Introduction to AWS Service Catalog using CloudFormation
This page covers AWS Service Catalog.
Service Catalog allows organizations to centrally manage commonly deployed IT services, and helps organizations achieve consistent governance and meet compliance requirements. End users can quickly deploy only the approved IT services they need, following the constraints set by your organization.
What Is Service Catalog?
In this introduction to Service Catalog, the objective is to build the contents covered in the following pages using CloudFormation.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted.html
Environment
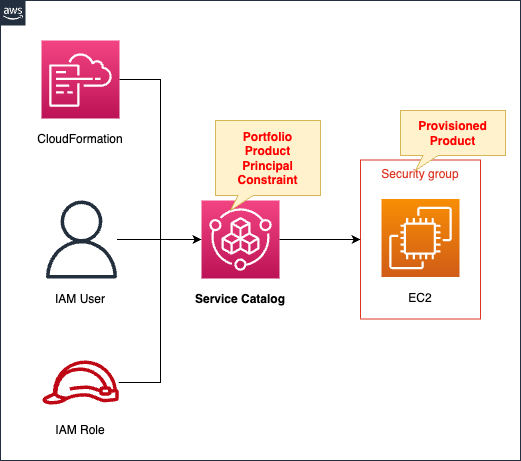
Create an IAM user and the IAM group to which the user belongs.
Create a Service Catalog portfolio.
Within the portfolio, register the following resources as products
- EC2 Instance
- Security Group
The above resources are defined in a CloudFormation template file, which is then associated with a portfolio to create a product.
Set the following two constraints
- Constraints on possible values for template parameters at product launch time
- Constraints on IAM roles assumed by Service Catalog at product launch
The aforementioned IAM group is targeted and authorized to access this portfolio.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation template is placed at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/124
Explanation of key points of template files
(Reference) IAM User and Group
Resources:
Group:
Type: AWS::IAM::Group
Properties:
GroupName: !Sub "${Prefix}-Endusers"
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AWSServiceCatalogEndUserFullAccess
- arn:aws:iam::aws:policy/AmazonEC2ReadOnlyAccess
User:
Type: AWS::IAM::User
Properties:
Groups:
- !Ref Group
LoginProfile:
Password: !Ref IAMUserPassword
PasswordResetRequired: false
UserName: !Sub "${Prefix}-User"
Code language: YAML (yaml)The IAM users who are allowed access to Service Catalog and the IAM groups they belong to.
Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-iamenduser.html
The key point is the IAM policy to attach to the IAM group.
Attach the AWS administration policy AWSServiceCatalogEndUserFullAccess to give access to the Service Catalog to users belonging to the group.
Also, after launching the product, attach AmazonEC2ReadOnlyAccess to check the configuration status of the EC2 instance you created.
Product Template
AWSTemplateFormatVersion: 2010-09-09
Description: |
AWS Service Catalog sample template. Creates an Amazon EC2 instance
running the Amazon Linux AMI. The AMI is chosen based on the region
in which the stack is run. This example creates an EC2 security
group for the instance to give you SSH access. **WARNING** This
template creates an Amazon EC2 instance. You will be billed for the
AWS resources used if you create a stack from this template.
Parameters:
InstanceType:
Description: EC2 instance type.
Type: String
Default: t2.micro
AllowedValues:
- t2.micro
- t2.small
- t2.medium
- m3.medium
- m3.large
- m3.xlarge
- m3.2xlarge
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: Instance configuration
Parameters:
- InstanceType
ParameterLabels:
InstanceType:
default: "Server size:"
Mappings:
AWSRegionArch2AMI:
us-east-1:
HVM64: ami-08842d60
us-west-2:
HVM64: ami-8786c6b7
us-west-1:
HVM64: ami-cfa8a18a
eu-west-1:
HVM64: ami-748e2903
ap-southeast-1:
HVM64: ami-d6e1c584
ap-northeast-1:
HVM64: ami-35072834
ap-southeast-2:
HVM64: ami-fd4724c7
sa-east-1:
HVM64: ami-956cc688
cn-north-1:
HVM64: ami-ac57c595
eu-central-1:
HVM64: ami-b43503a9
Resources:
EC2Instance:
Type: AWS::EC2::Instance
Properties:
InstanceType: !Ref InstanceType
SecurityGroups:
- !Ref InstanceSecurityGroup
ImageId: !FindInMap
- AWSRegionArch2AMI
- !Ref AWS::Region
- HVM64
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Enable SSH access via port 22
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
Outputs:
PublicDNSName:
Description: Public DNS name of the new EC2 instance
Value: !GetAtt EC2Instance.PublicDnsName
PublicIPAddress:
Description: Public IP address of the new EC2 instance
Value: !GetAtt EC2Instance.PublicIp
Code language: YAML (yaml)The CloudFormation template file described in the following page has been converted to YAML with some modifications.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-template.html
The changes are as follows
- Removed settings related to key pairs.
- Removed setting regarding SSH source restrictions.
Service Catalog
Portfolio
A portfolio is a collection of products that contains configuration information.
Portfolios
Resources:
Portfolio:
Type: AWS::ServiceCatalog::Portfolio
Properties:
AcceptLanguage: !Ref AcceptLanguage
Description: Sample portfolio that contains a single product.
DisplayName: Engineering Tools
ProviderName: IT (it@example.com)
Code language: YAML (yaml)Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-portfolio.html
Product
A product is an IT service that you want to make available for deployment on AWS. A product consists of one or more AWS resources, such as EC2 instances, storage volumes, databases, monitoring configurations, and networking components, or packaged AWS Marketplace products.
Products
Resources:
CloudFormationProduct:
Type: AWS::ServiceCatalog::CloudFormationProduct
Properties:
AcceptLanguage: !Ref AcceptLanguage
Description: Cloud development environment configured for engineering staff. Runs AWS Linux.
Name: Linux Desktop
Owner: IT
ProvisioningArtifactParameters:
- Description: Base Version
DisableTemplateValidation: true
Info:
LoadTemplateFromURL: !Sub "https://${TemplateBucketName}.s3.${AWS::Region}.amazonaws.com/${Prefix}/development-environment.yaml"
Name: v1.0
ReplaceProvisioningArtifacts: false
SupportDescription: Contact the IT department for issues deploying or connecting to this product.
SupportEmail: ITSupport@example.com
SupportUrl: https://wiki.example.com/IT/support
Code language: YAML (yaml)Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-product.html
In the LoadTemplateFromURL property, specify the CloudFormation template file for the product described above.
This time, upload the file to the S3 bucket and specify the URL of the file.
