Configure remediation actions when non-compliant resources are detected by AWS Config
One of the topics covered in AWS SOA is monitoring, logging, and remediation.
AWS Config allows you to define remediation actions.
AWS Config allows you to remediate noncompliant resources that are evaluated by AWS Config Rules.
Remediating Noncompliant Resources with AWS Config Rules
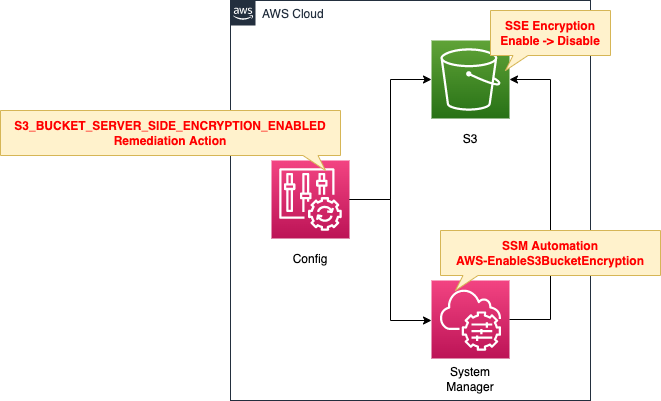
This time, we will define AWS Config rules and repair actions for SSE on S3 buckets and check the actual behavior.
Environment
Create an S3 bucket with SSE enabled for verification.
In AWS Config, create rules regarding SSE and remediation actions for the S3 bucket.
When an S3 bucket with SSE disabled is detected and determined to be non-compliant, it will be automatically restored.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation templates are located at the following URL
https://github.com/awstut-an-r/awstut-soa/tree/main/01/001
Explanation of key points of the template files
This page focuses on the contents related to AWS Config remediation actions.
For basic information about AWS Config, please refer to the following page

AWS Config Rules
Resources:
S3BucketSSEEnabledConfigRule:
Type: AWS::Config::ConfigRule
DependsOn:
- ConfigurationRecorder
Properties:
ConfigRuleName: !Sub "${Prefix}-S3-Bucket-SSE-Enabled"
Scope:
ComplianceResourceId: !Ref TestBucket
ComplianceResourceTypes:
- AWS::S3::Bucket
Source:
Owner: AWS
SourceIdentifier: S3_BUCKET_SERVER_SIDE_ENCRYPTION_ENABLED
Code language: YAML (yaml)Define rules for SSE of S3 buckets.
In this case, we will limit the resources to be audited for verification purposes.
In the Scope property, specify the bucket name in the ComplianceResourceId property and “AWS::S3::Bucket” in the ComplianceResourceTypes property to make only the bucket for verification subject to the rule.
AWS Config remediation actions
Resources:
RemediationConfiguration:
Type: AWS::Config::RemediationConfiguration
Properties:
Automatic: true
ConfigRuleName: !Ref S3BucketSSEEnabledConfigRule
MaximumAutomaticAttempts: 5
Parameters:
BucketName:
ResourceValue:
Value: RESOURCE_ID
SSEAlgorithm:
StaticValue:
Values:
- !Ref SSEAlgorithm
AutomationAssumeRole:
StaticValue:
Values:
- !GetAtt RemediationConfigurationRole.Arn
ResourceType: AWS::S3::Bucket
RetryAttemptSeconds: 60
TargetId: AWS-EnableS3BucketEncryption
TargetType: SSM_DOCUMENT
TargetVersion: "1"
Code language: YAML (yaml)Remediation actions are accomplished through the use of SSM Automation documentation.
AWS Config applies remediation using AWS Systems Manager Automation documents. These documents define the actions to be performed on noncompliant AWS resources evaluated by AWS Config Rules.
Remediating Noncompliant Resources with AWS Config Rules
We will cover the characteristic parameters.
