Email notification via SNS when error occurs in CodePipeline
The content is related to monitoring and troubleshooting, which is also part of the scope of the AWS DVA.
Consider how to notify when an error occurs in a CI/CD environment with CodePipeline.
The AWS official explanation of the notification method is as follows
You can set up notifications so that users of a resource, such as a build project, repository, deployment application, or pipeline, receive emails about the event types you specify according to the notification rule you create.
Notification concepts
This page introduces how to use this notification rule to notify error messages that occur in the pipeline via e-mail through SNS.
Environment
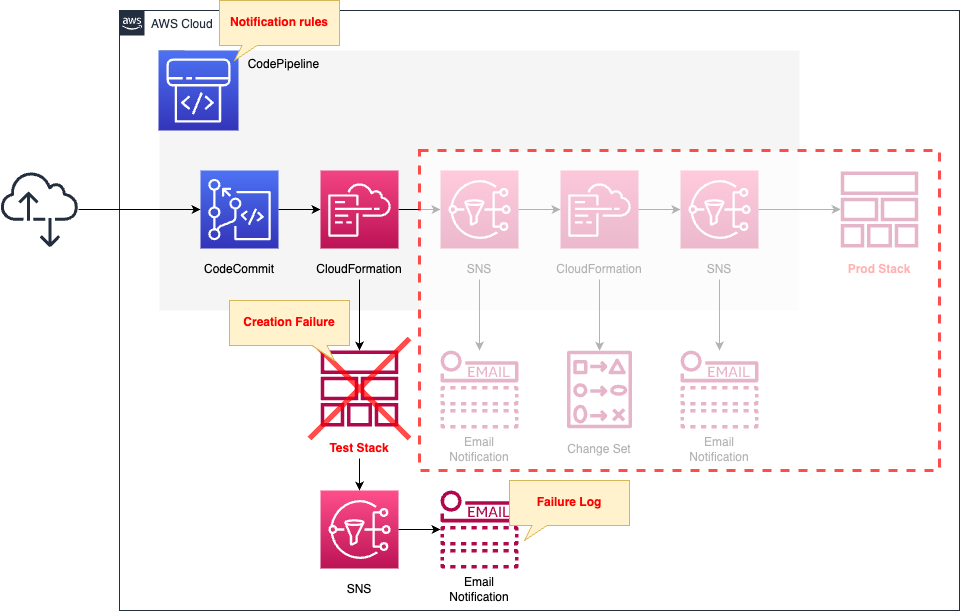
The basic structure is the same as that described in the following pages.

This is a CI/CD environment for CloudFormation using CodePipeline.
The changes on this page are the following two points
The first is to set up notification rules in CodePipeline.
The rules notify you of any error information that may occur on the pipeline.
The second point is a setting regarding the recipients of notification rules.
The content is notified by e-mail via SNS.
This time, we intentionally cause a failure in the creation of the test stack.
No further action stages in the pipeline will be advanced.
Upon failure, an email is sent via SNS according to the notification rules.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation templates are placed at the following URL
https://github.com/awstut-an-r/awstut-dva/tree/main/05/002
Explanation of key points of template files
This page focuses on the contents related to notification rules in CodePipeline.
For other details, please refer to the beginning of this page.
Notification Rule
Resources:
NotificationRule:
Type: AWS::CodeStarNotifications::NotificationRule
Properties:
DetailType: BASIC
EventTypeIds:
- codepipeline-pipeline-action-execution-failed
- codepipeline-pipeline-stage-execution-failed
- codepipeline-pipeline-pipeline-execution-failed
- codepipeline-pipeline-manual-approval-failed
Name: !Sub "${Prefix}-NotificationRule"
Resource: !Sub "arn:aws:codepipeline:${AWS::Region}:${AWS::AccountId}:${Pipeline}"
Status: ENABLED
Targets:
- TargetAddress: !Ref TopicArn
TargetType: SNS
Code language: YAML (yaml)There are three key points in creating a notification rule.
The first point is the source of the notification.
Specify the ARN of CodePipeline in the Resource property.
The second point is the notification target.
Specify the ARN, etc. of the SNS topic in the Targets property.
The third point is information about the event to be notified.
Specify the ID of the event to be notified in the EventTypeIds property.
