Use AWS Config to detect outdated access keys
In the following page, Introduction to AWS Config, we showed you how to audit the logging settings of S3 buckets.

This page shows how to detect old access keys that have not been rotated using a similar technique.
Environment
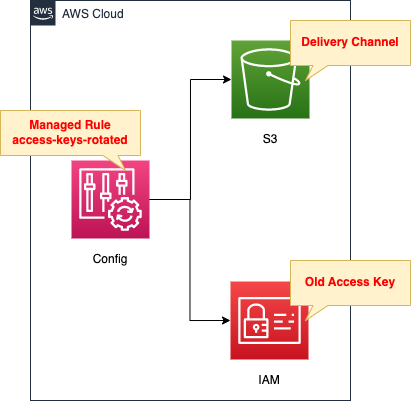
Create a rule in AWS Config to audit access keys.
If a key is detected that is past a certain number of days, it will be non-compliant.
This time the deadline is 90 days.
Create one S3 bucket.
This bucket is used for AWS Config to work.
This bucket stores data about the configuration and modification status of AWS resources.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation templates are placed at the following URL
https://github.com/awstut-an-r/awstut-fa/tree/main/131
Explanation of key points of template files
This page focuses on how to use AWS Config to detect old, non-rotated access keys.
For more information on how to audit resources using AWS Config, please see the following page.

S3
Resources:
ConfigBucket:
Type: AWS::S3::Bucket
Properties:
BucketName: !Ref Prefix
AccessControl: Private
ConfigBucketPolicy:
Type: AWS::S3::BucketPolicy
Properties:
Bucket: !Ref ConfigBucket
PolicyDocument:
Statement:
- Principal:
Service: config.amazonaws.com
Action: s3:GetBucketAcl
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}"
Condition:
StringLike:
AWS:SourceAccount: !Ref AWS::AccountId
- Principal:
Service: config.amazonaws.com
Action: s3:ListBucket
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}"
Condition:
StringLike:
AWS:SourceAccount: !Ref AWS::AccountId
- Principal:
Service: config.amazonaws.com
Action: s3:PutObject
Effect: Allow
Resource: !Sub "arn:aws:s3:::${ConfigBucket}/*"
Condition:
StringLike:
s3:x-amz-acl: bucket-owner-full-control
AWS:SourceAccount: !Ref AWS::AccountId
Code language: YAML (yaml)Bucket for AWS Config delivery channel.
No special configuration is required for the bucket. On the other hand, you can define a bucket policy to allow various accesses from AWS Config.
AWS Config
Delivery Channel
Resources:
DeliveryChannel:
Type: AWS::Config::DeliveryChannel
Properties:
Name: !Sub "${Prefix}-DeliveryChannel"
S3BucketName: !Ref ConfigBucket
Code language: YAML (yaml)Designate the aforementioned bucket as the delivery channel.
Configuration Recorder
Resources:
ConfigurationRecorder:
Type: AWS::Config::ConfigurationRecorder
Properties:
Name: !Sub "${Prefix}-ConfigurationRecorder"
RecordingGroup:
AllSupported: true
IncludeGlobalResourceTypes: true
RoleARN: !Sub "arn:aws:iam::${AWS::AccountId}:role/aws-service-role/config.amazonaws.com/${AWSServiceRoleForConfig}"
AWSServiceRoleForConfig:
Type: AWS::IAM::ServiceLinkedRole
DeletionPolicy: Delete
Properties:
AWSServiceName: config.amazonaws.com
Code language: YAML (yaml)When auditing against a global resource such as an access key, the AllSupported/IncludeGlobalResourceTypes property is key, as in the following quote
Specifies whether AWS Config includes all supported types of global resources (for example, IAM resources) with the resources that it records.
Before you can set this option to true, you must set the AllSupported option to true.
AWS::Config::ConfigurationRecorder RecordingGroup
Set both properties to “true” according to the above.