The Automatic property is a parameter that sets whether or not the remediation action will be performed automatically.
you can either choose to manually or automatically remediate noncompliant resources by associating remediation actions with AWS Config rules. With all remediation actions, you can either choose manual or automatic remediation.
Remediating Noncompliant Resources with AWS Config Rules
In this case, we will specify “true” to automatically execute the remediation action.
The TargetId, TargetType, and TargetVersion properties are parameters related to the document to be executed.
This time we will enable SSE for S3 buckets by running the managed document AWS-EnableS3BucketEncryption.
You can find more information about this document on the following page
The MaximumAutomaticAttempts property is a parameter that specifies the maximum number of automatic repair failures.
In this case, we will set it to the default value of 5 times.
The RetryAttemptSeconds property is a parameter that specifies the maximum time to perform an automatic repair.
This time it is set to the default value of 60 seconds.
The Parameters property is the parameter to pass when executing the document.
As indicated in the page above, the following three parameters must be specified to run this document
- BucketName
- SSEAlgorithm
- AutomationAssumeRole
Set these parameters in the Parameters property.
The key point is whether the value specified for each parameter is dynamic or static.
For example, BucketName is a dynamic value because it varies for each bucket that is determined to be non-compliant by the audit.
For a dynamic value, use the ResourceValue property and specify “RESOURCE_ID” in the internal Value property.
On the other hand, SSEAlgorithm and AutomationAssumeRole are static values.
