checking Action
Now that everything is ready, let’s check the Operation.
Disable the SSE settings for the S3 bucket.
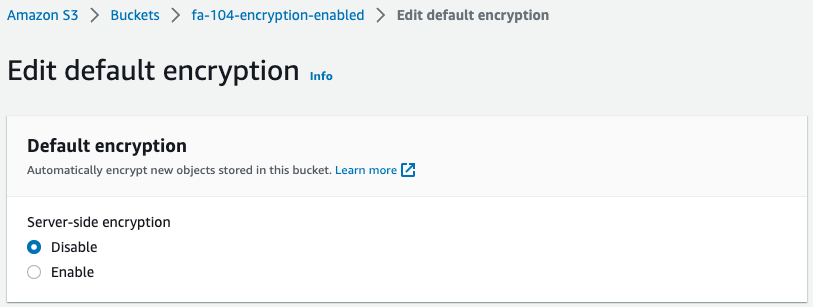
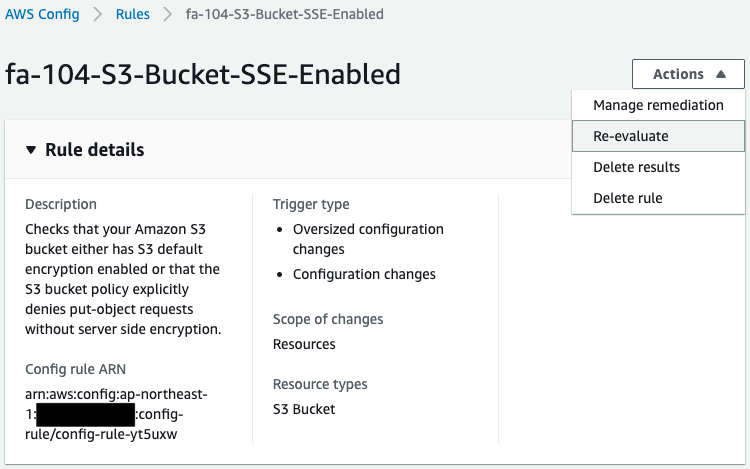
After disabling, re-evaluate the rules on the AWS Config side.
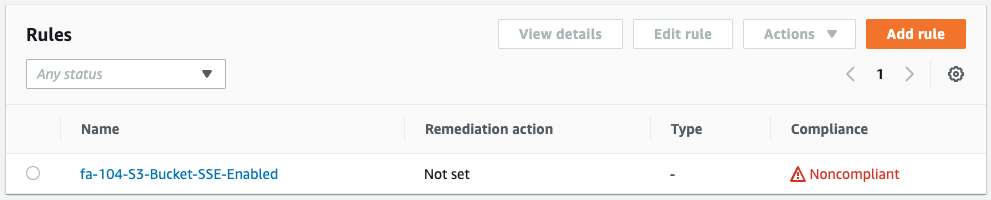
The rules are re-evaluated and the bucket for verification is now “Nocompliant.
After waiting for a while, the following email was received.

The body of the email is indeed a string with various parameters embedded in the template specified in the Input Transformer.
By configuring the EventBridge rule in this way, we were able to send an email notification via SNS when a resource that does not conform to AWS Config rules is detected.
Summary
We have introduced a method to send email notifications via SNS when a non-compliant resource is detected in an AWS Config audit.