Creating Lambda Function URL by CloudFormation (NONE version)
Lambda Function URL was released on April 22, 2022.
AWS Lambda is announcing Lambda Function URLs, a new feature that makes it easier to invoke functions through an HTTPS endpoint as a built-in capability of the AWS Lambda service.
AWS Lambda Function URLs: built-in HTTPS endpoints for your Lambda functions
In this case, we will use CloudFormation to create Function URLs for Lambda inside and outside the VPC, with an authentication method of NONE.
Environment
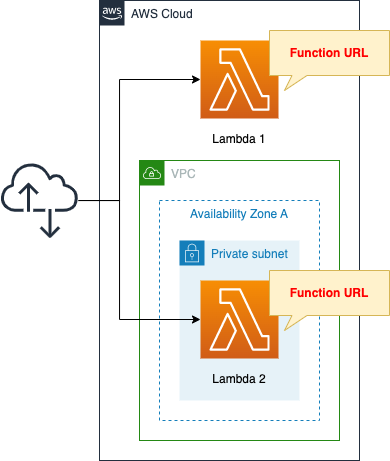
Create one Lambda function each inside and outside the VPC.
Create a Function URL for each function and access it over the Internet.
The runtime environment for Lambda functions is Python 3.8.
CloudFormation template files
The above configuration is built using CloudFormation.
The CloudFormation template is located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/038
Explanation of key points of the template files
Lambda Function
First, check the main body of the Lambda function.
Resources:
Function1:
Type: AWS::Lambda::Function
Properties:
Code:
ZipFile: |
def lambda_handler(event, context):
return 'hello, from function 1.'
FunctionName: !Sub "${Prefix}-function-01"
Handler: !Ref Handler
Runtime: !Ref Runtime
Role: !GetAtt FunctionRole1.Arn
Function2:
Type: AWS::Lambda::Function
Properties:
Code:
ZipFile: |
def lambda_handler(event, context):
return 'hello, from function 2.'
FunctionName: !Sub "${Prefix}-function-02"
Handler: !Ref Handler
Runtime: !Ref Runtime
Role: !GetAtt FunctionRole2.Arn
VpcConfig:
SecurityGroupIds:
- !Ref FunctionSecurityGroup
SubnetIds:
- !Ref FunctionSubnet
Code language: YAML (yaml)This is the same as a normal Lambda function.
The code to be executed is expressed inline.
For more information, please refer to the following page

This is a Lambda function to be installed in a VPC, but the security group to be applied is the one that permits inbound HTTPS (443/tcp) communication.
Resources:
FunctionSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: !Sub "${Prefix}-FunctionSecurityGroup"
GroupDescription: Allow HTTPS.
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: !Ref HTTPSPort
ToPort: !Ref HTTPSPort
CidrIp: 0.0.0.0/0
Code language: YAML (yaml)This is a point about the subnet and VPC where the Lambda will be installed, but no Internet gateway or routing configuration to that gateway is required.
Resources:
VPC:
Type: AWS::EC2::VPC
Properties:
CidrBlock: !Ref VPCCidrBlock
FunctionSubnet:
Type: AWS::EC2::Subnet
Properties:
CidrBlock: !Ref CidrIp
VpcId: !Ref VPC
AvailabilityZone: !Sub "${AWS::Region}${AvailabilityZone}"
Code language: YAML (yaml)Lambda Function URL
Check the HTTPS endpoint (Fnction URL) that calls the function.
Resources:
FunctionUrl1:
Type: AWS::Lambda::Url
Properties:
AuthType: NONE
TargetFunctionArn: !GetAtt Function1.Arn
FunctionUrl2:
Type: AWS::Lambda::Url
Properties:
AuthType: NONE
TargetFunctionArn: !GetAtt Function2.Arn
Code language: YAML (yaml)Create an endpoint by setting the Type property to AWS::Lambda::Url.
Set the AuthType property to “NONE” since IAM is not used for the authentication method this time.
Permission to invoke Lambda from Function URL
Currently, it is not possible to invoke a Lambda function over the Internet from a Function URL.
This is because the permission to invoke Lambda functions has not been set.
To solve this problem, create a Permission.
Resources:
FunctionUrlPermission1:
Type: AWS::Lambda::Permission
Properties:
Action: lambda:InvokeFunctionUrl
FunctionName: !GetAtt Function1.Arn
FunctionUrlAuthType: NONE
Principal: "*"
FunctionUrlPermission2:
Type: AWS::Lambda::Permission
Properties:
Action: lambda:InvokeFunctionUrl
FunctionName: !GetAtt Function2.Arn
FunctionUrlAuthType: NONE
Principal: "*"
Code language: YAML (yaml)The point is to set “lambda:InvokeFunctionUrl” to the Action property.
This will authorize the user to invoke the Lambda function via Function URL.
Architecting
Using CloudFormation, we will build this environment and check the actual behavior.
Create CloudFormation stacks and check resources in stacks
Create a CloudFormation stack.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- Function URL for Lambda function 1: https://4qbav7r5hywdr7clbyayo4n7gm0exogq.lambda-url.ap-northeast-1.on.aws/
- Function URL for Lambda Function 2: https://f4hcdqzqcllahzh7gcc7datqdm0kvahd.lambda-url.ap-northeast-1.on.aws/
The Function URL for each function is also confirmed from the AWS Management Console.
