CloudFront Geographic Restriction
This page is also one of the AWS SAA’s topics on designing secure applications and architectures.
We will review one of CloudFront’s features, geo-restriction.
If you need to prevent users in specific countries from accessing your content, you can use the CloudFront geographic restrictions feature to do one of the following:
・Allow your users to access your content only if they’re in one of the approved countries on your allow list.
・Prevent your users from accessing your content if they’re in one of the banned countries on your block list.
Restricting the geographic distribution of your content
This time, we will set up a geographic restriction using the whitelist method and check the actual behavior.
Environment
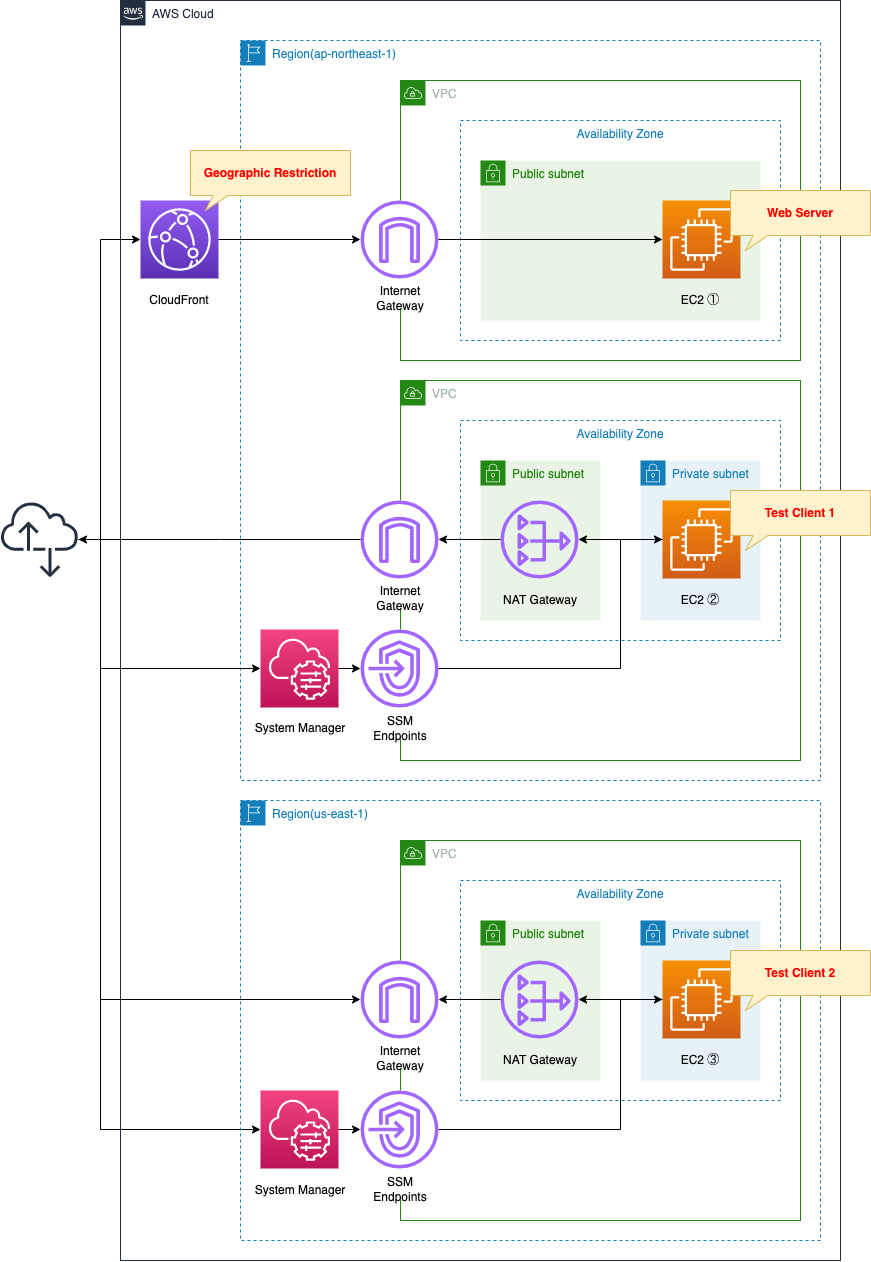
Create three VPCs.
