Create your own rule groups in WAF Web ACL to restrict geography
WAF Web ACL allows you to set up rules with various conditions.
In this article, we will create our own rule group for geo-restriction to block access from specific countries.
This time, we will show you how to use WAF Web ACL for geo-restriction, but you can also use CloudFront for the same purpose.
For more details, please refer to the following page

Environment
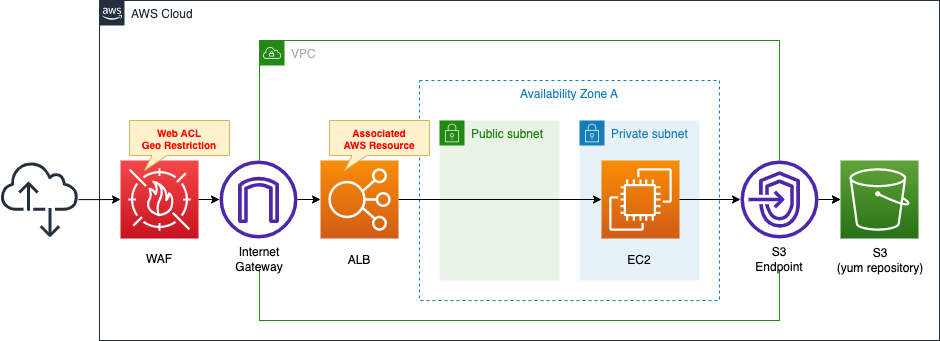
Create a WAF Web ACL.
Perform geographic restriction.
Specifically, create your own rule group and set a rule to block access from Japan (JP) in it.
Apply the created Web ACL to ALB.
Attach an EC2 instance in a private subnet to ALB.
The EC2 instance should be the latest version of Amazon Linux 2.
Install Apache on the EC2 instance, configure it to run as a web server and return its own instance ID.
Apache is installed from a yum repository built on S3.
CloudFormation template files
The above configuration is built using CloudFormation.
The CloudFormation template is located at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/046
Explanation of key points of template files
This page focuses on how to create your own rule groups and geo-restrictions with WAF Web ACL.
For more information on the basics of WAF Web ACL, please refer to the following page

For information on how to attach an EC2 in a private subnet to an ALB, please refer to the following page
For information on how to execute yum on EC2 in a private subnet, please refer to the following page
Setting up geo-restriction rules for your own rule group
Resources:
RuleGroup:
Type: AWS::WAFv2::RuleGroup
Properties:
Capacity: 10
Name: !Sub "${Prefix}-GeoRestrictionRuleGroup"
Rules:
- Action:
Block: {}
Name: !Sub "${Prefix}-GeoRestrictionRule"
Priority: 0
Statement:
GeoMatchStatement:
CountryCodes:
- JP
VisibilityConfig:
CloudWatchMetricsEnabled: true
MetricName: !Sub "${Prefix}-GeoRestrictionRule"
SampledRequestsEnabled: true
Scope: REGIONAL
VisibilityConfig:
CloudWatchMetricsEnabled: true
MetricName: !Sub "${Prefix}-GeoRestrictionRuleGroup"
SampledRequestsEnabled: true
Code language: YAML (yaml)You can define rule groups with the AWS::WAFv2::RuleGroup type.
We will cover the key properties.
The Capacity property sets the Web ACL Capacity Unit (WCU) for the entire rule group.
The WCU specification is detailed in the following official page.
https://docs.aws.amazon.com/waf/latest/developerguide/how-aws-waf-works.html
The key point of the Capacity property in a rule group is that once it is set, it cannot be modified later.
When you create your own rule group, you define this, and you cannot change it after creation.
AWS::WAFv2::RuleGroup
Therefore, you should try to design your capacity with a margin of safety.
In this case, we set it to “10”.
Originally, the WCU for geo-restrictive statements is “1”, but we made sure that there is enough margin for future expansion.
Set the rules to be defined in the group in the Rules property.
The Action property defines the response to traffic that meets the rule’s conditions.
You can set “Allow” or “Block”.
In this case, we will restrict access from Japan, so we will set “Block”.
Define the content of the rule in the Statement property.
Use the GeoMatchStatement property for geographic restriction.
Specify the target country code in the CountryCodes property.
In this case, we specify “JP” because Japan is the target country.
According to the following page, the WCU for geographic restriction is “1”.
https://docs.aws.amazon.com/waf/latest/developerguide/waf-rule-statements-list.html
The Scope property is determined by which resource the Web ACL containing this rule group is applied to.
If the Web ACL is applied to CloudFront, it is “CLOUDFRONT”, and if it is applied to other resources, it is “REGIONAL”.
In this case, since it is an ALB, it is the latter.