The former specifies the default value “AES256” and the latter specifies a fixed IAM role as described below.
In this case, use the StaticValue property and set the value to the internal Values property.
The IAM role is used to grant SSM Automation the necessary privileges for remediation actions.
Resources:
RemediationConfigurationRole:
Type: AWS::IAM::Role
DeletionPolicy: Delete
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
Service:
- ssm.amazonaws.com
Policies:
- PolicyName: S3PutSSEPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- s3:PutEncryptionConfiguration
Resource:
- !Sub "arn:aws:s3:::${TestBucket}"
Code language: YAML (yaml)This time, we will give permission to enable SSE settings for the verification bucket.
Architecting
Using CloudFormation, we will build this environment and verify the actual behavior.
Create CloudFormation stacks and verify resources in stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- AWS Config rule: soa-01-001-S3-Bucket-SSE-Enabled
- Bucket for verification: soa-01-001-encryption-enabled
Check each resource from the AWS Management Console.
First, check the AWS Config rules.
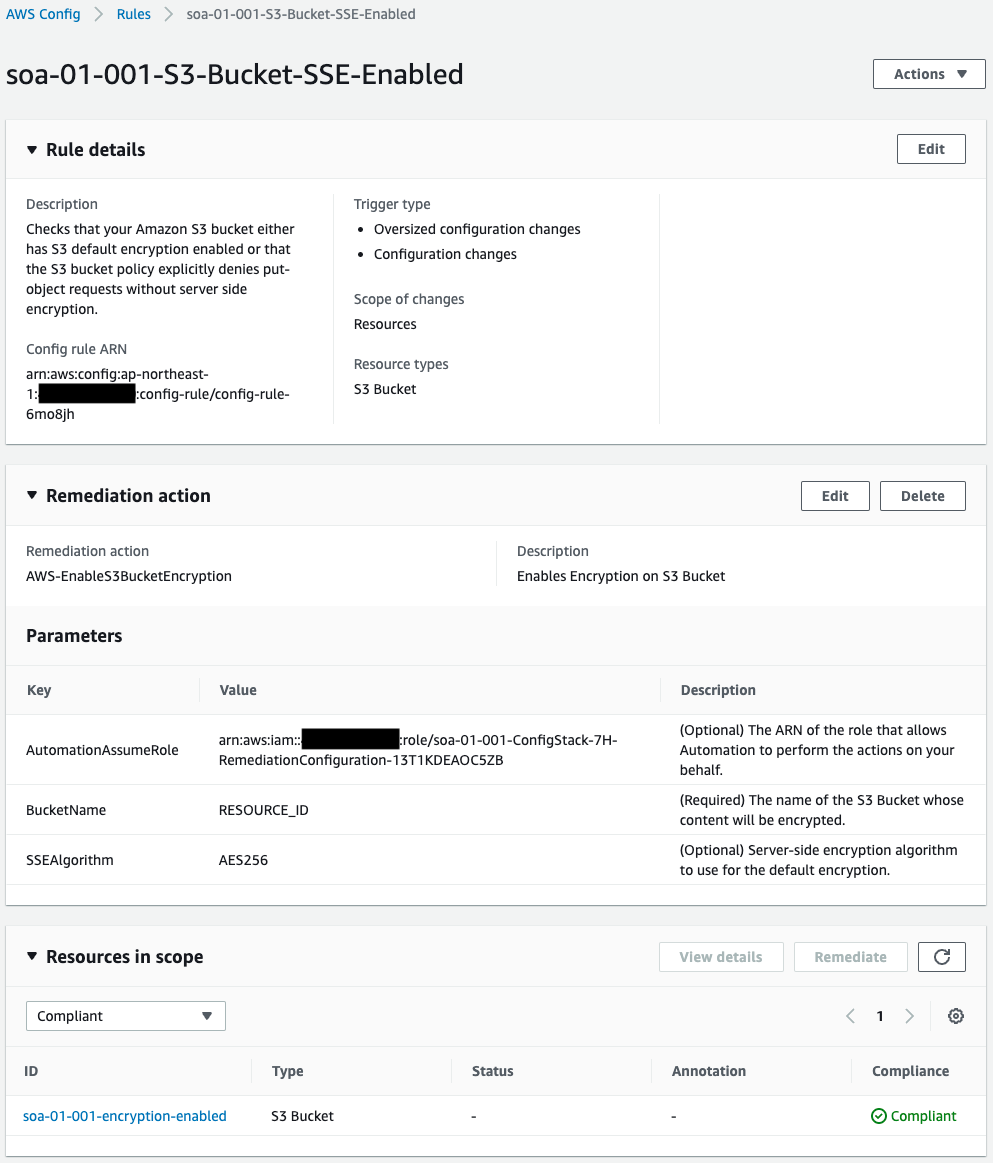
We can see that the rule has been successfully created.
The audit based on the rule also shows that the validation bucket is “Compliant”.
The remediation action is defined and the SSM document AWS-EnableS3BucketEncryption and parameters for document execution are specified.
If SSE is disabled for the validation bucket and the audit results show that it is non-compliant, this document will be executed as the remediation action.
Check the validation bucket.
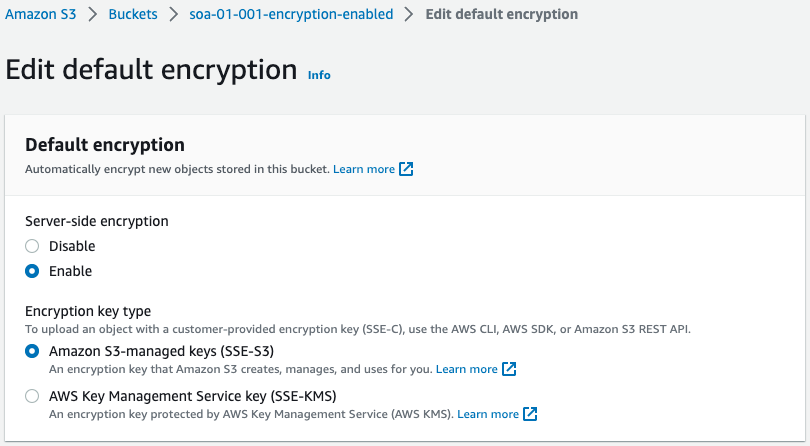
You can see that SSE is indeed enabled.
Checking Action
Now that everything is ready, let’s check the action.
Disable the SSE setting for the S3 bucket.