Now that the portfolio and products have been defined, define the following resources and associate them
Resources:
PortfolioProductAssociation:
Type: AWS::ServiceCatalog::PortfolioProductAssociation
Properties:
AcceptLanguage: !Ref AcceptLanguage
PortfolioId: !Ref Portfolio
ProductId: !Ref CloudFormationProduct
Code language: YAML (yaml)Constraints
Constraints can control the launch context of a product (launch constraints), or add rules to the AWS CloudFormation template (template constraints).
Step 5: Add a Template Constraint to Limit Instance Size
Resources:
LaunchTemplateConstraint:
Type: AWS::ServiceCatalog::LaunchTemplateConstraint
Properties:
AcceptLanguage: !Ref AcceptLanguage
PortfolioId: !Ref Portfolio
ProductId: !Ref CloudFormationProduct
Rules: |
{
"Rule1": {
"Assertions": [
{
"Assert" : {"Fn::Contains": [["t2.micro", "t2.small"], {"Ref": "InstanceType"}]},
"AssertDescription": "Instance type should be t2.micro or t2.small"
}
]
}
Code language: YAML (yaml)Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-constraint.html
In the CloudFormation template file described above, the Parameters section allowed you to select the size of the EC2 instance to launch.
By defining constraints on the template, you can limit this possible value.
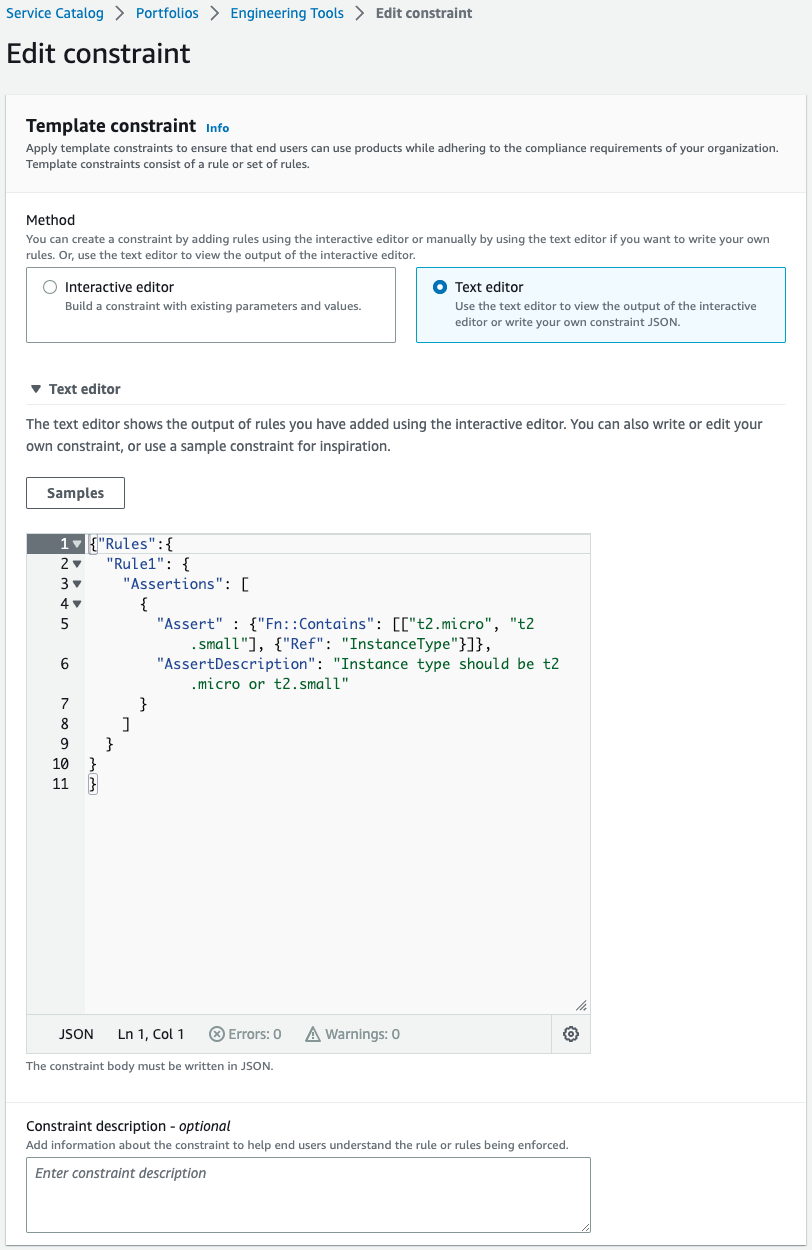
The specifics of the constraints are done in the Rules property.
Following the above page, only two sizes (t2.micro, t2.small) can be selected in this case.
Note that this property must be a string in JSON format.
Restrictions on IAM Roles
A launch constraint designates an IAM role that Service Catalog assumes when an end user launches a product.
Step 6: Add a Launch Constraint to Assign an IAM Role
Resources:
LaunchRoleConstraint:
DependsOn:
- Portfolio
- CloudFormationProduct
- PortfolioProductAssociation
- PortfolioPrincipalAssociation
- LaunchTemplateConstraint
Type: AWS::ServiceCatalog::LaunchRoleConstraint
Properties:
AcceptLanguage: !Ref AcceptLanguage
Description: !Sub "Launch as ${IAMRoleArn}"
PortfolioId: !Ref Portfolio
ProductId: !Ref CloudFormationProduct
RoleArn: !Ref IAMRoleArn
Code language: YAML (yaml)Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-launchconstraint.html
The following are the IAM roles assumed by Service Catalog.
Resources:
LinuxDesktopLaunchRole:
Type: AWS::IAM::Role
DeletionPolicy: Delete
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action: sts:AssumeRole
Principal:
Service:
- servicecatalog.amazonaws.com
Policies:
- PolicyName: LinuxDesktopPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- cloudformation:CreateStack
- cloudformation:DeleteStack
- cloudformation:DescribeStackEvents
- cloudformation:DescribeStacks
- cloudformation:GetTemplateSummary
- cloudformation:SetStackPolicy
- cloudformation:ValidateTemplate
- cloudformation:UpdateStack
Resource: "*"
- Effect: Allow
Action:
- servicecatalog:*
Resource: "*"
- Effect: Allow
Action:
- sns:*
Resource: "*"
- Effect: Allow
Action:
- s3:GetObject
Resource: "*"
Condition:
StringEquals:
s3:ExistingObjectTag/servicecatalog:provisioning: true
- Effect: Allow
Action:
- ec2:*
Resource: "*"
Code language: YAML (yaml)Portfolio Access Permission
Granting a user access to a portfolio enables that user to browse the portfolio and launch the products in it.