Setting your own rule group in WAF Web ACL
Resources:
WebACL:
Type: AWS::WAFv2::WebACL
Properties:
DefaultAction:
Allow: {}
Name: !Sub "${Prefix}-WebACL"
Rules:
- Name: !Sub "${Prefix}-WebACL-GeoRestriction"
OverrideAction:
None: {}
Priority: 0
Statement:
RuleGroupReferenceStatement:
Arn: !GetAtt RuleGroup.Arn
VisibilityConfig:
CloudWatchMetricsEnabled: true
MetricName: !Sub "${Prefix}-WebACL-GeoRestriction"
SampledRequestsEnabled: true
Scope: REGIONAL
VisibilityConfig:
CloudWatchMetricsEnabled: true
MetricName: !Ref Prefix
SampledRequestsEnabled: true
Code language: YAML (yaml)To apply your own rule group to the Web ACL, use the RuleGroupReferenceStatement property in the Statement property.
Specify the ARN of the rule group to which the Web ACL is related.
Architecting
Use CloudFormation to build this environment and check the actual behavior.
Create CloudFormation stacks and check the resources in stacks
Create a CloudFormation stack.
For information on how to create stacks and check each stack, please refer to the following page

After checking the resources in each stack, information on the main resources created this time is as follows
- EC2 instance ID: i-060ce9534adc3fa3d
- ALB name: fa-046-ALB
- ALB URL: http://fa-046-alb-926330093.ap-northeast-1.elb.amazonaws.com/
From the AWS Management Console, check the WAF.
First is a rule group that you created yourself.
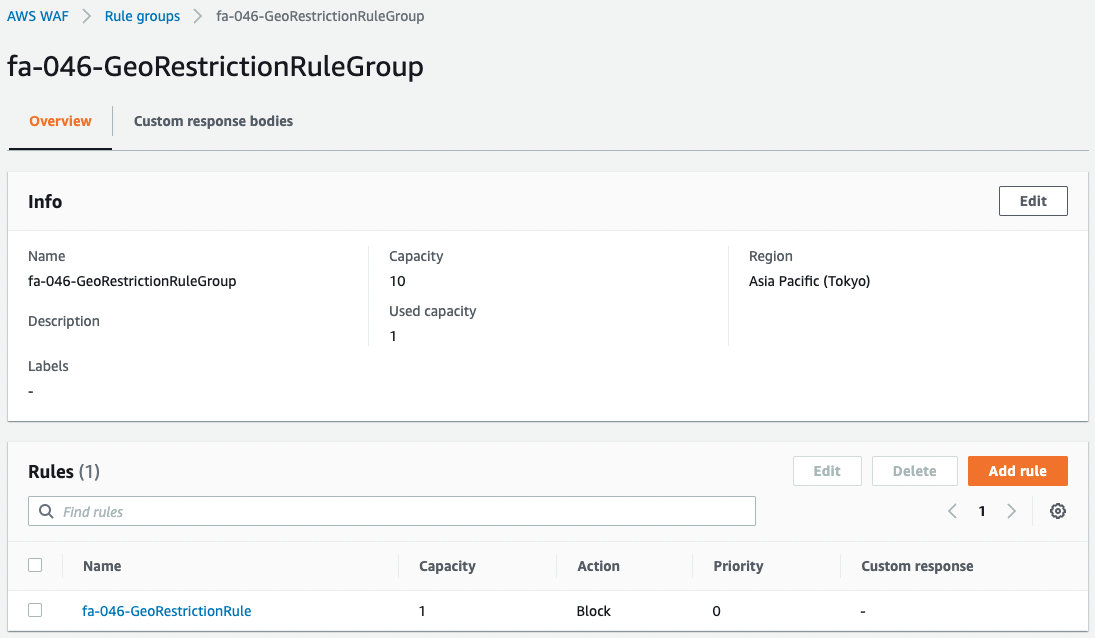
You can see that the capacity set in the rule group is “10” and the actual capacity consumed is “1”.
You can also see that there is only one rule set in the group.
Next, let us check the contents of the rule.