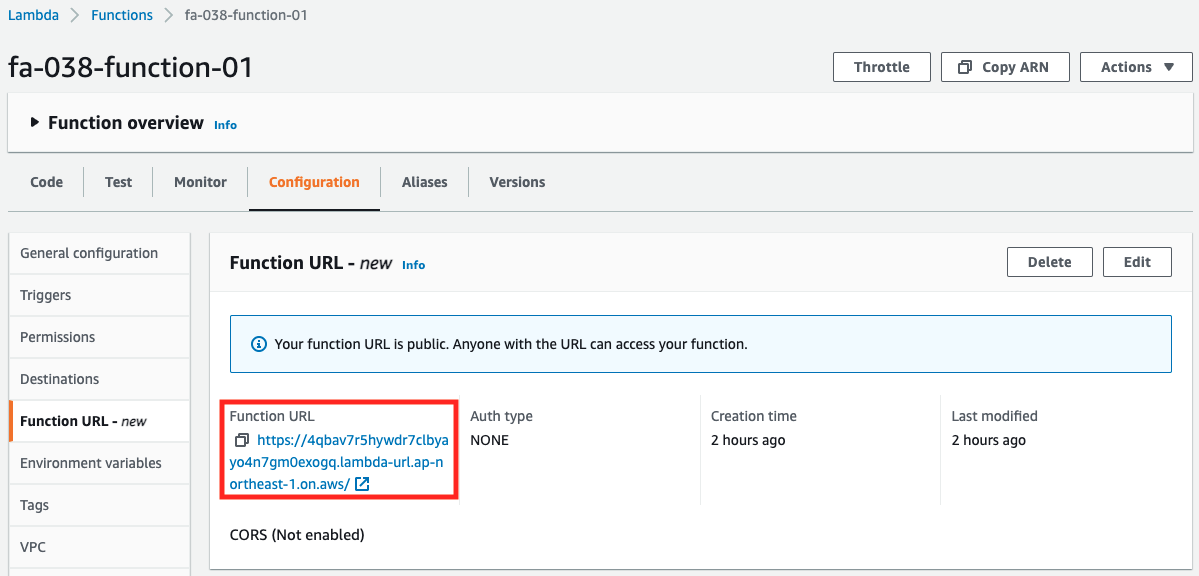
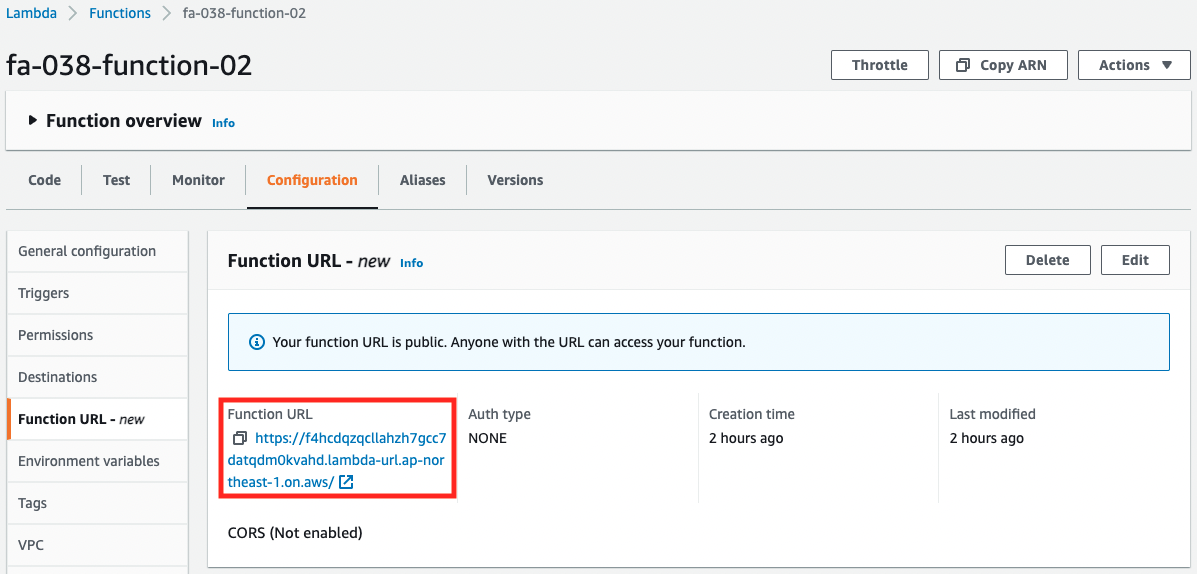
The Function URL has been successfully created.
Confirmation of Operation
Now that everything is ready, access each Function URL.
First, Function 1.
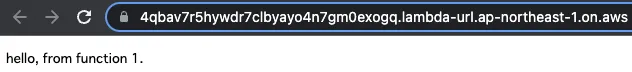
The response is returned normally.
As you can see, we were able to invoke a Lambda function outside the VPC through the Function URL.
Next is Function2.
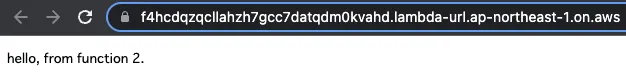
This one also returned a normal response.
In this way, the Lambda function inside the VPC could be invoked through the Function URL.
Summary
A new function of Lambda function, Function URL, was created with CloudFormation.
We have confirmed that Lambda functions inside and outside of VPC can be invoked through Function URLs.