One is a VPC for the web servers that will be geo-restricted by CloudFront.
The VPC will be created in the Tokyo Region (ap-northeast-1).
The origin server for CloudFront is the latest Amazon Linux 2-based EC2 instance.
Apache is installed and configured to run as a web server and return its own instance ID.
The other two are test VPCs.
We will build exactly the same environment in the Tokyo Region and Virginia Region (us-east-1).
Create an EC2 instance for accessing the web server, and access the web server for verification.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation template is located at the following URL
https://github.com/awstut-an-r/awstut-saa/tree/main/03/001
Explanation of points in template files
Configure whitelist-style geographic restrictions in CloudFront
This section will focus on confirming settings related to geographic restrictions.
For information on how to set up an EC2 instance as an origin server for CloudFront and how to configure the cache, see the following page.

Resources:
CloudFront:
Type: AWS::CloudFront::Distribution
Properties:
DistributionConfig:
DefaultCacheBehavior:
AllowedMethods:
- GET
- HEAD
CachedMethods:
- GET
- HEAD
Compress: true
ForwardedValues:
Cookies:
Forward: none
QueryString: false
TargetOriginId: !Ref InstancePublicDnsName
ViewerProtocolPolicy: allow-all
DefaultTTL: !Ref CacheTTL
MaxTTL: !Ref CacheTTL
MinTTL: !Ref CacheTTL
Enabled: true
Origins:
- CustomOriginConfig:
OriginProtocolPolicy: http-only
HTTPPort: !Ref HTTPPort
DomainName: !Ref InstancePublicDnsName
Id: !Ref InstancePublicDnsName
PriceClass: PriceClass_All
Restrictions:
GeoRestriction:
Locations:
- !Ref GeoRestrictionLocation
RestrictionType: whitelist
Code language: YAML (yaml)The key parameter for setting geographic restrictions is the GeoRestriction property within the Restrictions property.
In the RestrictionType property, you can select the restriction method from either the whitelist method or the blacklist method. In this case, we will use the former, so “whitelist” is specified.
Specify the target country in the Locations property. This time, we will use the whitelist method to restrict access, so only access from the specified country will be allowed. This time, using the built-in function Fn::Ref, specify “JP” to allow access only from Japan.
Architecting
Using CloudFormation, we will build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create a CloudFormation stack.
In this case, we will create 3 VPCs and create a stack for each VPC.
The following is a command to create a stack by referencing a template file placed on an S3 bucket.
$ aws cloudformation create-stack \
--stack-name saa-03-001 \
--template-url https://[s3-bucket-url]/saa-03-001.yaml \
--capabilities CAPABILITY_IAM \
--region ap-northeast-1
$ aws cloudformation create-stack \
--stack-name saa-03-001-test \
--template-url https://[s3-bucket-url]/saa-03-001-test.yaml \
--capabilities CAPABILITY_IAM \
--region ap-northeast-1
$ aws cloudformation create-stack \
--stack-name saa-03-001-test \
--template-url https://[s3-bucket-url]/saa-03-001-test.yaml \
--capabilities CAPABILITY_IAM \
--region us-east-1
Code language: Bash (bash)For information on how to create stacks and check each stack, please refer to the following page

After checking the resources for each stack, the following is the information on the main resources created in this case.
- Web server instance ID: i-0ad8cf475359b2566
- Public DNS for the web server: ec2-18-176-173-96.ap-northeast-1.compute.amazonaws.com
- Instance ID of test client (Tokyo Region): i-05f2bf8cfdcfcf971
- Instance ID for test client (Virginia Region): i-07fdf65d6a22d9422
The AWS Management Console also checks the status of the created CloudFront.