The events that can be notified are summarized in the following official AWS page.
https://docs.aws.amazon.com/dtconsole/latest/userguide/concepts.html
In this case, we will specify four Failed notifications related to CodePipeline.
SNS
Topic
Resources:
Topic:
Type: AWS::SNS::Topic
Properties:
Subscription:
- Endpoint: !Ref MailAddress
Protocol: email
TopicName: !Ref Prefix
Code language: YAML (yaml)No special configuration is required.
Specify an e-mail address for the subscriber.
Access Policy
Resources:
TopicPolicy:
Type: AWS::SNS::TopicPolicy
Properties:
PolicyDocument:
Statement:
- Principal:
Service: codestar-notifications.amazonaws.com
Action: sns:Publish
Effect: Allow
Resource: !Ref TopicArn
Condition:
StringEquals:
aws:SourceAccount: !Ref AWS::AccountId
Topics:
- !Ref TopicArn
Code language: YAML (yaml)When designating an SNS as a notification destination, an important point to consider is the SNS access policy.
Set the access policy according to the following official AWS page
https://docs.aws.amazon.com/dtconsole/latest/userguide/set-up-sns.html
As above, specify CodeStar as the principal and then allow “sns:Publish”.
CloudFormation-related files
Check the files to run CloudFormation in CodePipeline.
Template File
AWSTemplateFormatVersion: 2010-09-09
Parameters:
Prefix:
Type: String
Default: dva-05-002-sample-lambda
Environment:
Type: String
Default: test
Handler:
Type: String
Default: index.lambda_handler
MemorySize:
Type: Number
Default: 128
Runtime:
Type: String
Default: python3.8
Timeout:
Type: Number
Default: 5
Resources:
Function:
Type: AWS::Lambda::Function
Properties:
Code:
ZipFile: |
def lambda_handler(event, context):
print('sample lambda')
FunctionName: !Sub "${Prefix}-${Environment}-Function"
Handler: !Ref Handler
MemorySize: !Ref MemorySize
Runtime: !Ref Runtime
Role: !GetAtt LambdaRole.Arn
LambdaRole:
Type: AWS::IAM::Role
DeletionPolicy: Delete
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
Service:
- lambda.amazonaws.com
ManagedPolicyArns:
- arn:aws:iam::aws:policy/service-role/AWSLambdaBasicExecutionRole
Code language: YAML (yaml)Define Lambda functions and IAM roles.
The key points are the function name (FunctionName) and memory size (MemorySize).
These values are set differently for the test and production stacks according to the template configuration file described below.
Template configuration file for test stack
{
"Parameters" : {
"Environment": "test",
"MemorySize": "0"
}
}
Code language: JSON / JSON with Comments (json)The value of memory size is the key point.
Dare to specify 0 (MB).
This will cause the stack to fail when it is created.
Architecting
Use CloudFormation to build this environment and check its actual behavior.
Create CloudFormation stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following pages.

After reviewing the resources in each stack, information on the main resources created in this case is as follows
- SNS Topic: fa-117
- CodeCommit: dva-05-002
- CodePipeline: dva-05-002
Email Address Authentication
If you have designated an email address as a subscriber to an SNS topic, you must authenticate that email address.
The following authentication email will be sent to the specified email address.
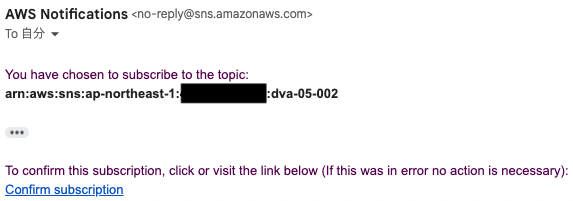
Press “Confirm subscription” to proceed with the authentication.
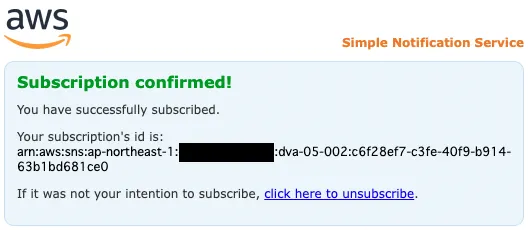
The above page will appear, indicating that authentication has been completed.
Resource Check
Check each resource from the AWS Management Console.
First, check the SNS topic.