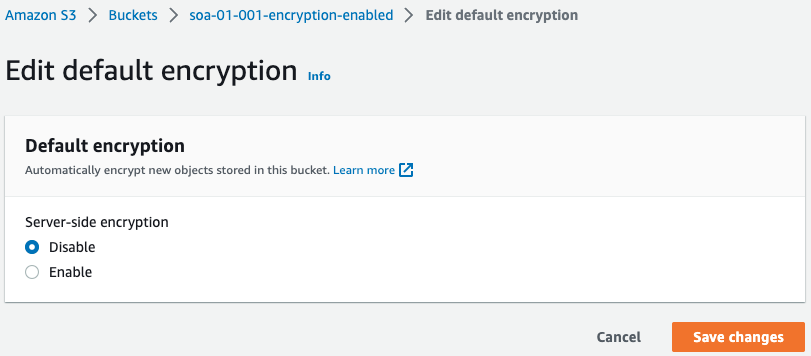
SSE has been disabled.
The AWS Config evaluation is changed.
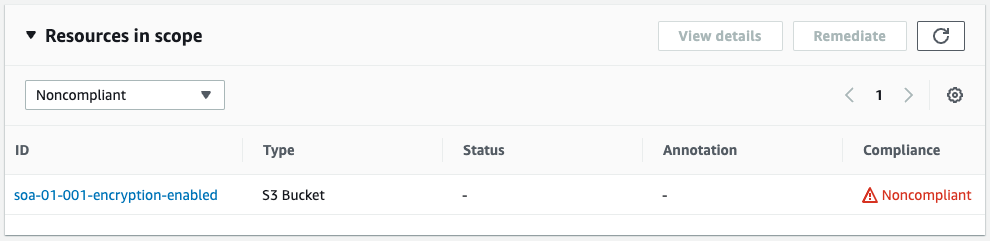
It was “Compliant” earlier, but it changed to “Nocompliant” after SSE was disabled.
Check SSM Automation.
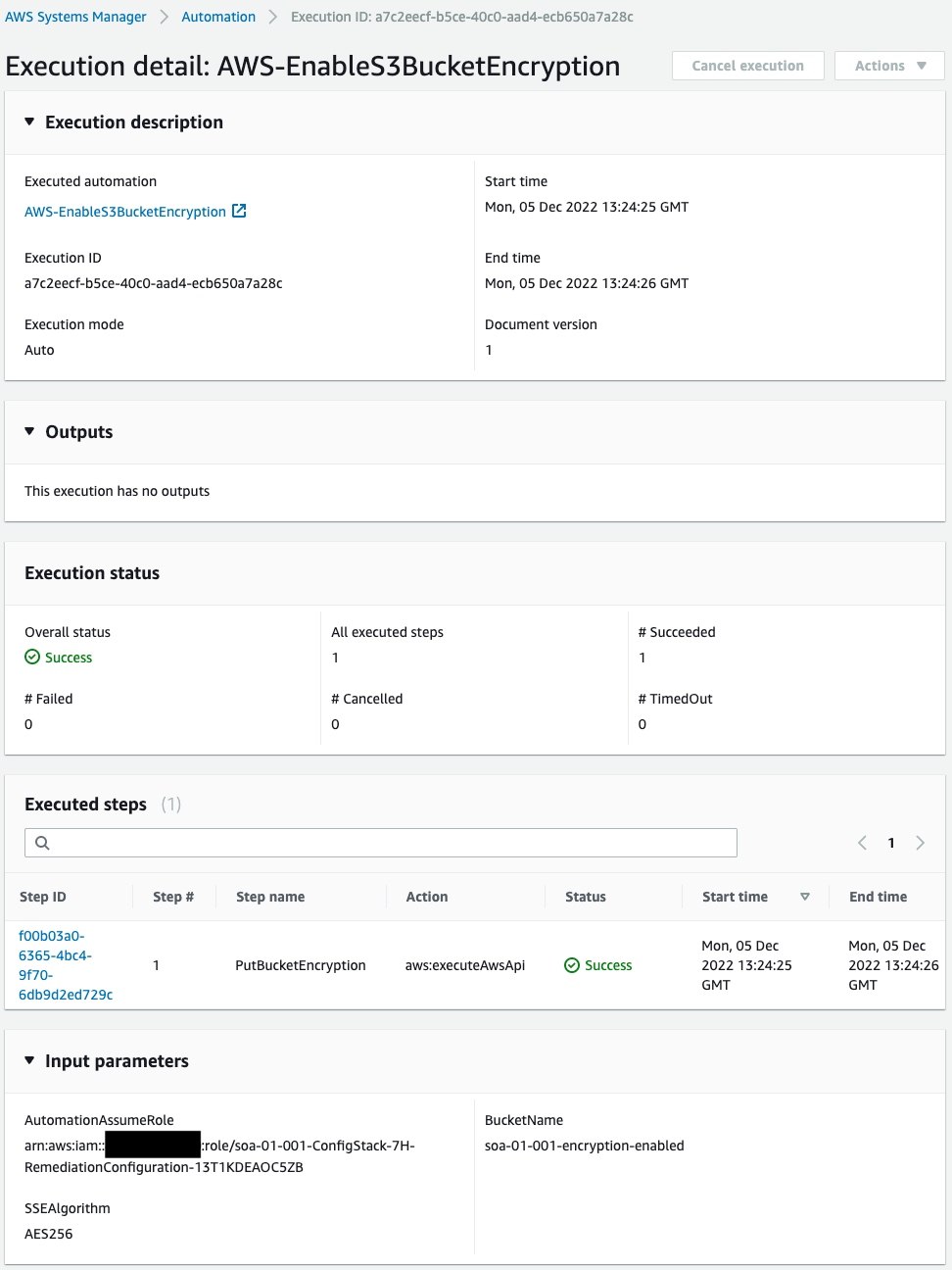
SSM Automation has indeed been executed.
SSM Automation executed the SSM document AWS-EnableS3BucketEncryption and we can see that it completed successfully.