Permissions
Resources:
PortfolioPrincipalAssociation:
Type: AWS::ServiceCatalog::PortfolioPrincipalAssociation
Properties:
AcceptLanguage: !Ref AcceptLanguage
PortfolioId: !Ref Portfolio
PrincipalARN: !Ref IAMGroupArn
PrincipalType: IAM
Code language: YAML (yaml)Follow the instructions on the following pages.
https://docs.aws.amazon.com/servicecatalog/latest/adminguide/getstarted-deploy.html
Grant access to the portfolio to the IAM group mentioned above.
Architecting
Use CloudFormation to build this environment and check its actual behavior.
Create CloudFormation stacks and check the resources in the stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following pages.

The parameters of the command used to create the CloudFormation stack are as follows
$ aws cloudformation create-stack \
--stack-name fa-124 \
--template-url [s3-bucket-url]/fa-124.yaml \
--capabilities CAPABILITY_NAMED_IAM CAPABILITY_AUTO_EXPAND
Code language: Bash (bash)After reviewing the resources in each stack, information on the main resources created in this case is as follows
- IAM User: fa-124-User
- IAM Group: fa-124-Endusers
- Portfolio: Engineering Tools
- Product:Linux Desktop
- IAM Role for Service Catalog: fa-124-IAMStack-1URUPL1I86Y-LinuxDesktopLaunchRole-A2RWHWI8I1HD
Check various resources from the AWS Management Console.
Confirm the IAM user.
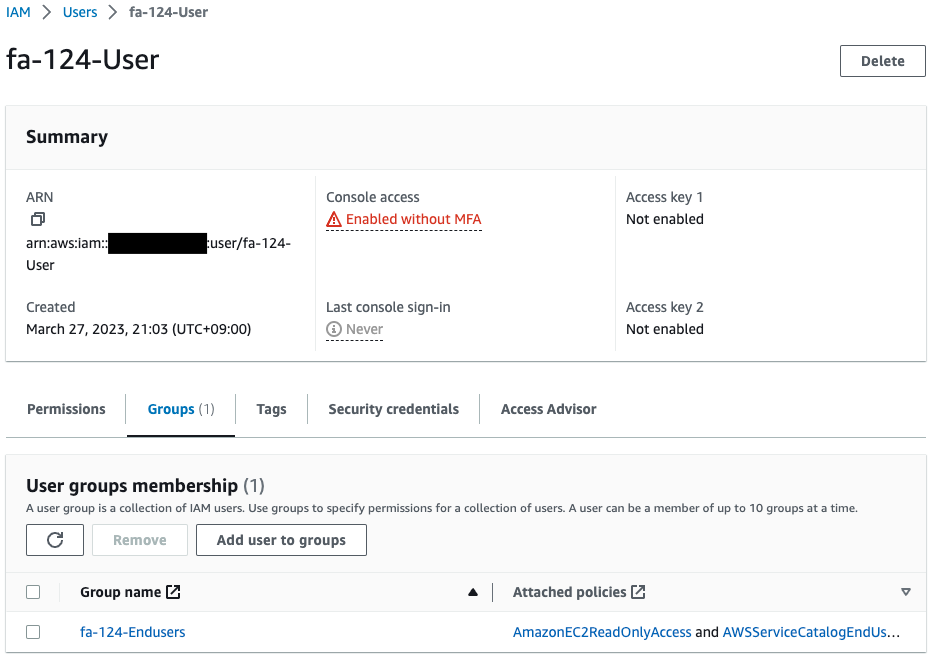
Indeed, a user has been created.
We can also see that this user belongs to fa-124-Endusers.
Check the IAM group.
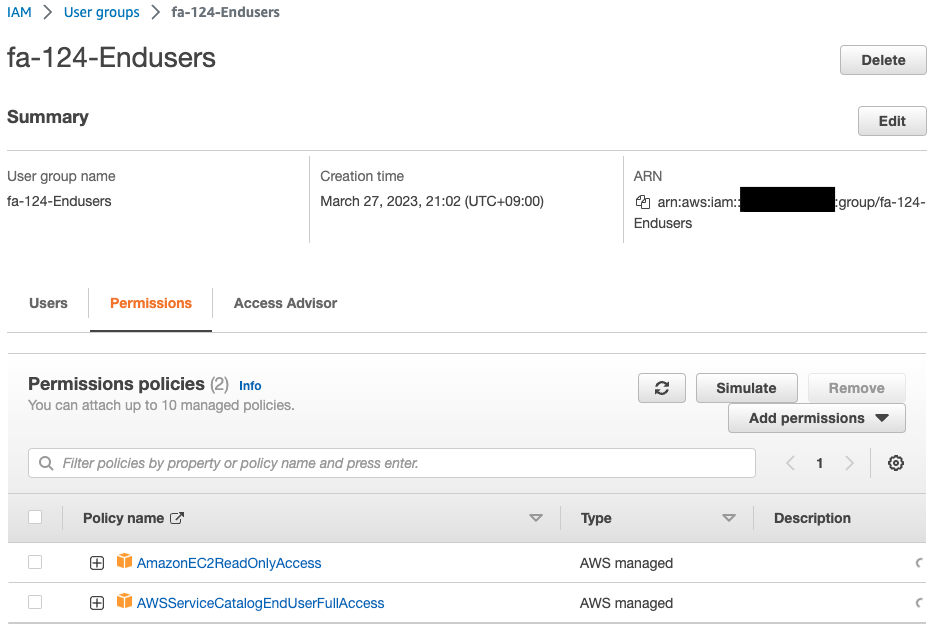
You can see that it was also created successfully.
You can also see that two IAM policies are attached.
Check the portfolio.