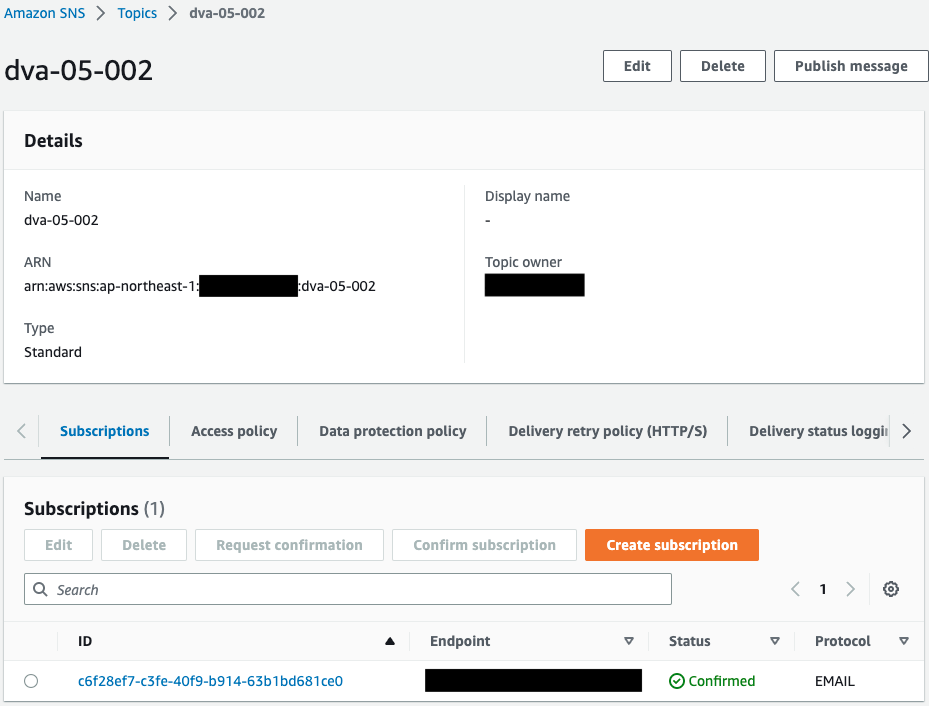
An email address is specified as a subscriber to the SNS topic.
Check CodePipeline
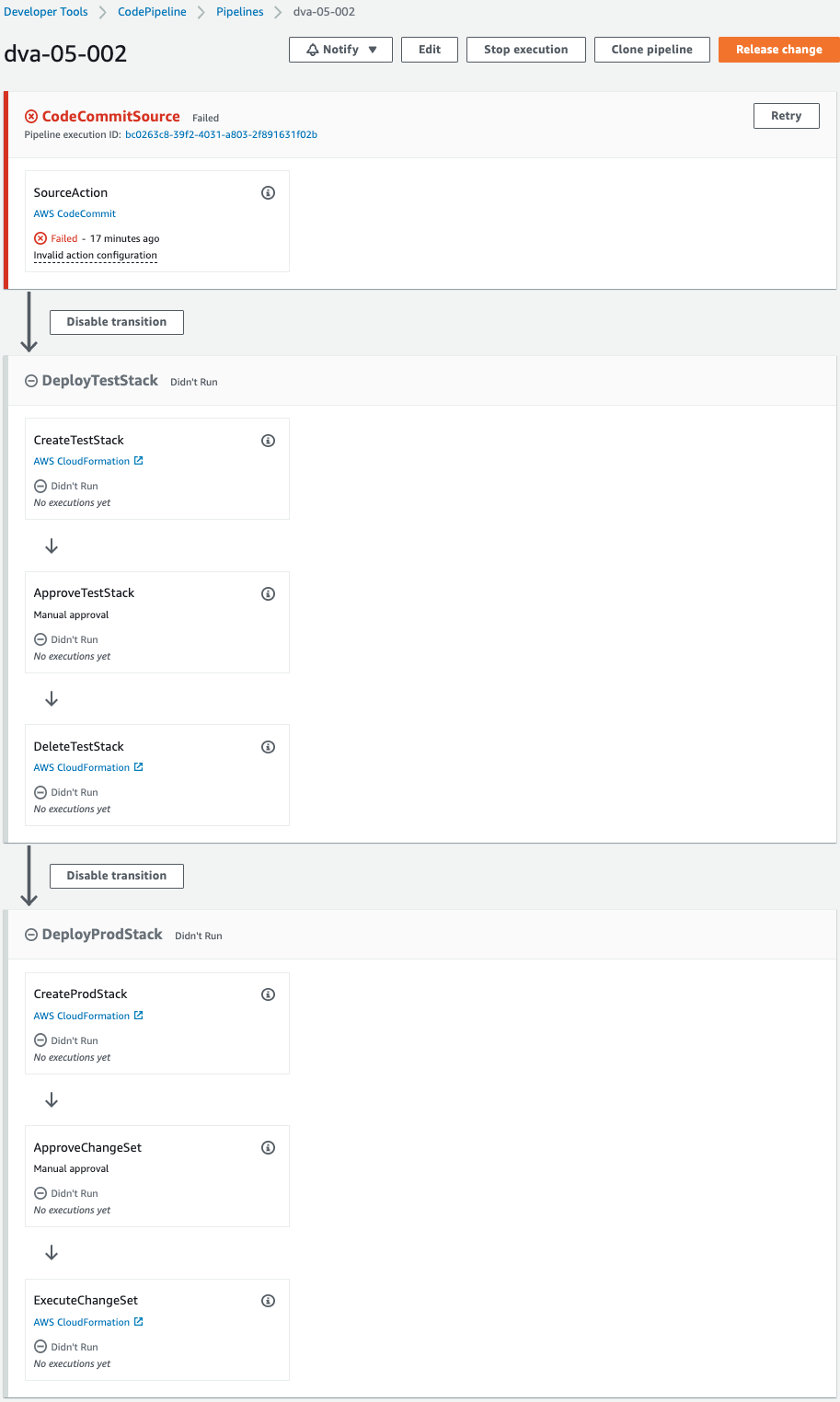
The pipeline is failing to execute.
This is because the pipeline was triggered by the creation of CodeCommit when the CloudFormation stack was created.
Since we are not pushing code to CodeCommit at this time, an error occurred during the pipeline execution process.