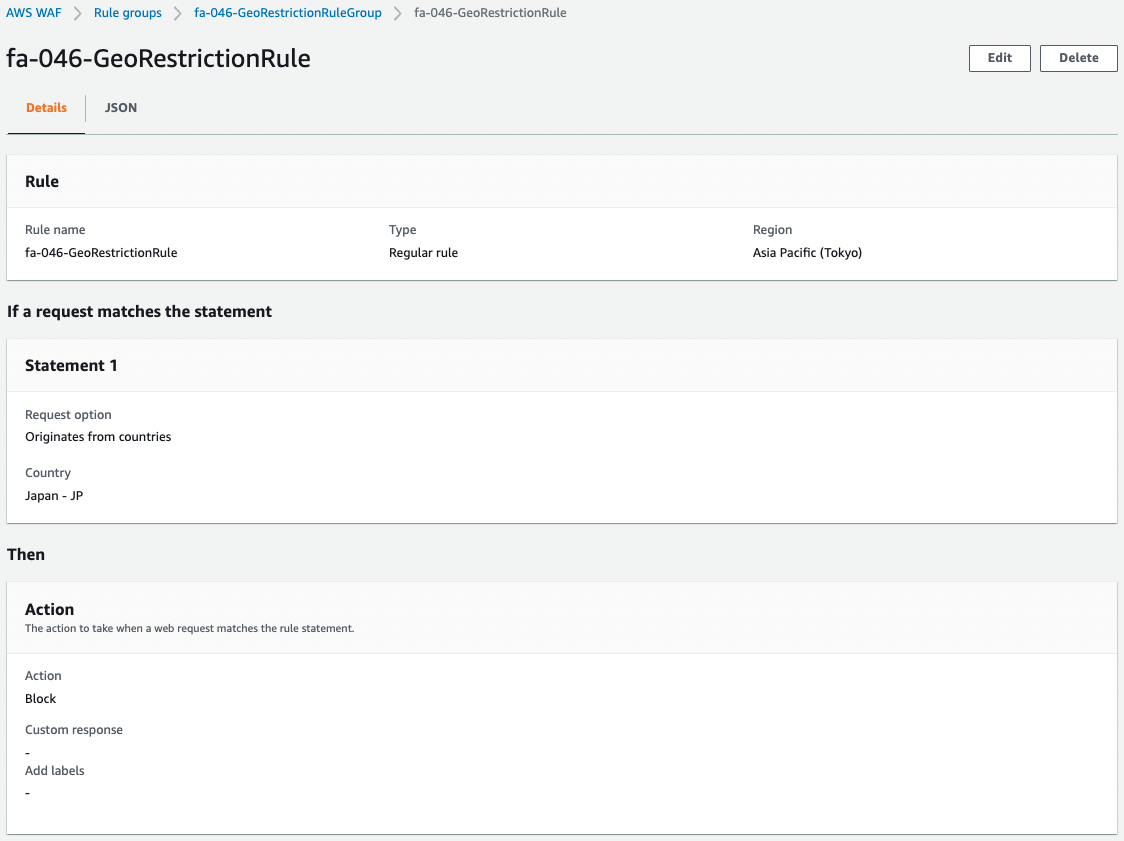
The rule is set to deny access from Japan.
Check Action
Now that everything is ready, try to access ALB from Japan.
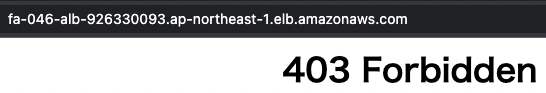
Access was denied.
Because you accessed from Japan, the WAF Web ACL filtered access before it reached the ALB.
To confirm, change the action of the geo-restriction.
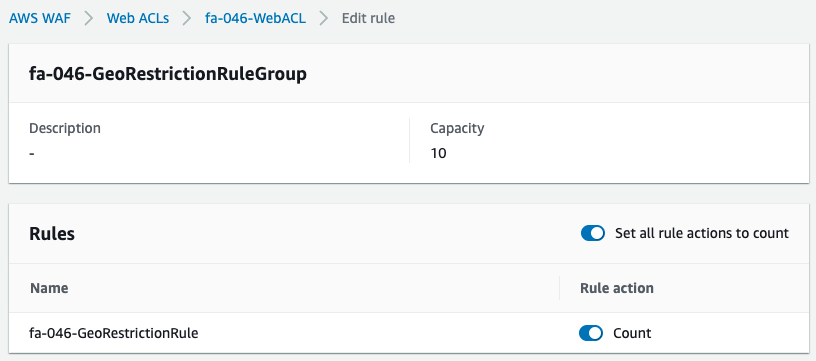
We changed the rule action from blocking to counting, i.e., keeping the rule alive but only counting the number of traffic that corresponds to the rule.
Access the ALB again.
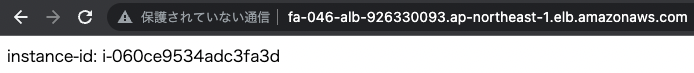
You can now access the ALB.
This is because the rule action has been changed from blocking to only counting, so access is now possible.
Finally, we check the sampled requests.
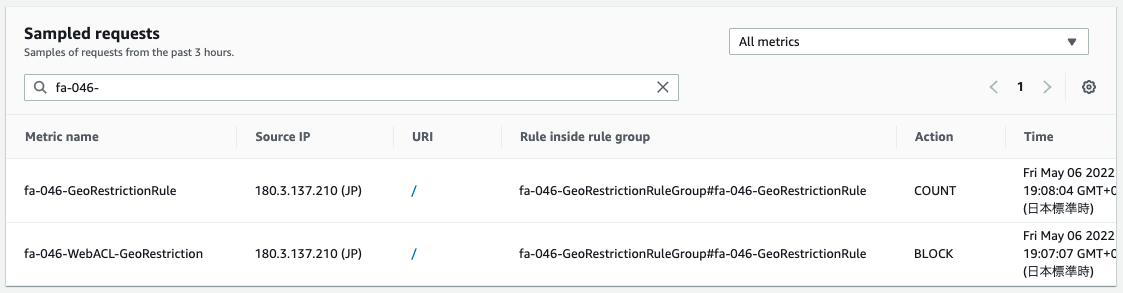
There is one blocked request and one counted request.
This is the first access and the access after the rule change.
Summary
We have created our own rule group and confirmed how to restrict geography using WAF Web ACL.