Introduction to AWS Organaizations using CloudFormation
This page provides an introduction to AWS Organizations.
AWS Organizations lets you create new AWS accounts at no additional charge. With accounts in an organization, you can easily allocate resources, group accounts, and apply governance policies to accounts or groups.
AWS Organizations
In this introduction to AWS Organizations, we will create an organization, an Organizational Unit (OU), and member accounts.
Environment
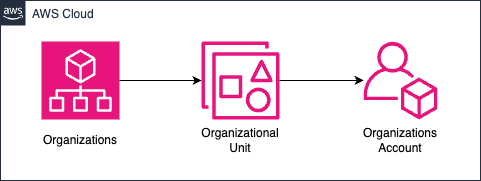
Create an Organization in AWS Organizations.
Create an Organizational Unit (OU) in your Organization.
Create one AWS account in the same OU.
CloudFormation template files
The above configuration is built with CloudFormation. The CloudFormation templates are placed at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/146
Explanation of key points of template files
Organization
The AWS official description of the Organization is as follows
An entity that you create to consolidate your AWS accounts so that you can administer them as a single unit.
AWS Organizations terminology and concepts
Resources:
Organization:
Type: AWS::Organizations::Organization
Properties:
FeatureSet: ALL
Code language: YAML (yaml)If the FeatureSet property is set to “ALL”, all features of the organization will be enabled. If the same property is set to “CONSOLIDATED_BILLING”, the organization’s bulk billing feature will be enabled.
In this case, the former is specified.
OU
AWS officially describes the OU as follows
A container for accounts within a root. An OU also can contain other OUs, enabling you to create a hierarchy that resembles an upside-down tree, with a root at the top and branches of OUs that reach down, ending in accounts that are the leaves of the tree.
AWS Organizations terminology and concepts
Resources:
OrganizationalUnit:
Type: AWS::Organizations::OrganizationalUnit
Properties:
Name: !Ref OUName
ParentId: !GetAtt Organization.RootId
Code language: YAML (yaml)Set the name of the OU with the Name property. In this case, “dev” is used as the OU name.
This time we will place this OU directly under the root. To do so, specify the root ID of the Organization in the ParentId property.
Account
AWS officially describes the Account as follows
An account in Organizations is a standard AWS account that contains your AWS resources and the identities that can access those resources.
AWS Organizations terminology and concepts
Resources:
Account:
Type: AWS::Organizations::Account
Properties:
AccountName: !Ref AccountName
Email: !Ref Email
ParentIds:
- !Ref OrganizationalUnit
RoleName: OrganizationAccountAccessRole
Code language: YAML (yaml)In the AccountName and Email properties, specify the name and email address of the account to be created. In this case, specify the account name “awstut”.
Specify the root or OU to which the account belongs in the ParentIds property. In this case, specify the ID of the aforementioned OU.
The RoleName property allows you to specify the role name of the IAM role that will be automatically prepared in this account. This role can be assumed and used by an administrative account user. In this case, we will specify the default “OrganizationAccountAccessRole”.
Architecting
Use CloudFormation to build this environment and check its actual behavior.
Create CloudFormation stacks and check the resources in the stacks
Create CloudFormation stacks. For information on how to create stacks and check each stack, please see the following page.

After reviewing the resources in each stack, information on the main resources created in this case is as follows
- Organization ID: r-e3tv
- OU name: dev
- Account name: awstut
Check the organization.
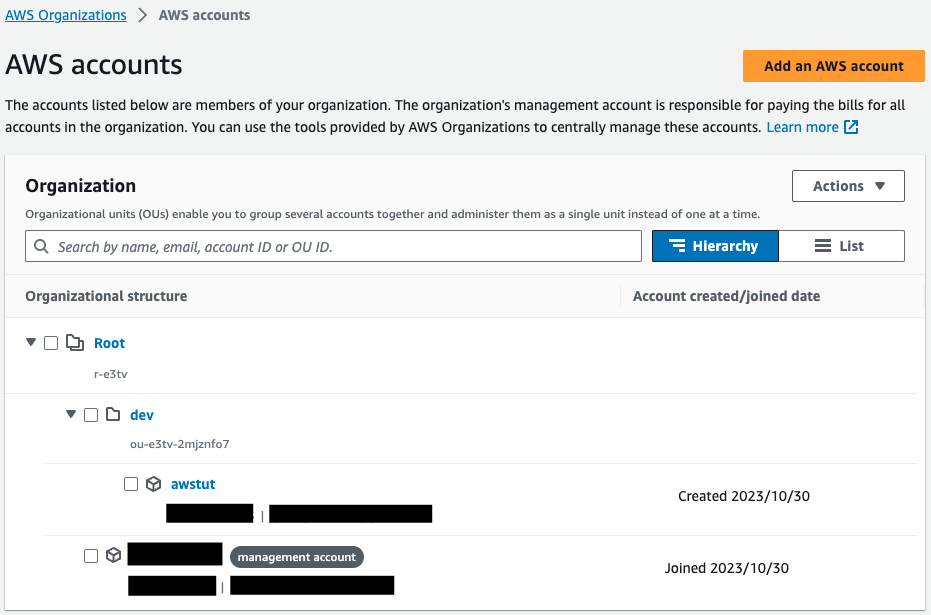
Within a single organization, root, OU, and administrative and member accounts are shown.