Check the notification rules.
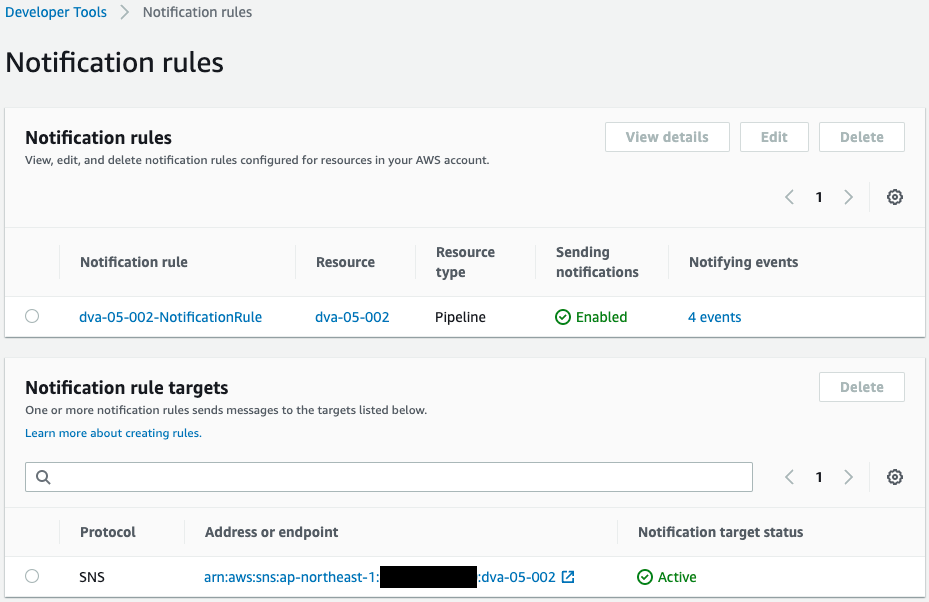
Indeed, a notification rule has been created.
You can see that the aforementioned SNS topic is specified as the notification destination and that it is enabled.
This means that CodeStar is properly authorized to notify messages to the SNS topic.
Details will also be confirmed.
