Delegate access privileges between AWS accounts using cross-account roles
Accessing a specific AWS resource from another AWS account is called cross-account access.
You share resources in one account with users in a different account. By setting up cross-account access in this way, you don’t have to create individual IAM users in each account.
IAM tutorial: Delegate access across AWS accounts using IAM roles
This page will review the cross-account access procedures with reference to the following page.
https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-account-with-roles.html
Environment
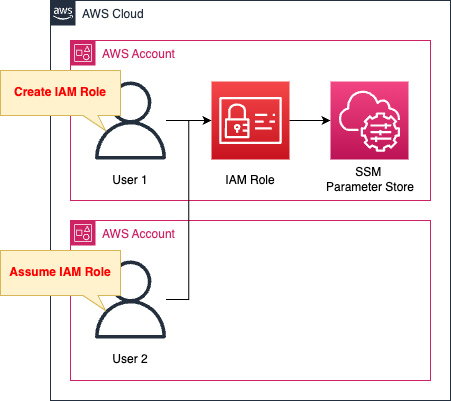
Two AWS accounts will be used.
The first account will create two resources.
The first will create parameters in the SSM parameter store.
The second creates an IAM role.
This IAM role has permissions to access the SSM parameter store as described above.
The second account assumes this IAM role.
After assuming the role, verify that the SSM parameter store is accessible.
CloudFormation template files
The above configuration is built using CloudFormation.
We have placed the CloudFormation templatse at the following URL
https://github.com/awstut-an-r/awstut-dva/tree/main/02/002
Explanation of key points of the template files
(Reference) SSM Parameter Store
Resources:
Parameter:
Type: AWS::SSM::Parameter
Properties:
Name: !Sub "${Prefix}-Parameter"
Type: String
Value: Test Parameter
Code language: YAML (yaml)Create an SSM parameter as a resource for verification.
No special configuration is required.
IAM Role
Resources:
SSMParameterRole:
Type: AWS::IAM::Role
DeletionPolicy: Delete
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
AWS: !Ref CrossAccountId
Policies:
- PolicyName: !Sub "${Prefix}-GetParameterPolicy"
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- ssm:DescribeParameters
Resource: "*"
- Effect: Allow
Action:
- ssm:GetParameter
Resource:
- !Sub "arn:aws:ssm:${AWS::Region}:${AWS::AccountId}:parameter/${Parameter}"
Code language: YAML (yaml)The key point is the trust policy.
The Principal property specifies the ID of the account with cross account access.
The inline policy defines access privileges to the SSM parameter store.
The following page was used as a reference to set this up.
https://docs.aws.amazon.com/systems-manager/latest/userguide/sysman-paramstore-access.html
Architecting
Use CloudFormation to build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- SSM Parameter: dva-02-002-Parameter
- IAM role: dva-02-002-IAMStack-3A259XLV4A28-SSMParameterRole-1E0267AH90Z9O
Check each resource from the AWS Management Console.
Check the SSM parameters.
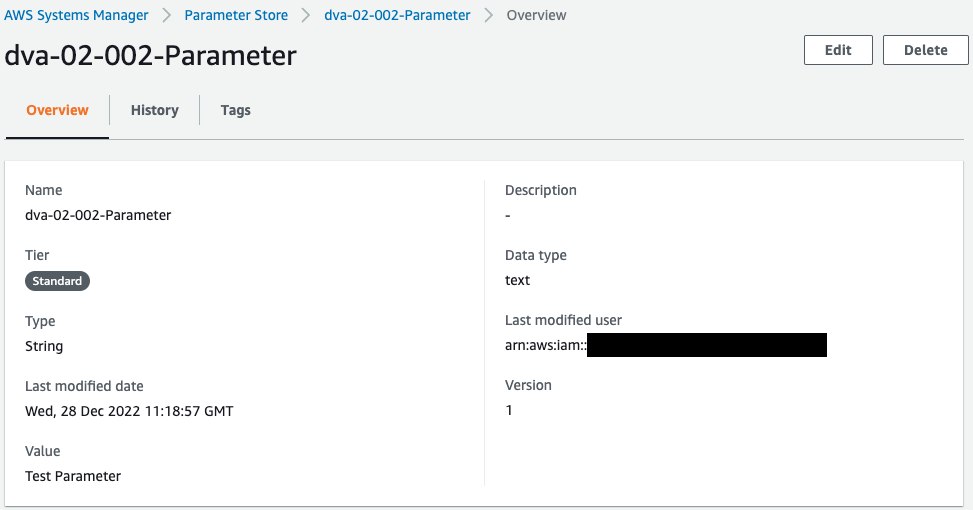
Parameters are indeed created.