Check the OU.
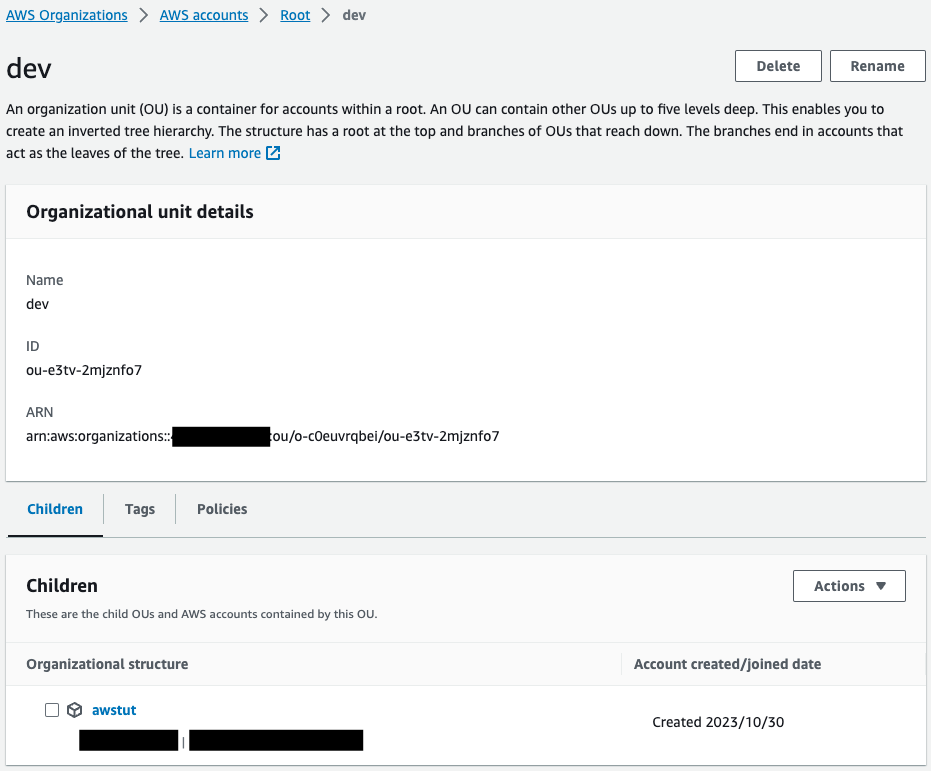
You can check member accounts and other information belonging to OU.
Verify your account.
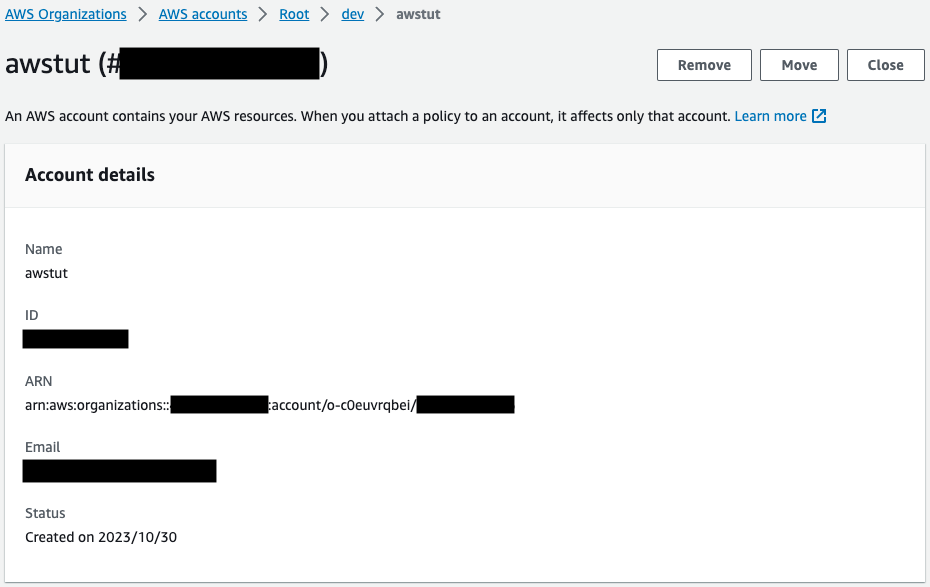
The account is indeed created as per the name and email address specified.