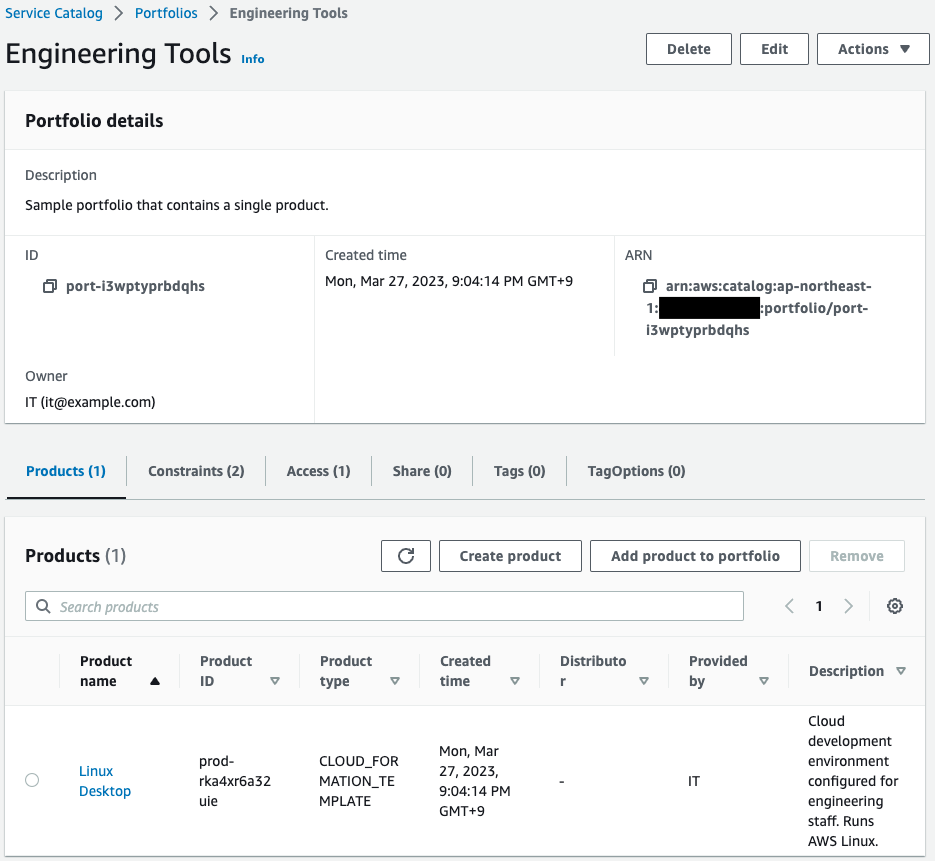
You can see that one product has been created in the portfolio.
Check the contents of this product.
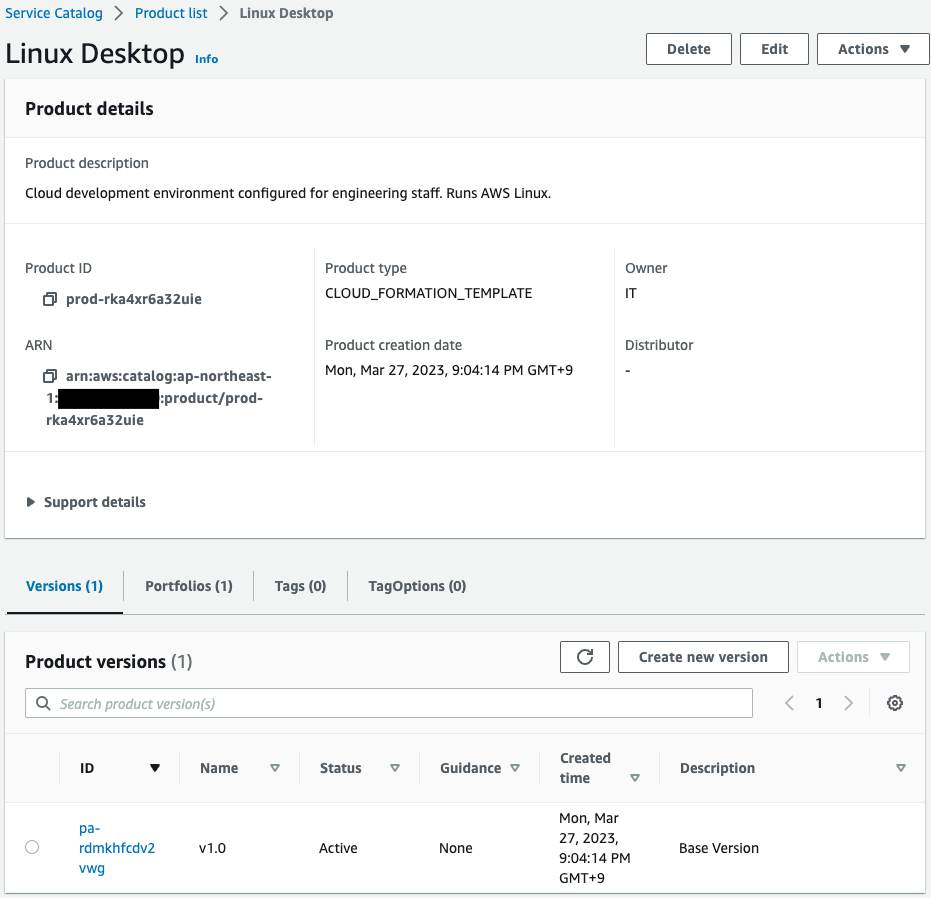
The Versions tab shows that v1.0 has been created.
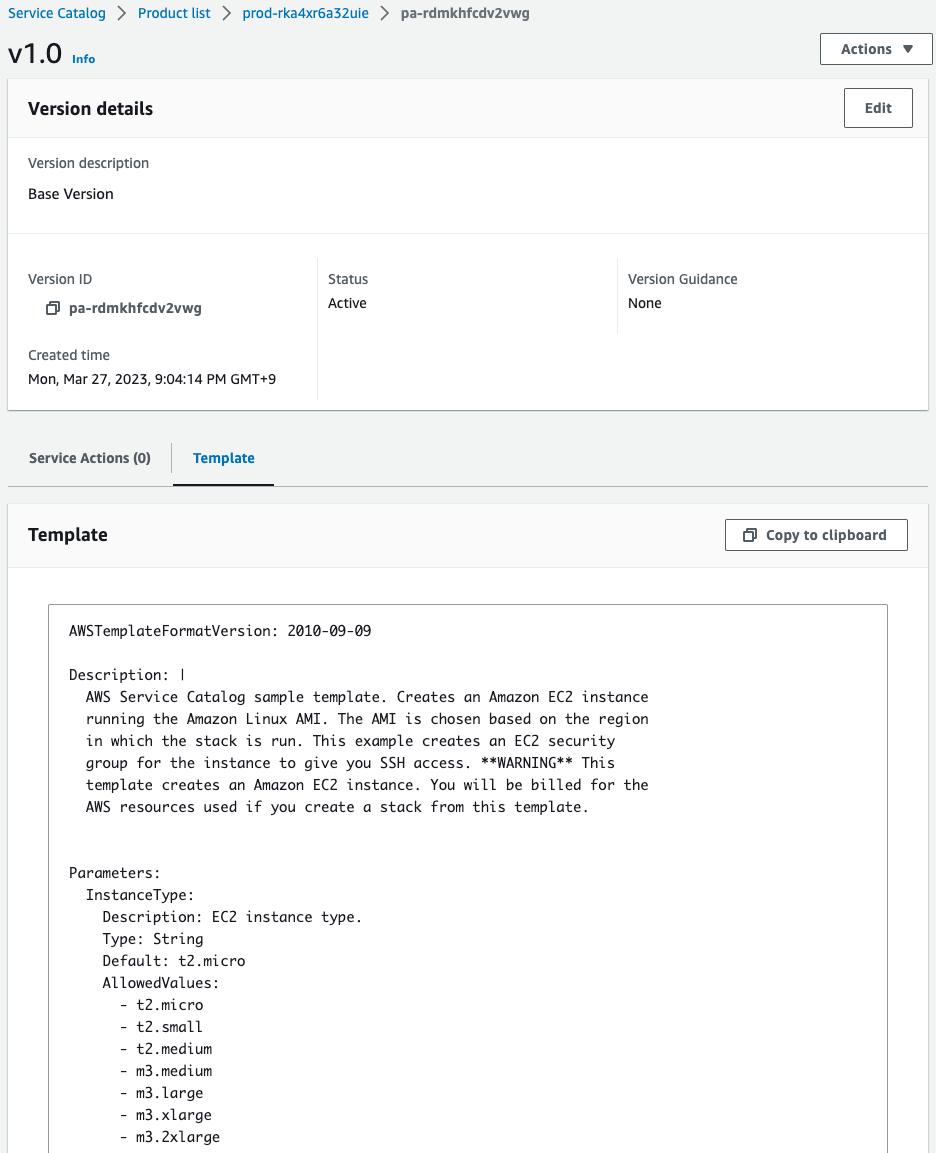
Looking at the version details, we can see the CloudFormation template for the product.