Check the IAM role.
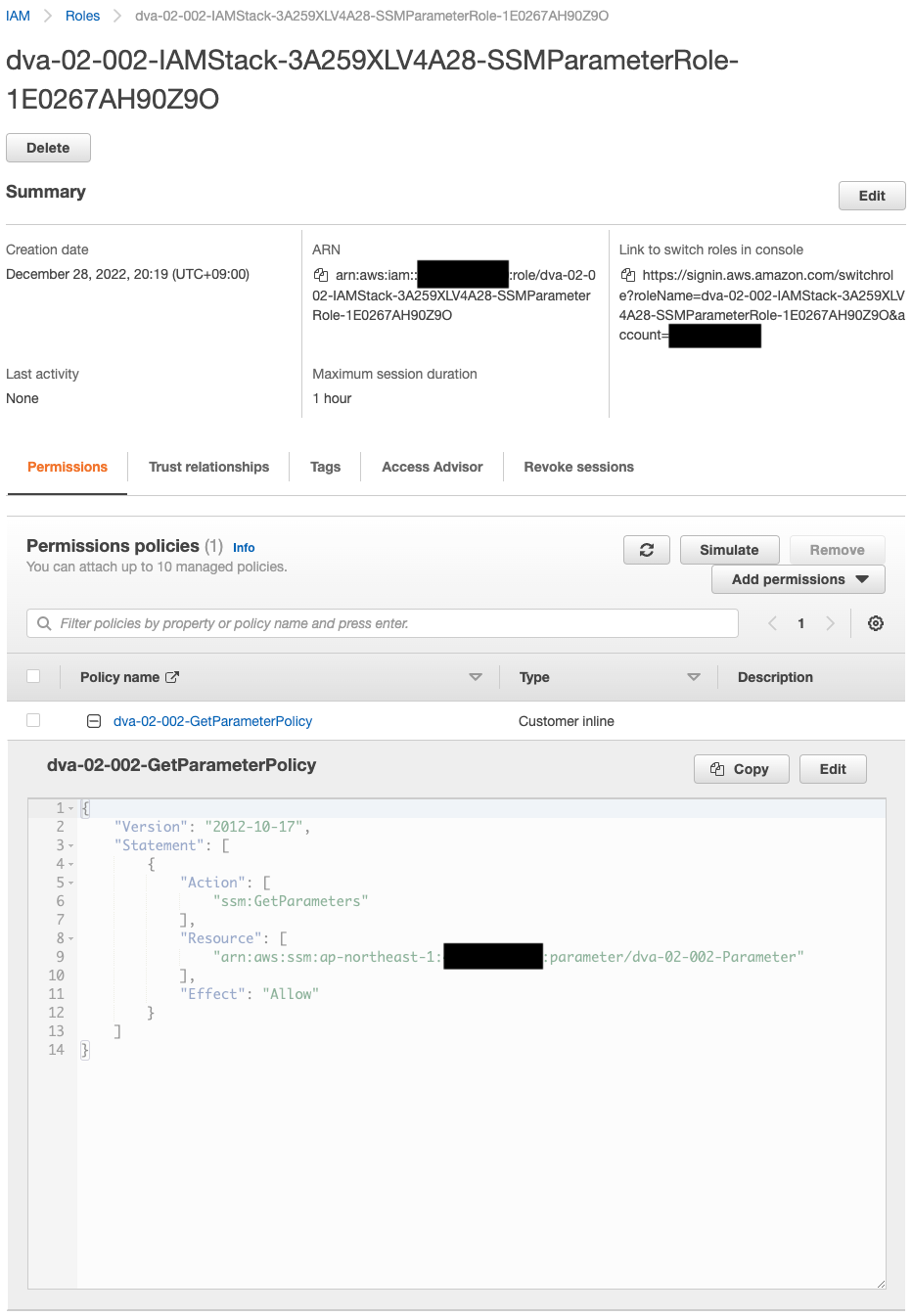
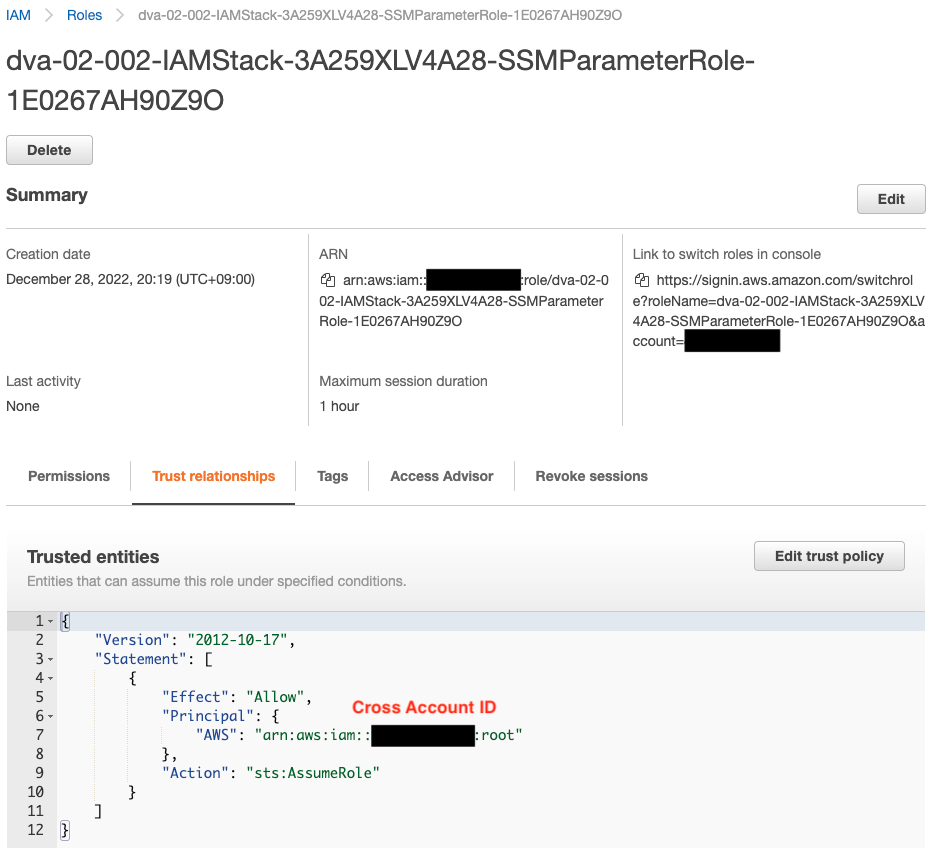
Looking at the permissions, we see that permissions are set to access the SSM parameters mentioned above.
Looking at the trust relationship, the ID of the account with cross account access (the root user of the account) is set as the principal.
Checking Action
Now that everything is ready, we can perform cross-account access.
Open the management console of the account to be cross accessed and click “Switch role”.
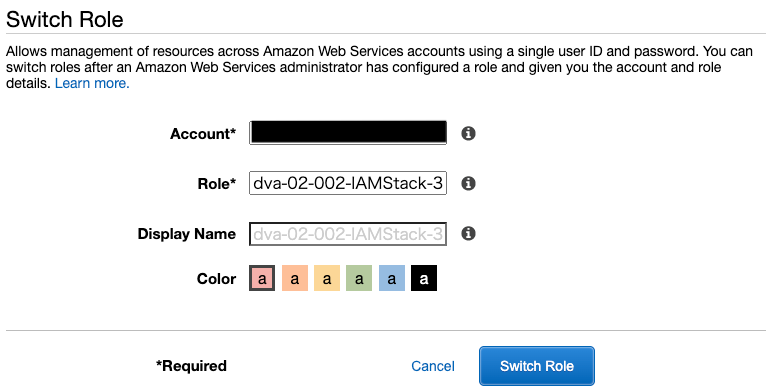
Enter the information of the role to be assumed and click “Switch Role”.