AWS Config Rule
Resources:
ConfigRule:
Type: AWS::Config::ConfigRule
DependsOn:
- ConfigurationRecorder
Properties:
ConfigRuleName: !Sub "${Prefix}-IAM-Access-Keys-Rotated"
InputParameters:
maxAccessKeyAge: 90
Source:
Owner: AWS
SourceIdentifier: ACCESS_KEYS_ROTATED
Code language: YAML (yaml)The managed rule access-key-rotated can be used to detect old access keys that have not been rotated.
https://docs.aws.amazon.com/config/latest/developerguide/access-keys-rotated.html
Specify “ACCESS_KEYS_ROTATED” for the SourceIdentifier property.
This rule also takes the following parameters
maxAccessKeyAge
Type: int
Default: 90
Maximum number of days without rotation.
access-keys-rotated
Set the InputParameters property in the format “maxAccessKeyAge: 90”.
Architecting
Use CloudFormation to build this environment and check its actual behavior.
Create CloudFormation stacks and check the resources in the stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please see the following page.

After reviewing the resources in each stack, information on the main resources created in this case is as follows
- AWS Config rule: fa-131-IAM-Access-Keys-Rotated
Check the created resource from the AWS Management Console.
Check the basic settings in AWS Config.
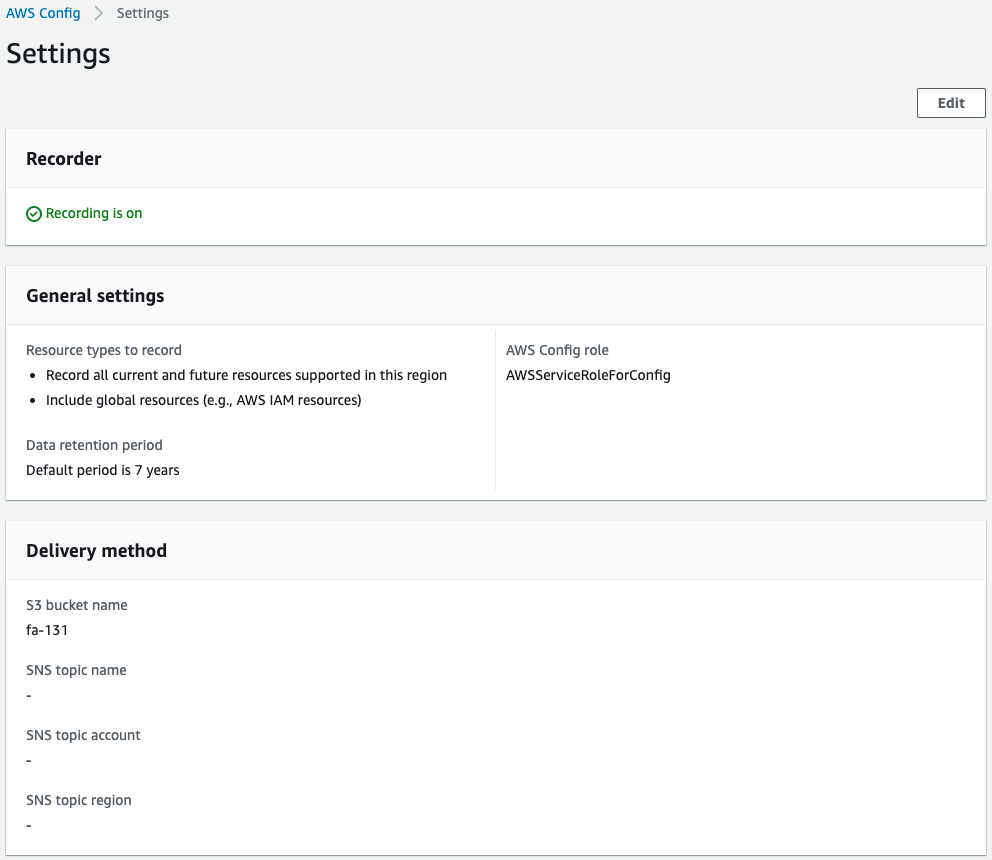
We can see that all resources, including global resources, are targeted by the recorder.
We also see that the aforementioned S3 bucket is specified as the destination.
Operation Check
Now that you are ready, check the audit results of the AWS Config rules.