Thus, you can see that the CloudFormation template for the product is tied to the version.
Check the constraints.
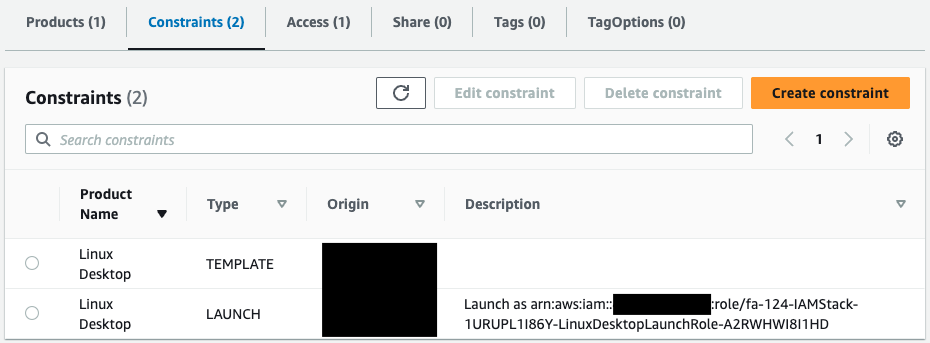
You can see that two constraints have been set.
One is related to the template and the other to the IAM role to be assumed when the product is launched.
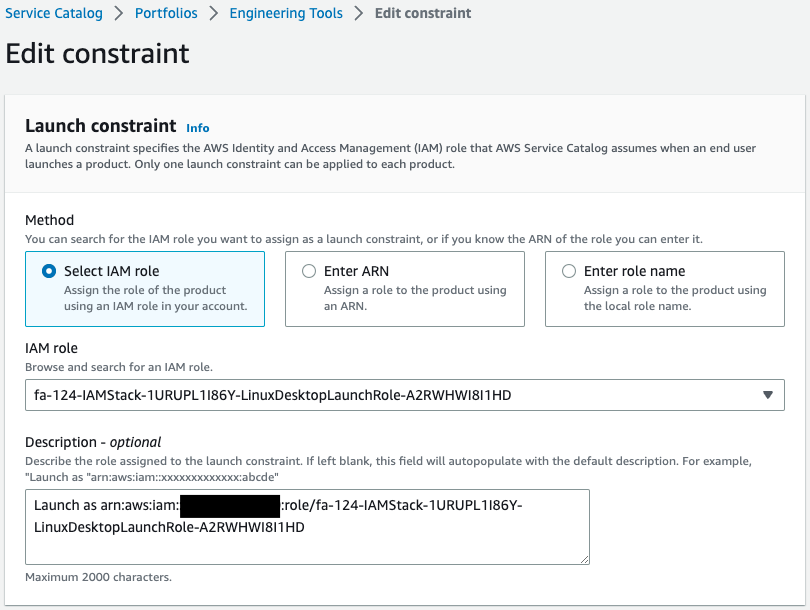
You can see that both have been successfully created.
Check the permissions to access the portfolio.
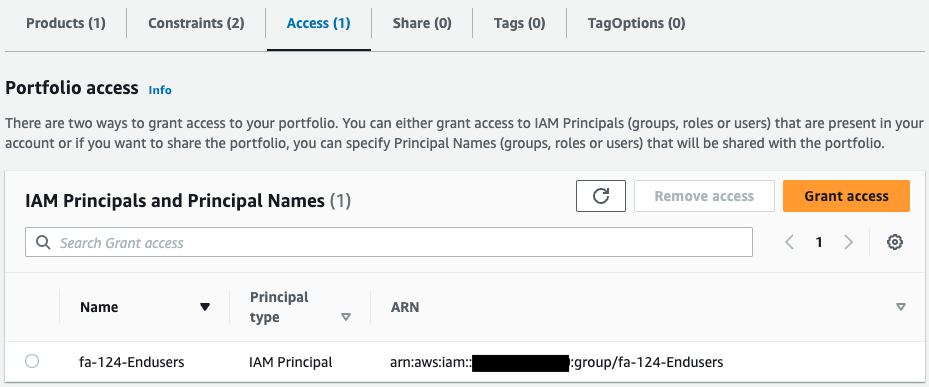
We can see that users in the IAM group fa-124-Endusers have access rights.
Operation Check
Now that you are ready, sign in to the AWS Management Console with the IAM user (fa-124-User).