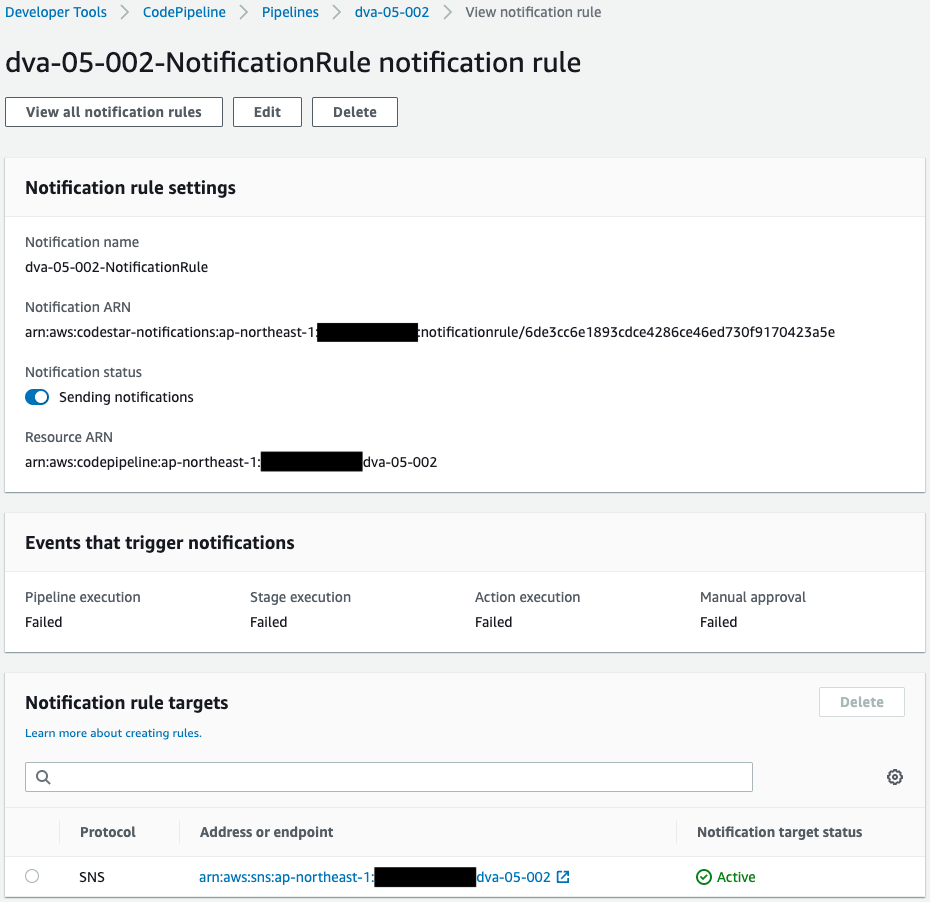
The contents of sending a Failed notification regarding CodePipeline.
Operation Check
Now that you are ready, push the code to CodeCommit.
$ git clone https://git-codecommit.ap-northeast-1.amazonaws.com/v1/repos/dva-05-002
Cloning into 'dva-05-002'...
warning: You appear to have cloned an empty repository.
Code language: Bash (bash)An empty repository has been pulled.
Add three files (sample-lambda.yaml, test-stack-configuration.json, and prod-stack-configuration.json) to the repository.
$ ls -al
total 12
drwxrwxr-x 3 ec2-user ec2-user 118 Jan 22 11:31 .
drwxrwxr-x 4 ec2-user ec2-user 151 Jan 22 11:31 ..
drwxrwxr-x 7 ec2-user ec2-user 119 Jan 22 11:31 .git
-rw-rw-r-- 1 ec2-user ec2-user 98 Jan 18 12:43 prod-stack-configuration.json
-rw-rw-r-- 1 ec2-user ec2-user 1667 Jan 18 11:40 sample-lambda.yaml
-rw-rw-r-- 1 ec2-user ec2-user 95 Jan 21 11:55 test-stack-configuration.json
Code language: Bash (bash)Push 3 files.
$ git add .
$ git commit -m 'first commit'
...
create mode 100644 prod-stack-configuration.json
create mode 100644 sample-lambda.yaml
create mode 100644 test-stack-configuration.json
$ git push
...
* [new branch] master -> master
Code language: Bash (bash)The push was successful.
The pipeline has now started.
After a short wait, the pipeline fails midway.