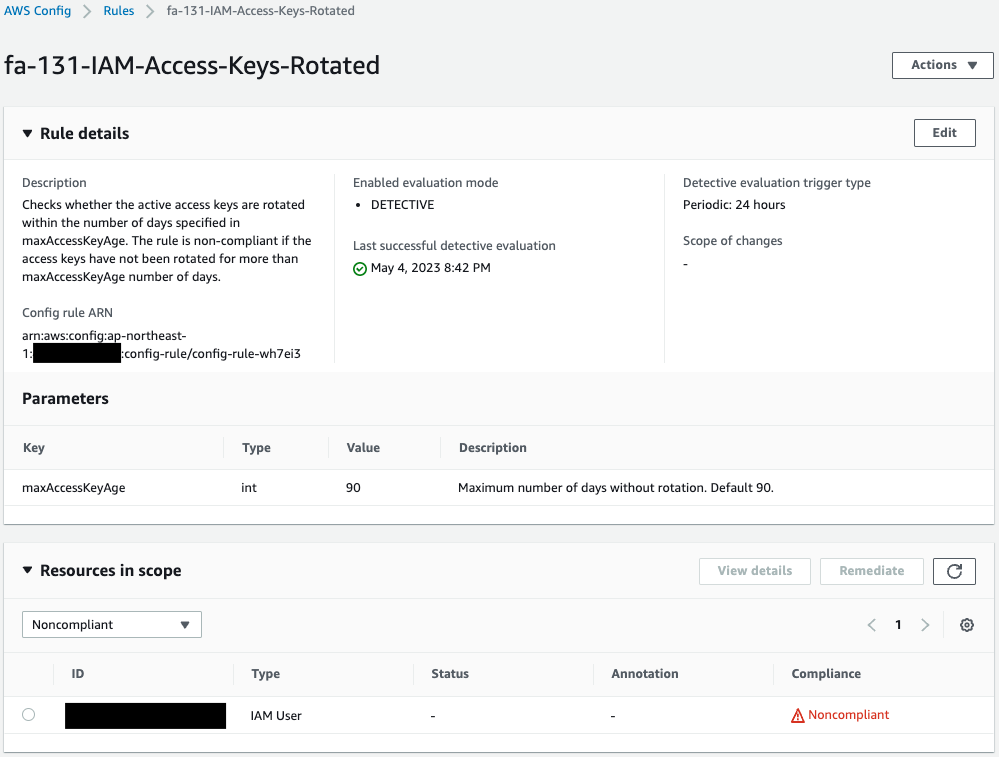
You can confirm that the rule has been successfully created.
One IAM user is listed as non-compliant with this rule.
Check this user’s details.
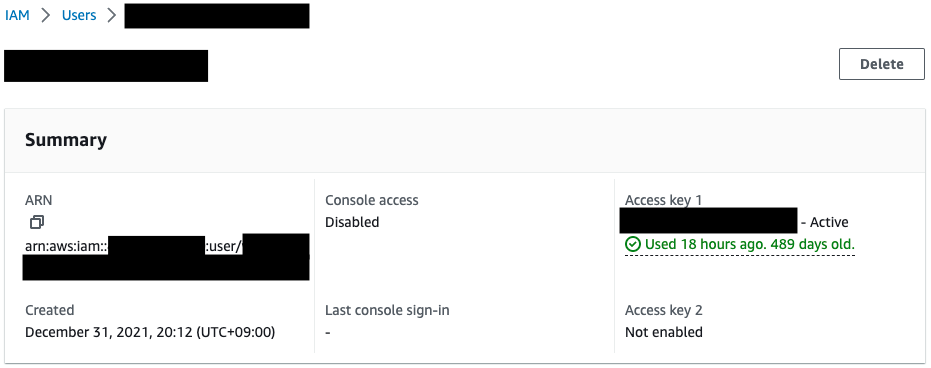
It is true that the access key is past due (90 days).
Thus, AWS Config can be used to detect old access keys that have not been rotated.
Summary
We have identified a way to detect old access keys that have not been rotated.