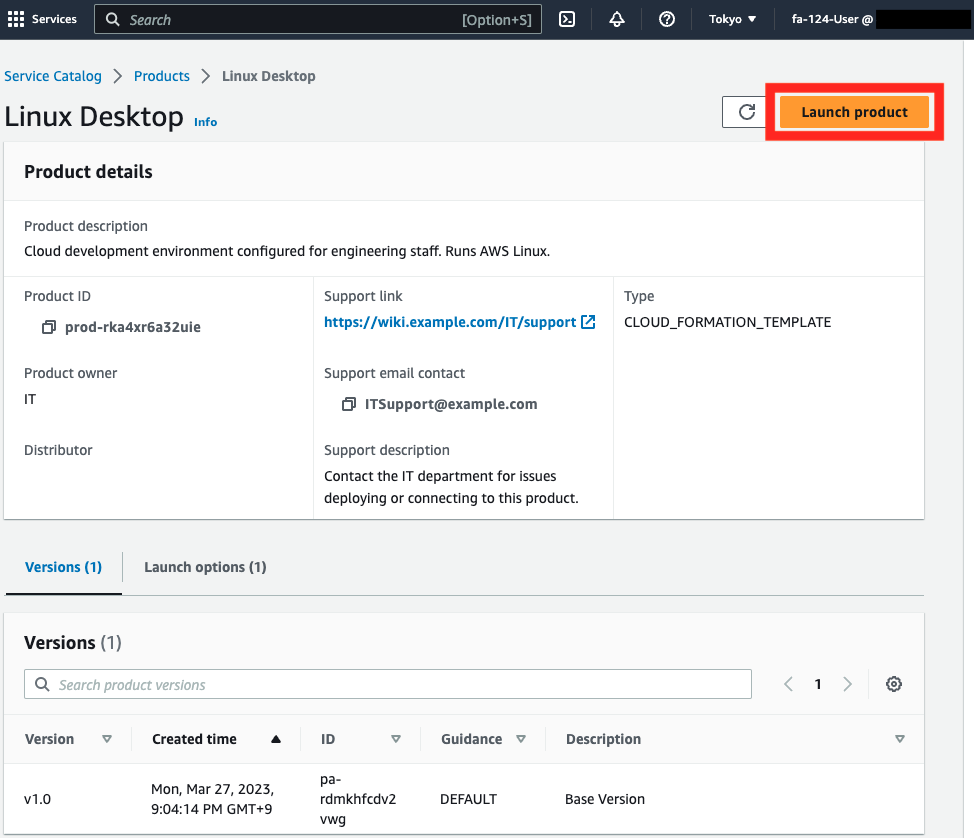
After logging in, if you access the Service Catalog page, you will see the product you have just created.
You can see that access privileges have indeed been granted to this user.
Launch product.
Click on “Launch product”.
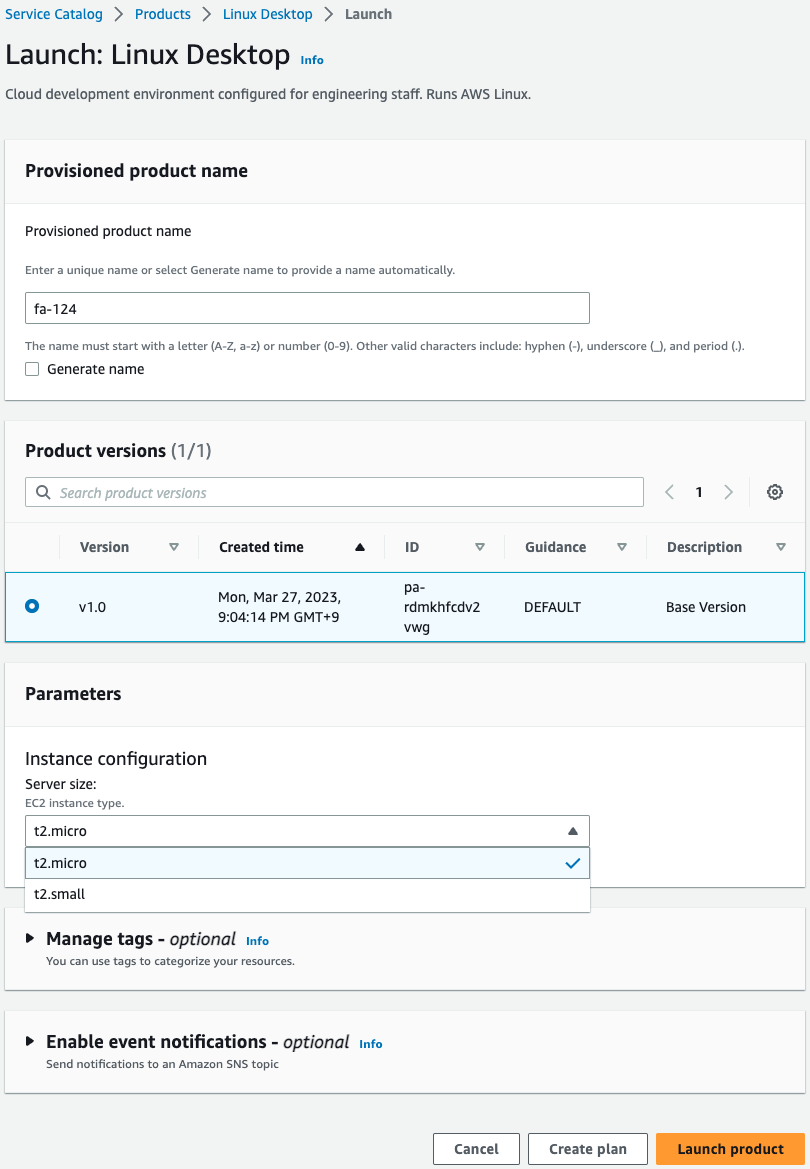
Specify “fa-124” as the provisioned product name.
As confirmed earlier, the product version “v1.0” is available, so specify this.
Specify the parameters of the CloudFormation template for your product in Parameters.
As you can see in the image, originally 7 instance sizes are selectable, but 2 values are selectable.
This is due to template constraints.
In this case, we will specify t2.micro.