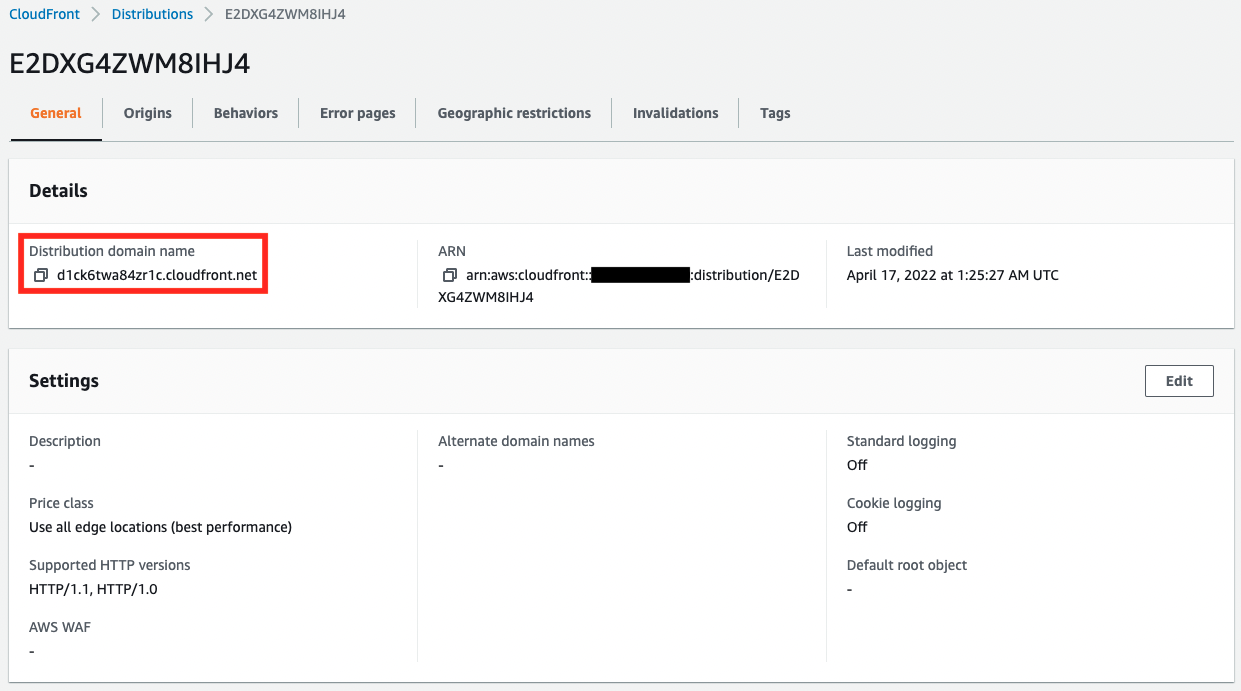
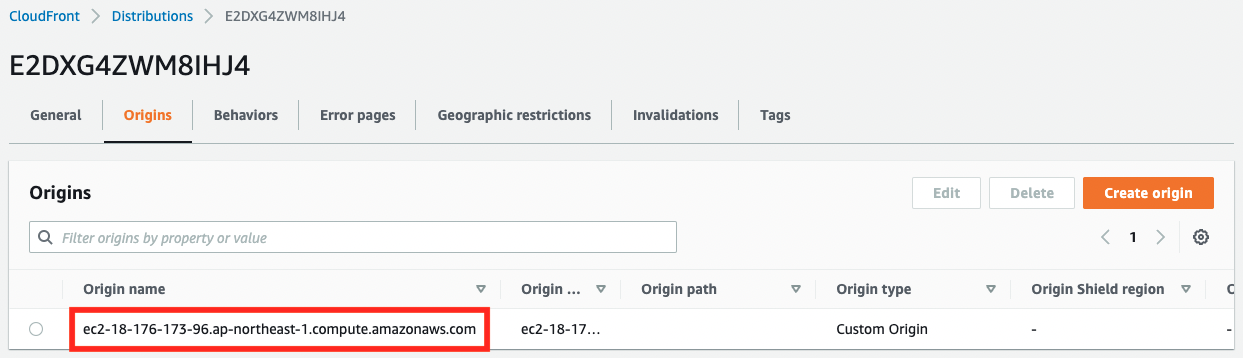
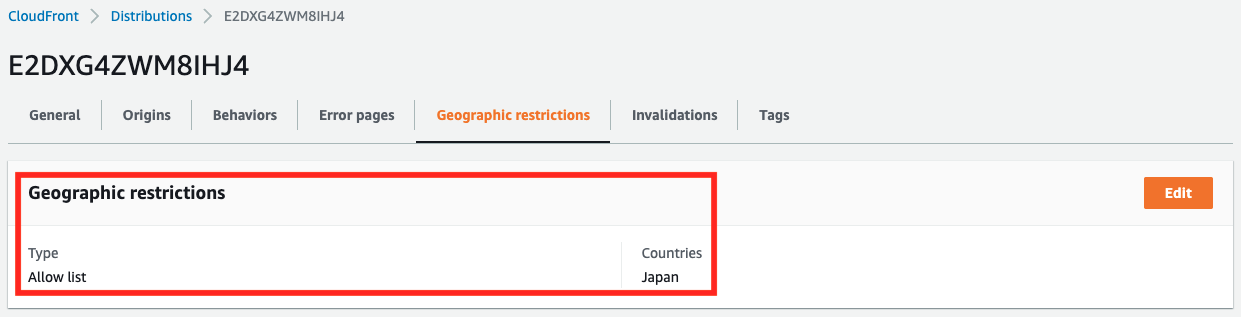
The CloudFront distribution has been successfully created.
You can see that the domain name of the created distribution is “d1ck6twa84zr1c.cloudfront.net”.
You can see that an EC2 instance has been set as the origin server.
You can see that only access from Japan is allowed as a geographical restriction.
Operation Verification 1: Accessing from region permitted by geographical restriction
Now that we are ready, we will check the actual behavior.
First, access is attempted from the verification environment on the Tokyo Region side.
Access an instance in the same environment using SSM Session Manager.
Please refer to the following page for details on accessing instances using this service.

% aws ssm start-session \
--target i-05f2bf8cfdcfcf971
--region ap-northeast-1
sh-4.2$
Code language: Bash (bash)The site has been accessed successfully.
Continue to access CloudFront for verification.
sh-4.2$ curl https://d1ck6twa84zr1c.cloudfront.net
instance-id: i-0ad8cf475359b2566
Code language: Bash (bash)Normal access was achieved.
Thus, access from countries specified in the white list was possible as normal.
Operation Verification 2: Accessing from regions not allowed by geographical restrictions
This time, access is attempted from the verification environment on the Virginia region side.
% aws ssm start-session -\
-target i-07fdf65d6a22d9422 \
--region us-east-1
sh-4.2$
Code language: Bash (bash)Successfully accessed.