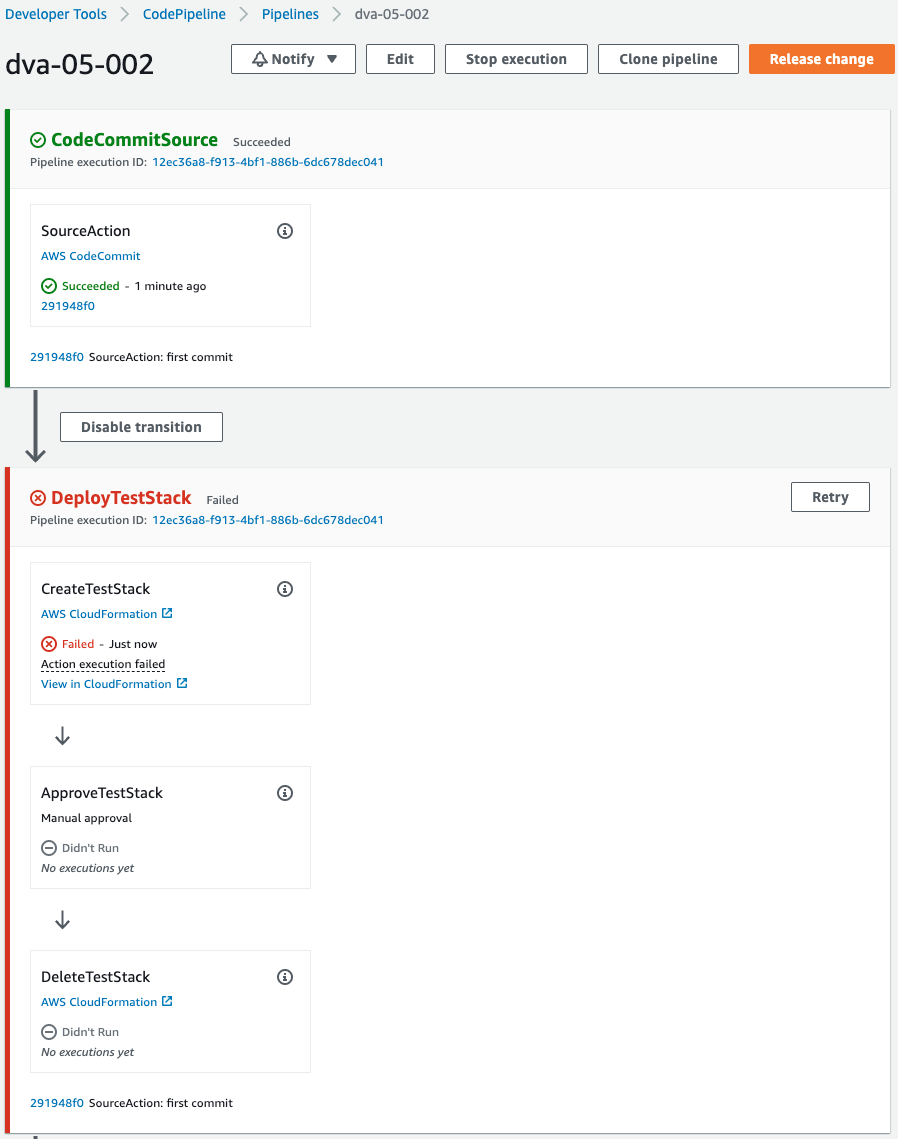
Failed to create test stack.
As mentioned earlier, this is due to the fact that the memory size of the Lambda function is set to “0”.