We will check the AWS Config rules and S3 bucket again.
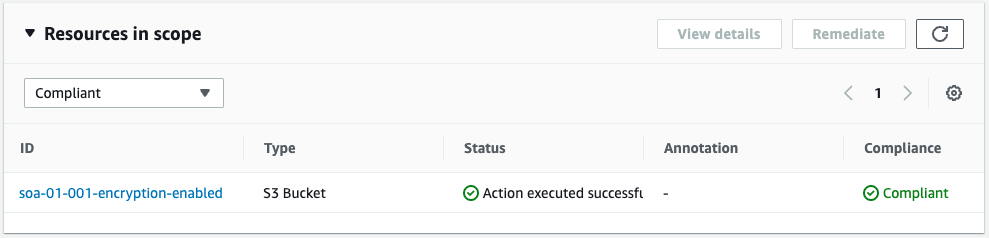
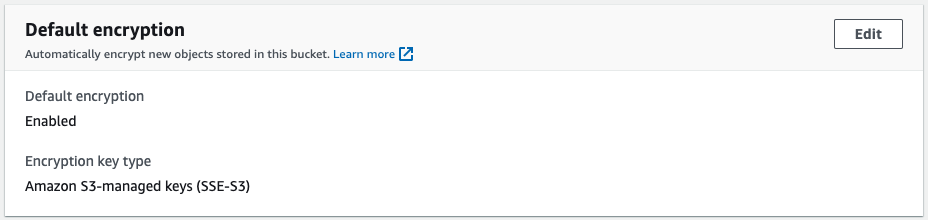
On the AWS Config rules page, we are back to “Compliant” again.
And on the S3 Buckets page, we can see that SSE has been enabled again.
This indicates that SSM Automation has executed the SSM document and enabled the SSE feature for the S3 bucket.
Summary
We have seen how to automatically recover a resource by defining a remediation action in AWS Config rules.