This account is then accessed. Access is done by assuming the aforementioned IAM role from the admin account.
For information on cross-account access using IAM roles, please see the following page.

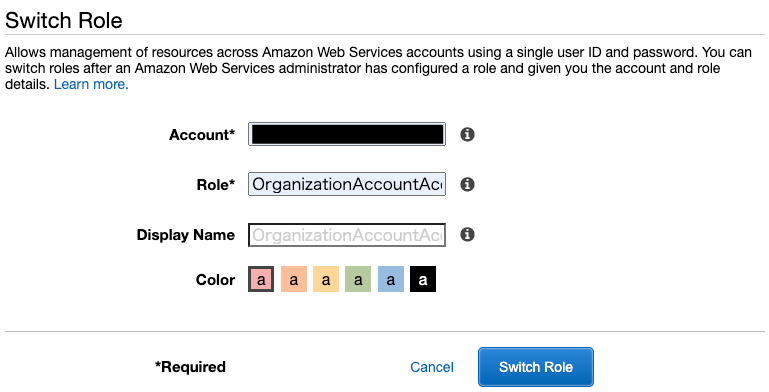
After entering the account ID and role name (OrganizationAccountAccessRole), press “Switch Role”.
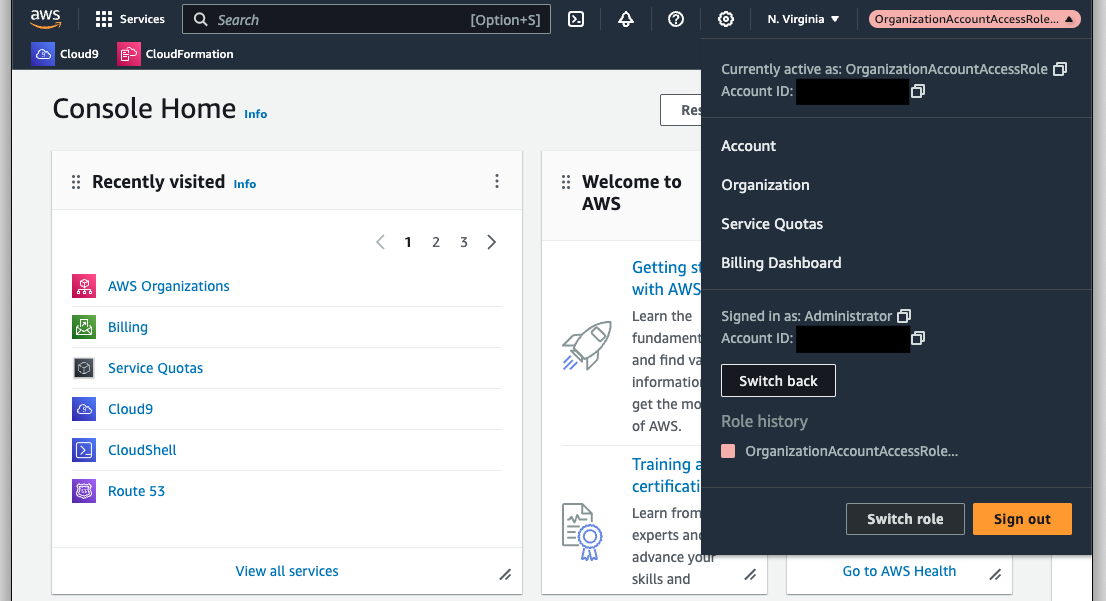
You have successfully accessed your member account.
Finally, we will review the details of the automatically created OrganizationAccountAccessRole.