An email was immediately sent to
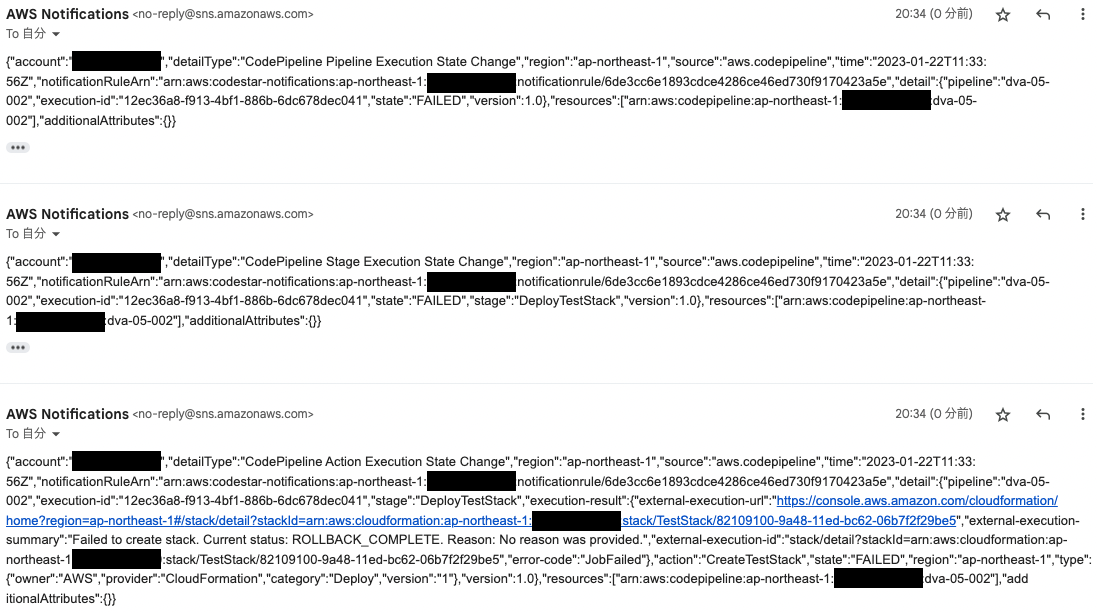
Three emails were received.
They indicate that errors occurred in Pipeline execution, Stage execution, and Action execution.
Also check the CloudFormation stack.
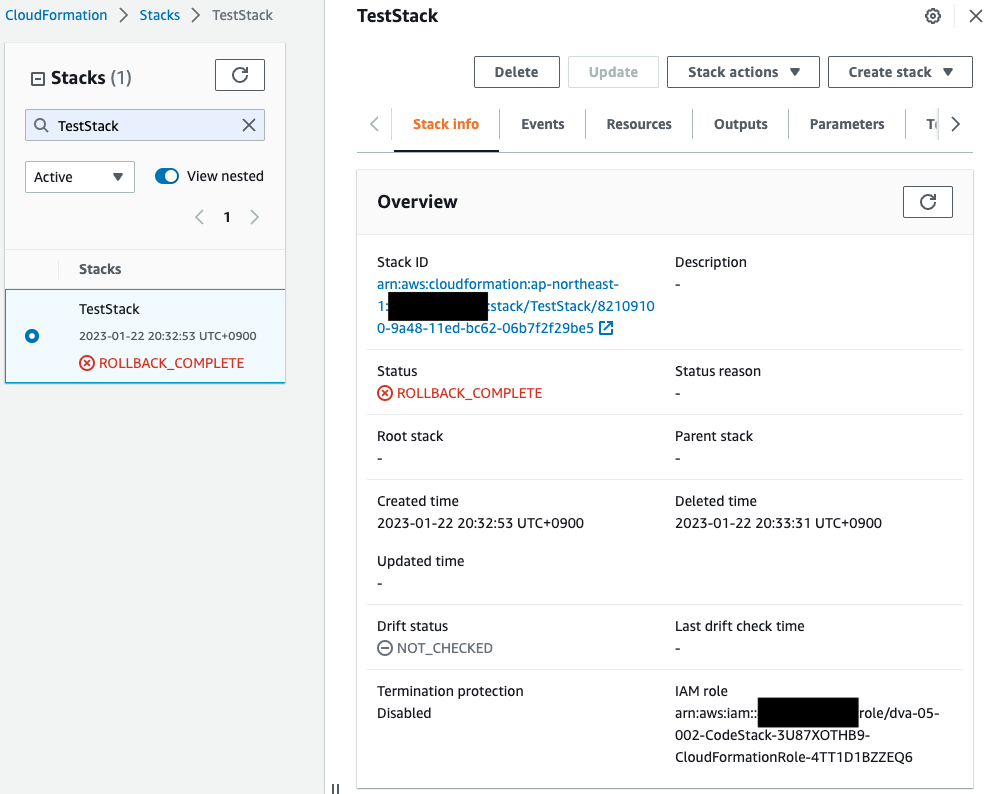
Indeed, the creation of the test stack has failed.
By creating a notification rule and specifying an SNS topic as the recipient of the notification, we were able to send email notifications of errors during CodePipeline execution.
Summary
We have introduced a method of email notification via SNS when an error occurs in CodePipeline.