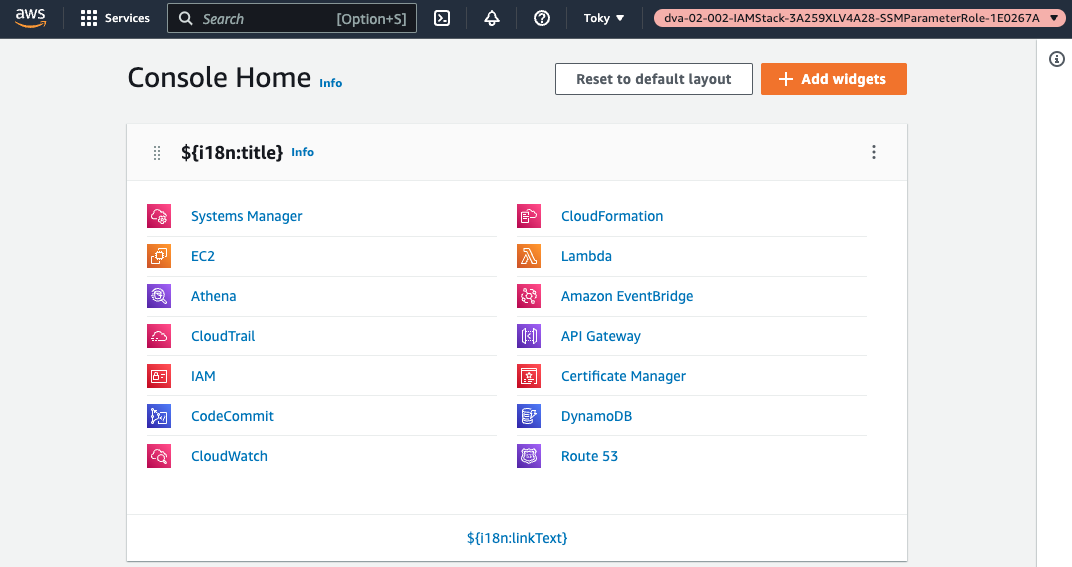
If the role is successfully assumed, the role will be displayed in the upper right corner.
Open the EC2 page as a test.
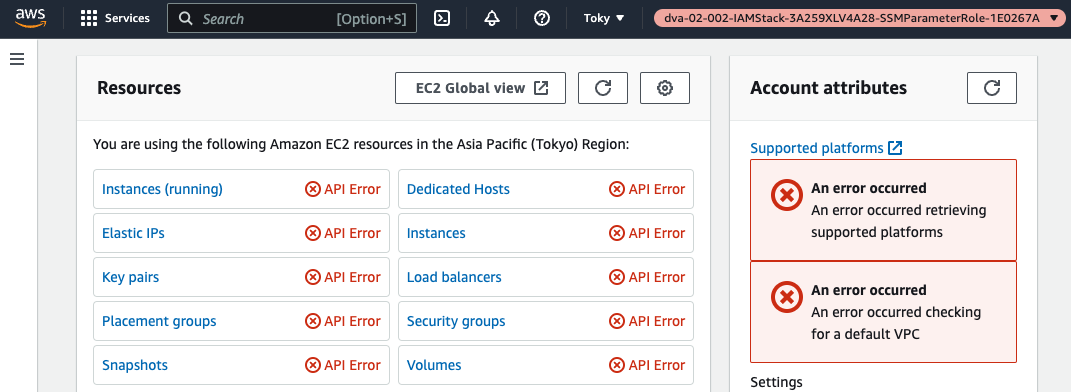
Errors are displayed in all fields.