Access and verify CloudFront as before.
sh-4.2$ curl https://d1ck6twa84zr1c.cloudfront.net
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/html4/loose.dtd">
<HTML><HEAD><META HTTP-EQUIV="Content-Type" CONTENT="text/html; charset=iso-8859-1">
<TITLE>ERROR: The request could not be satisfied</TITLE>
</HEAD><BODY>
<H1>403 ERROR</H1>
<H2>The request could not be satisfied.</H2>
<HR noshade size="1px">
The Amazon CloudFront distribution is configured to block access from your country.
We can't connect to the server for this app or website at this time. There might be too much traffic or a configuration error. Try again later, or contact the app or website owner.
<BR clear="all">
If you provide content to customers through CloudFront, you can find steps to troubleshoot and help prevent this error by reviewing the CloudFront documentation.
<BR clear="all">
<HR noshade size="1px">
<PRE>
Generated by cloudfront (CloudFront)
Request ID: qx0x5Uy6vGqeHrpIyE1pTBV73_twJfRSGOFuZZhKFaK5VzPDzV1LpQ==
</PRE>
<ADDRESS>
</ADDRESS>
</BODY></HTML>sh-4.2$
Code language: Bash (bash)An error page is displayed and access has failed.
The error message indicates that access from the country where the instance is hosted (the U.S.) is restricted due to CloudFront’s geo-restriction function.
Thus, by using CloudFront’s geo-restriction function, access from a specific country could be restricted.
Summary
We have seen that CloudFront can be used to restrict access to content based on geography.
We confirmed that geographic restrictions can be set using either the whitelist or blacklist method.