Access NLB in another VPC via VPC Endpoint
One of the features provided by VPC endpoints is the VPC Endpoint Service (PrivateLink).
You can create your own service powered by AWS PrivateLink, known as an endpoint service. You are the service provider, and the AWS principals that create connections to your service are the service consumers.
Create a service powered by AWS PrivateLink
This time we will use the VPC endpoint service to access the NLB on another VPC.
構築する環境
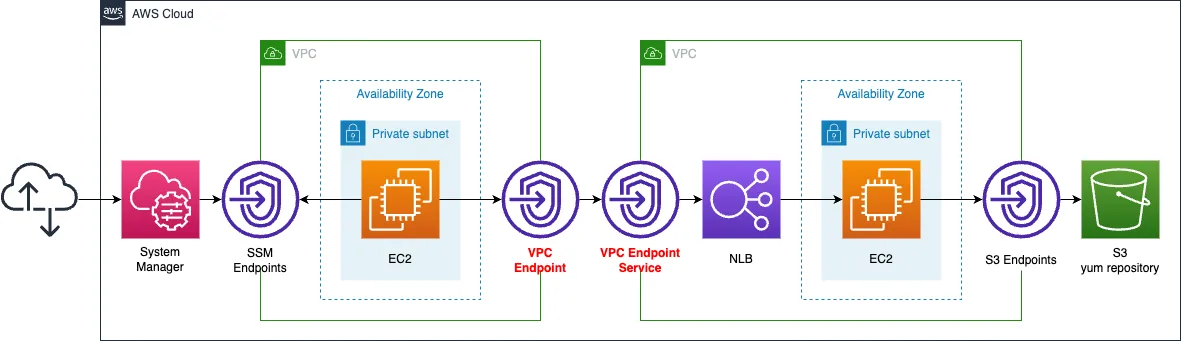
Create two VPCs.
The VPC on the other hand deploys NLB and EC2 instances.
The instance belongs to the NLB target group.
Apache is installed on the instance to run as a web server.
The other VPC will house an EC2 instance.
The role of this instance is to access the aforementioned NLB as a test.
Create three types of VPC endpoints.
The first is for S3.
It is used to install Apache on instances in the NLB target group.
The second is for SSM.
SSM Session Manager and is used to access test instances.
The third is for NLB.
It is used by the testing instance to access the NLB.
CloudFormation template files
The above configuration is built with CloudFormation.
The CloudFormation templates are placed at the following URL
https://github.com/awstut-an-r/awstut-saa/tree/main/03/002
Explanation of key points of template files
NLB
Resources:
NLB:
Type: AWS::ElasticLoadBalancingV2::LoadBalancer
Properties:
Name: !Sub "${Prefix}-NLB"
Scheme: internal
Subnets:
- !Ref PrivateSubnet
Type: network
NLBTargetGroup:
Type: AWS::ElasticLoadBalancingV2::TargetGroup
Properties:
Name: !Sub "${Prefix}-NLBTargetGroup"
Protocol: TCP
Port: !Ref HTTPPort
VpcId: !Ref VPC
Targets:
- Id: !Ref Instance
NLBListener:
Type: AWS::ElasticLoadBalancingV2::Listener
Properties:
DefaultActions:
- TargetGroupArn: !Ref NLBTargetGroup
Type: forward
LoadBalancerArn: !Ref NLB
Port: !Ref HTTPPort
Protocol: TCP
Code language: YAML (yaml)Create the three resources (NLB body, target group, and listener) that make up the NLB.
Specify an EC2 instance (described below) as the target.
No special configuration is required.
VPC Endpoint Service
Resources:
VPCEndpointService:
Type: AWS::EC2::VPCEndpointService
Properties:
AcceptanceRequired: false
NetworkLoadBalancerArns:
- !Ref NLB
Code language: YAML (yaml)This is a VPC endpoint service to access the NLB from outside the VPC.
There are two key parameters in creating a VPC endpoint service.
The first is the AcceptanceRequired property.
The AWS official explanation of this property is as follows
You can configure your endpoint service to accept connection requests automatically. Otherwise, you must accept or reject them manually. If you do not accept a connection request, the service consumer can’t access your endpoint service.
Accept or reject connection requests
This time, since manual acceptance is not performed, “false” is specified for this property.
The second is the NetworkLoadBalancerArns property.
Specify the aforementioned NLB for this.
This means that this VPC endpoint service is for NLB.
EC2 (NLB side)
Resources:
Instance:
Type: AWS::EC2::Instance
Properties:
ImageId: !Ref ImageId
InstanceType: !Ref InstanceType
NetworkInterfaces:
- DeviceIndex: 0
SubnetId: !Ref PrivateSubnet
GroupSet:
- !Ref InstanceSecurityGroup
UserData: !Base64 |
#!/bin/bash -xe
yum update -y
yum install -y httpd
systemctl start httpd
systemctl enable httpd
ec2-metadata -i > /var/www/html/index.html
Code language: YAML (yaml)EC2 instance in the NLB target group.