This is because the currently assumed role does not allow permissions on EC2.
Check the SSM parameter store again.
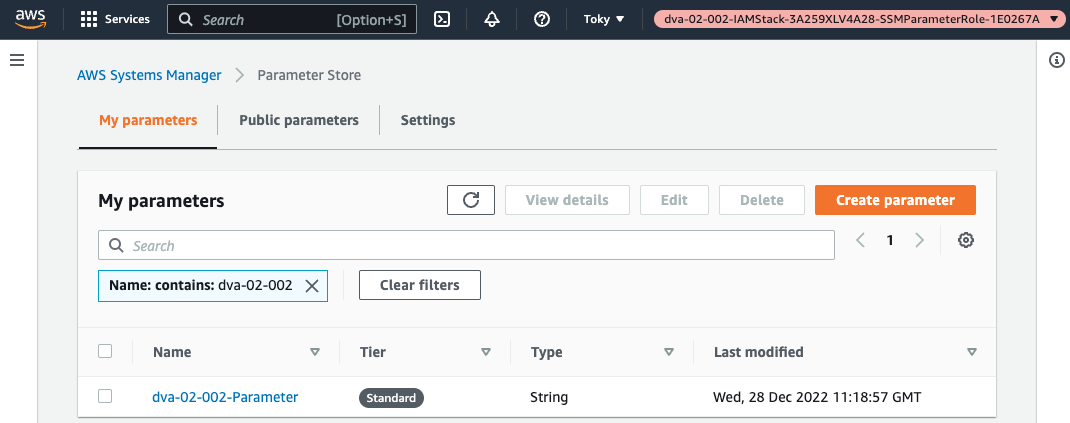
The parameters we just checked are now displayed.
Check the details.
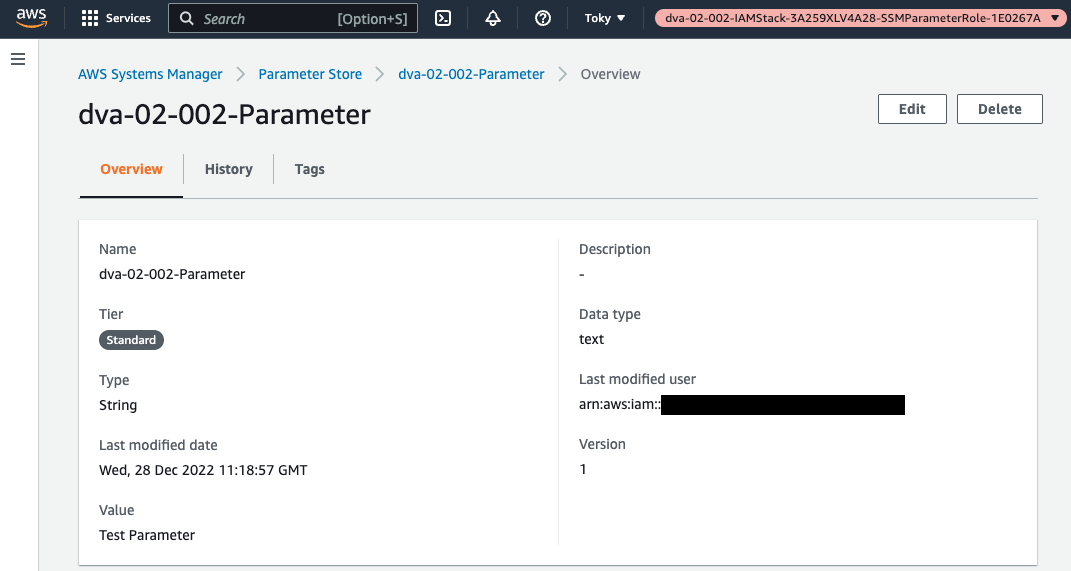
You can also check the value of the parameter.
By assuming a cross-account role in this way, you can access the resources of another account.
Summary
We have seen how to delegate access privileges between AWS accounts using cross-account roles.