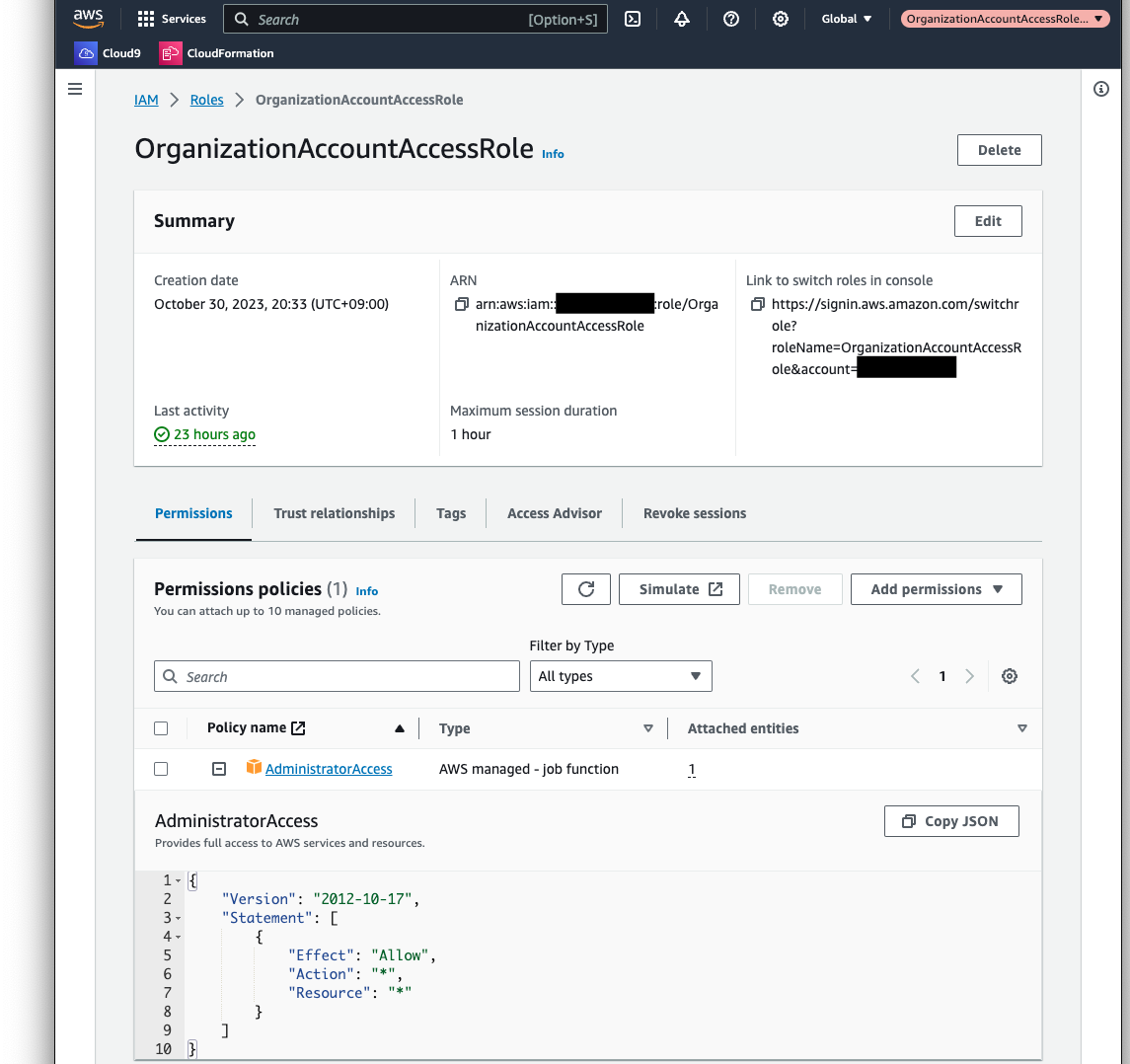
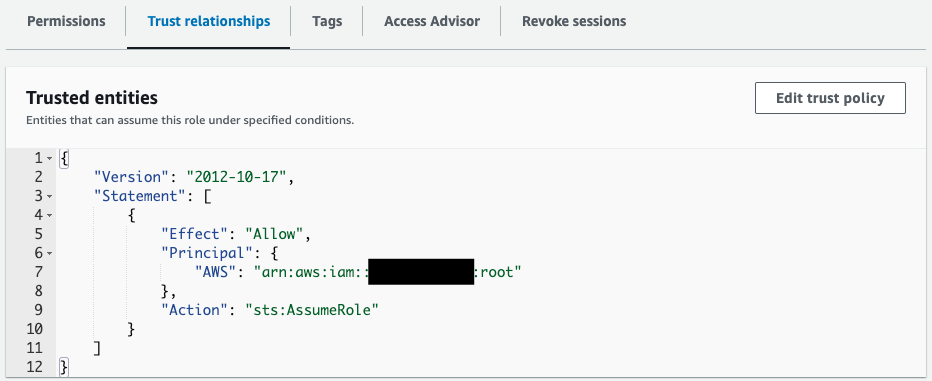
The policy attached to the role is the AWS admin policy AdministratorAccess, which allows all actions. The trust policy shows the root of the admin account as principal.
Summary
As an introduction to AWS Organizations, we used CloudFormation to create organizations, OUs, and member accounts.