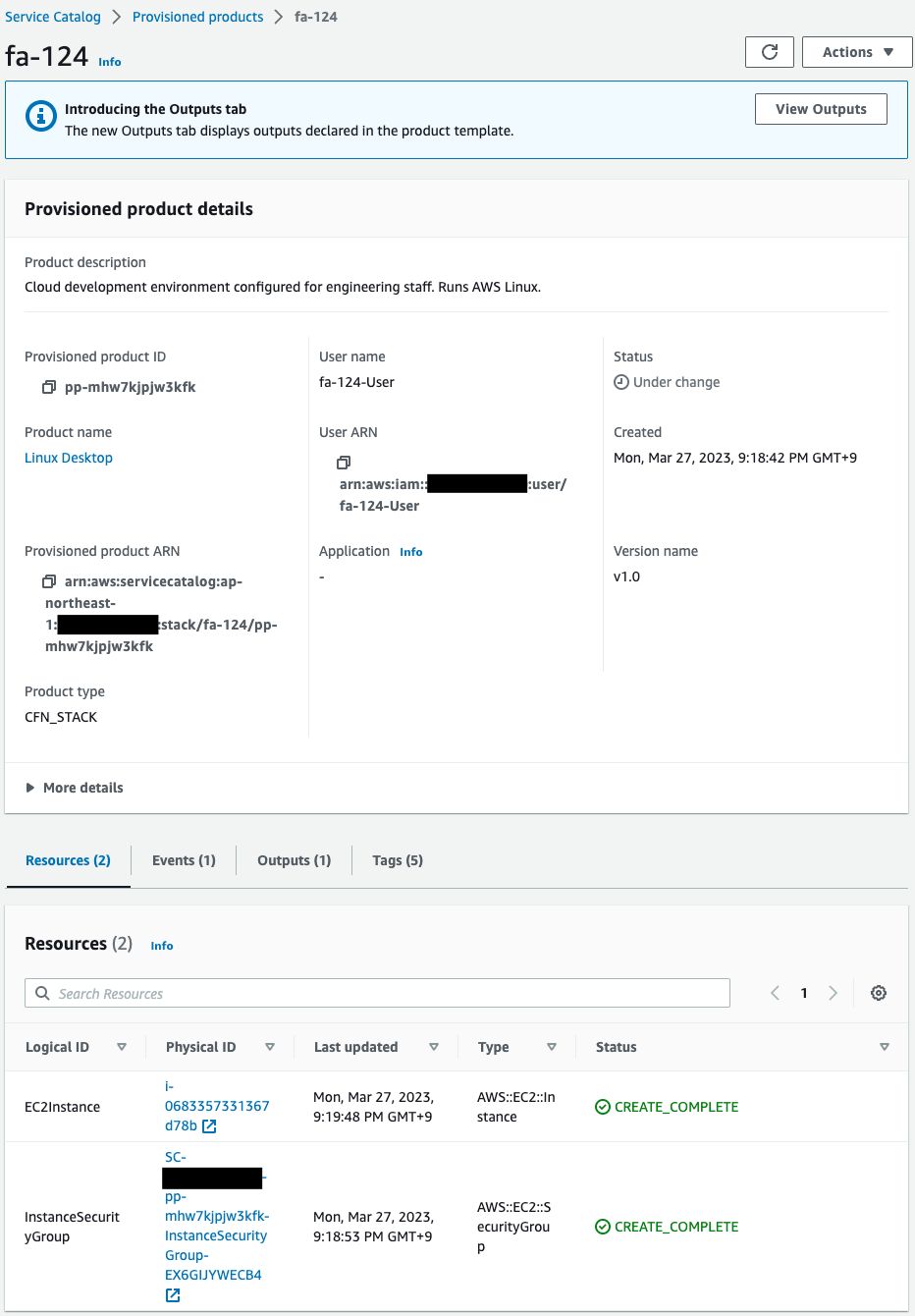
The product is indeed activated.
Resources shows that an EC2 instance and a security group have been created.
Check CloudFormation.
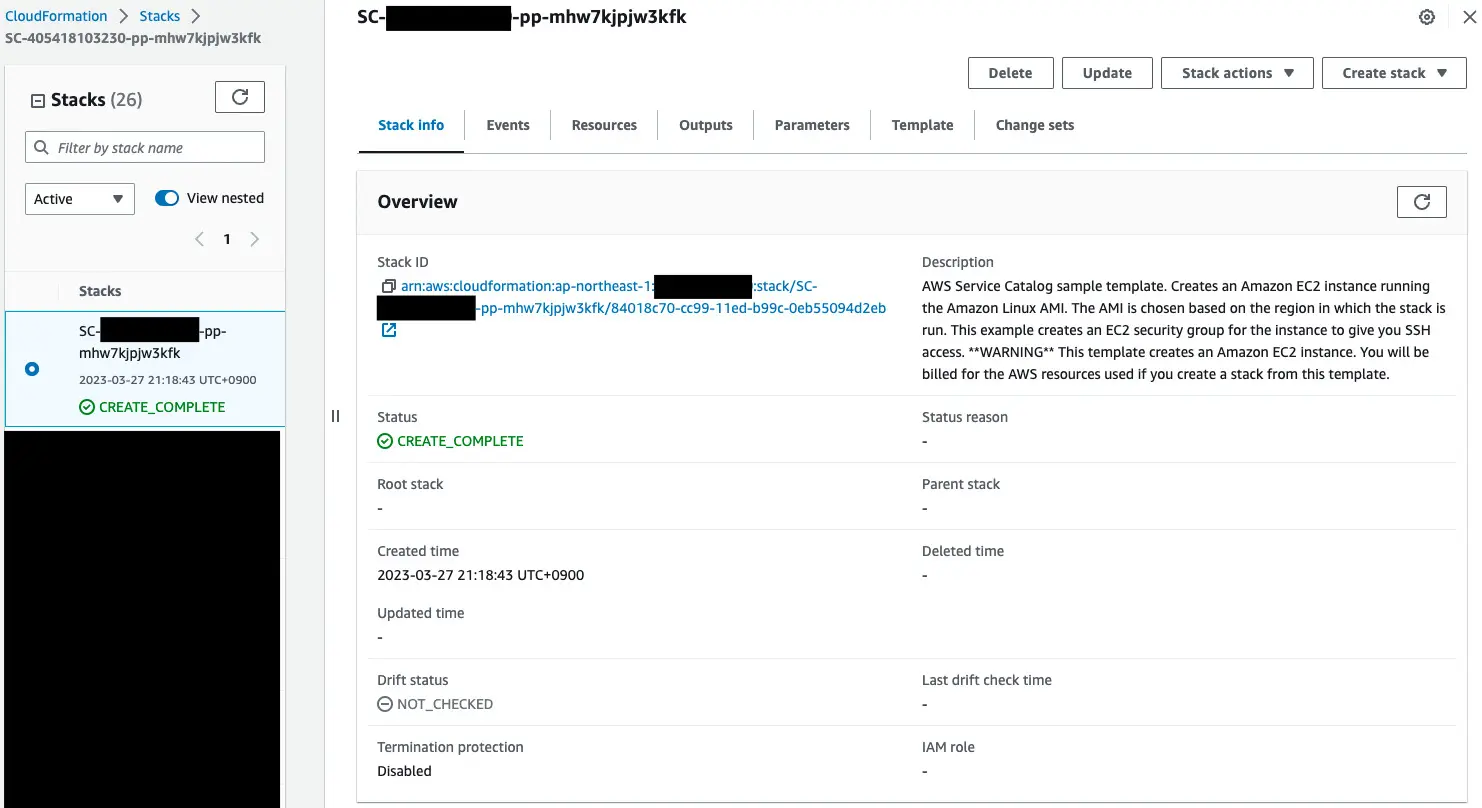
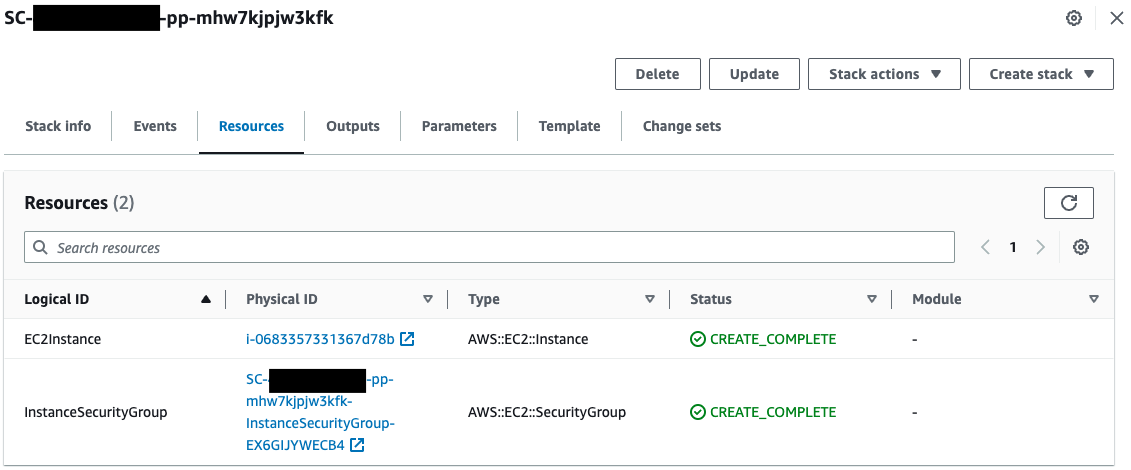
You can see that a new CloudFormation stack has been created by launching the Service Catalog product.
The last two resources created are identified.
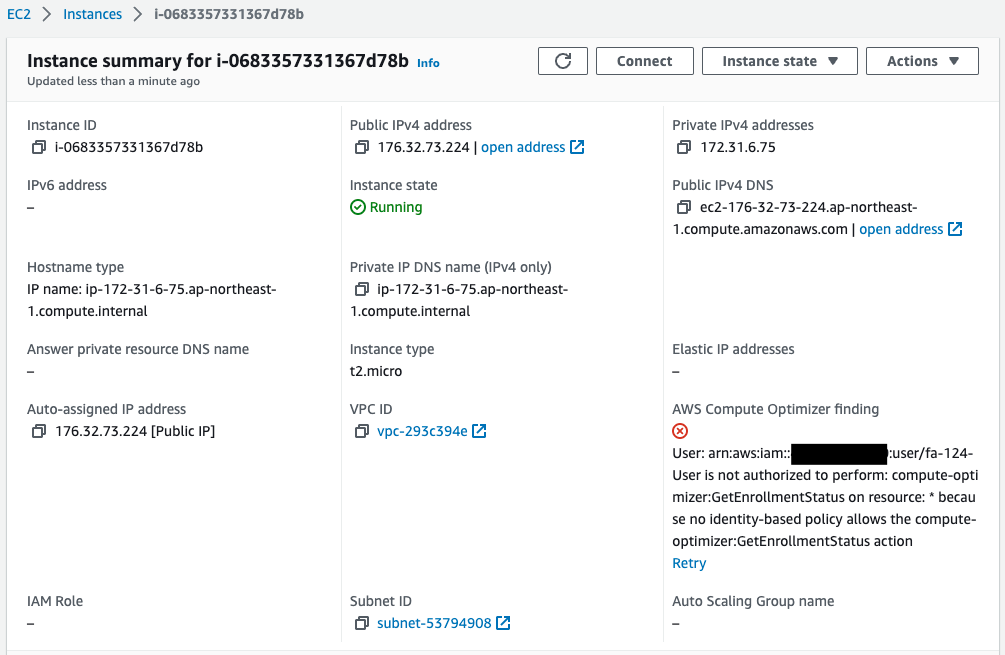
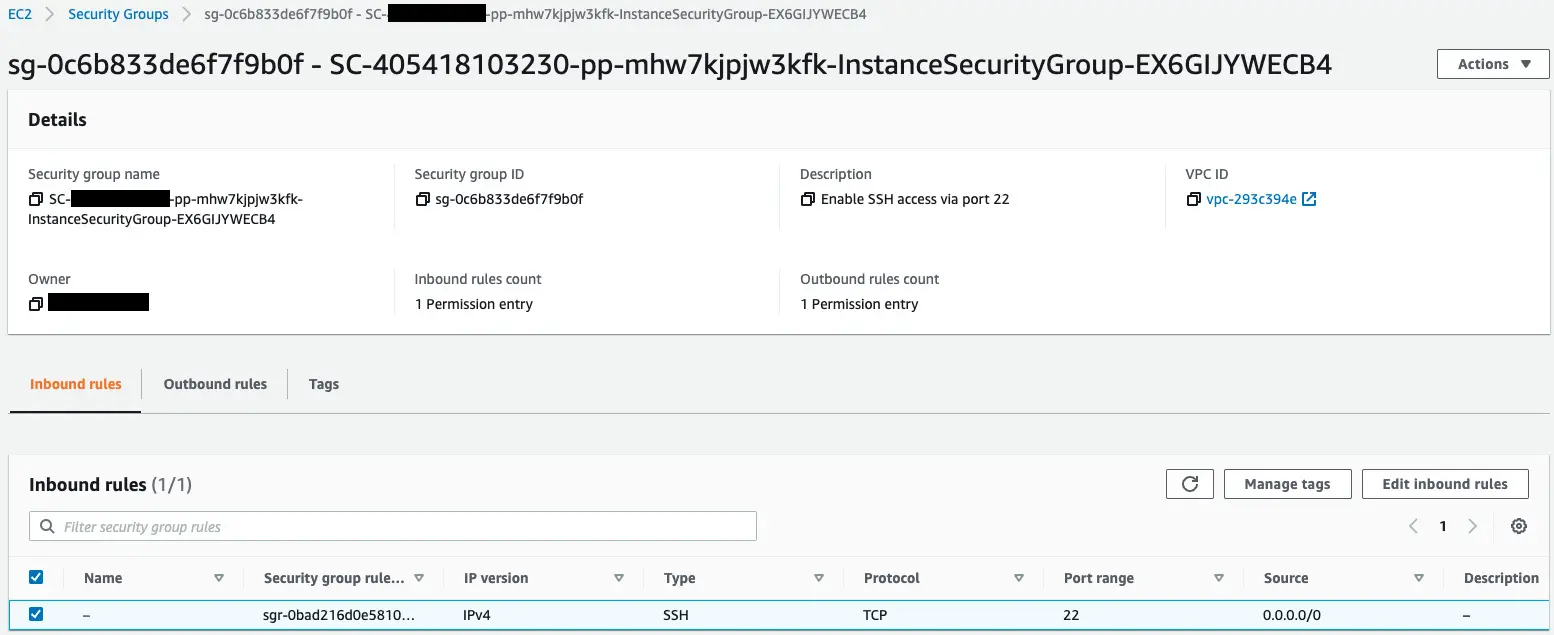
Indeed, an EC2 instance and a security group have been created.
By using Service Catalog in this way, you can allow a group of resources to be created for a specified user, subject to certain conditions.
Summary
Introduction to Service Catalog using CloudFormation.