The initialization process of the instance is performed using user data.
For details on initialization, please refer to the following page.

During the initialization process, Apache is installed and runs as a web server.
VPC endpoint for NLB
Resources:
NLBEndpoint:
Type: AWS::EC2::VPCEndpoint
Properties:
PrivateDnsEnabled: false
SecurityGroupIds:
- !Ref NLBEndpointSecurityGroup
ServiceName: !Sub "com.amazonaws.vpce.${AWS::Region}.${VPCEndpointService}"
SubnetIds:
- !Ref PrivateSubnet
VpcEndpointType: Interface
VpcId: !Ref VPC
Code language: YAML (yaml)VPC endpoint for NLB.
Used by test EC2 instances to access the NLB.
The key point is the ServiceName property.
As shown below, specify a string that embeds the ID of the aforementioned VPC endpoint service.
com.amazonaws.vpce.[region-id].[vpc-endpoint-service-id]
Check the security group for this endpoint.
Resources:
NLBEndpointSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupName: !Sub "${Prefix}-NLBEndpointSecurityGroup"
GroupDescription: Allow HTTP from InstanceSecurityGroup.
VpcId: !Ref VPC
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: !Ref HTTPPort
ToPort: !Ref HTTPPort
SourceSecurityGroupId: !Ref InstanceSecurityGroup
Code language: YAML (yaml)The EC2 instance under the NLB is running as a web server and listening on HTTP (80/tcp).
Therefore, the security group for the VPC endpoints also allows HTTP in the same way.
Architecting
Use CloudFormation to build this environment and check its actual behavior.
Create CloudFormation stacks and check the resources in the stacks
Create CloudFormation stacks.
For information on how to create stacks and check each stack, please refer to the following pages.

After reviewing the resources in each stack, information on the main resources created in this case is as follows
- NLB: saa-03-002-NLB
- VPC endpoint service for NLB: vpce-svc-074f49920d0314071
- VPC endpoint for NLB: vpce-00e74a560c595e218
- EC2 instance under NLB: i-086f1f474294d9822
- EC2 instance for testing: i-08a48ca7d3b86d91d
Check each resource from the AWS Management Console.
Check the NLB.
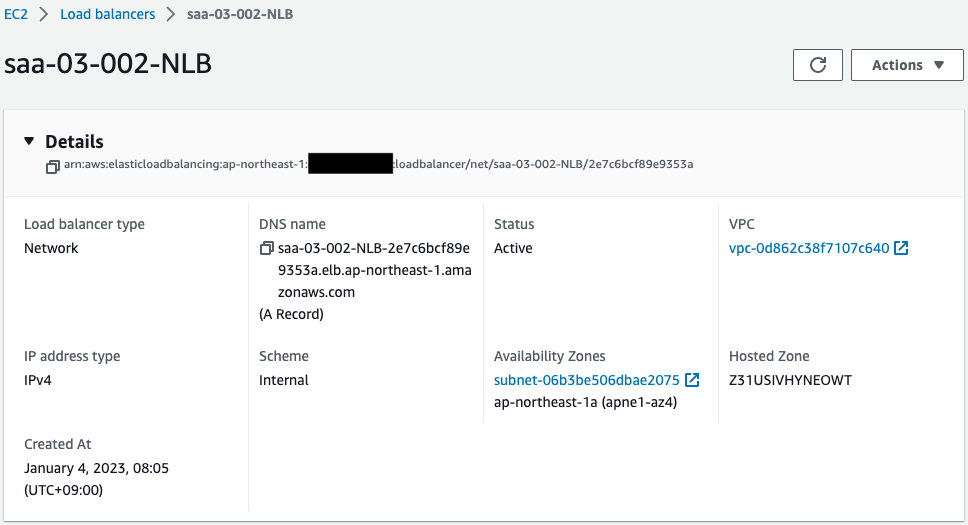
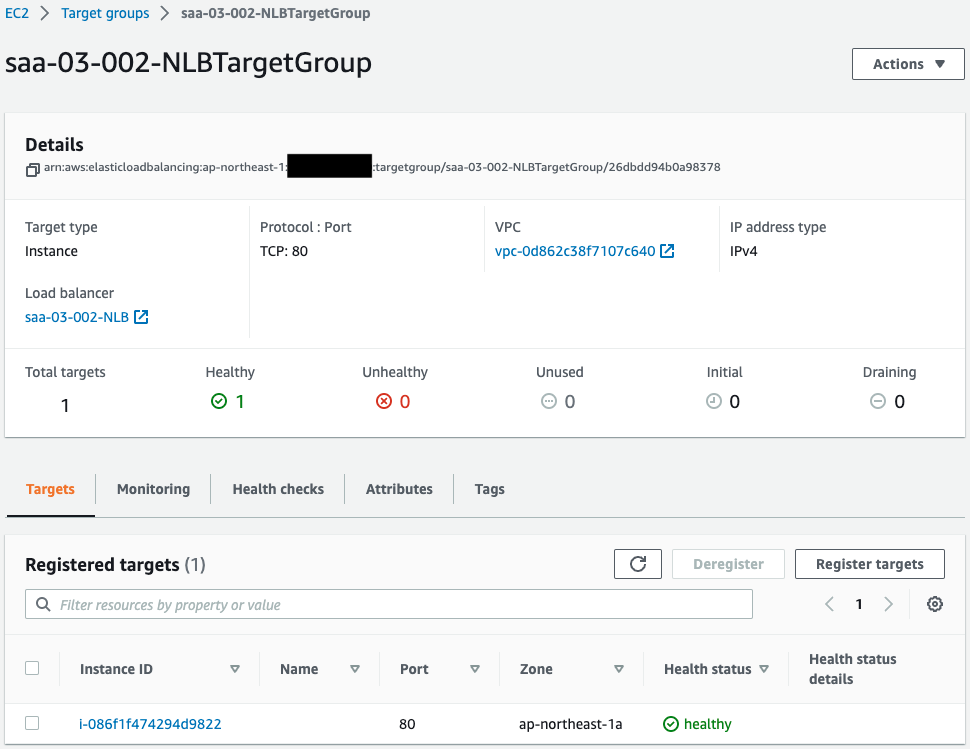
The NLB has been successfully created.
You can see that one instance is registered in the target group.
Check VPC endpoint service.
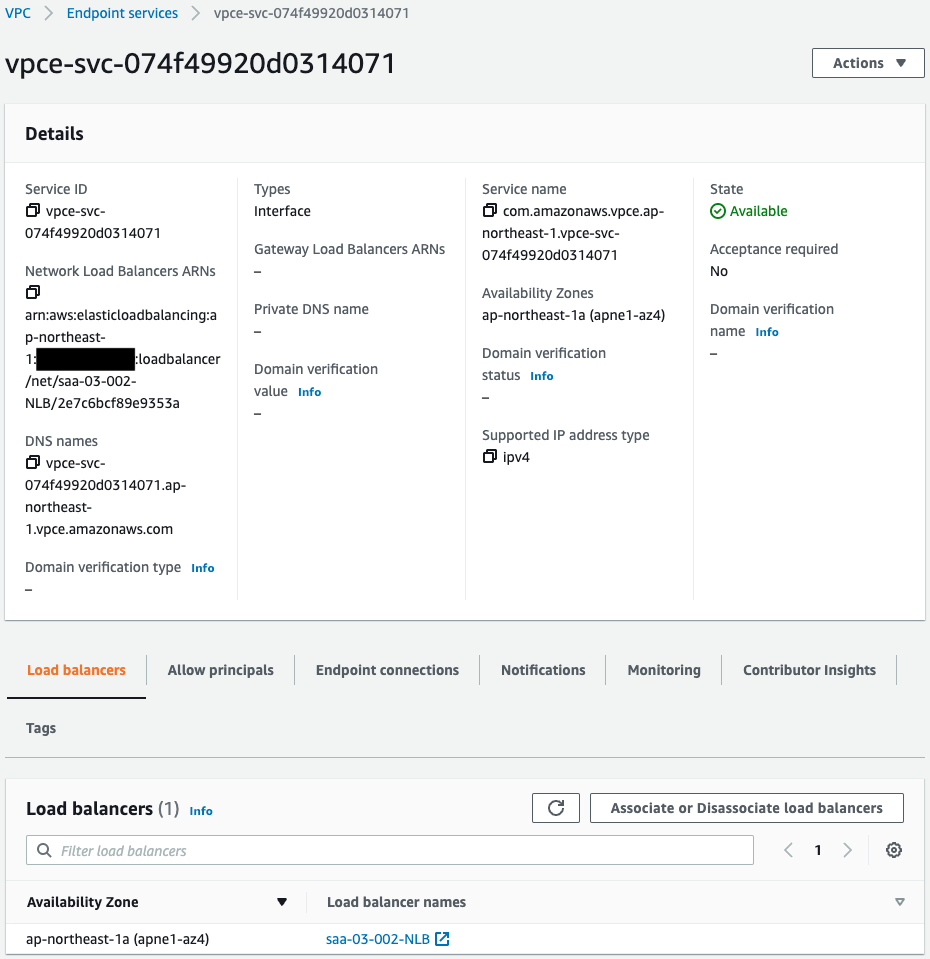
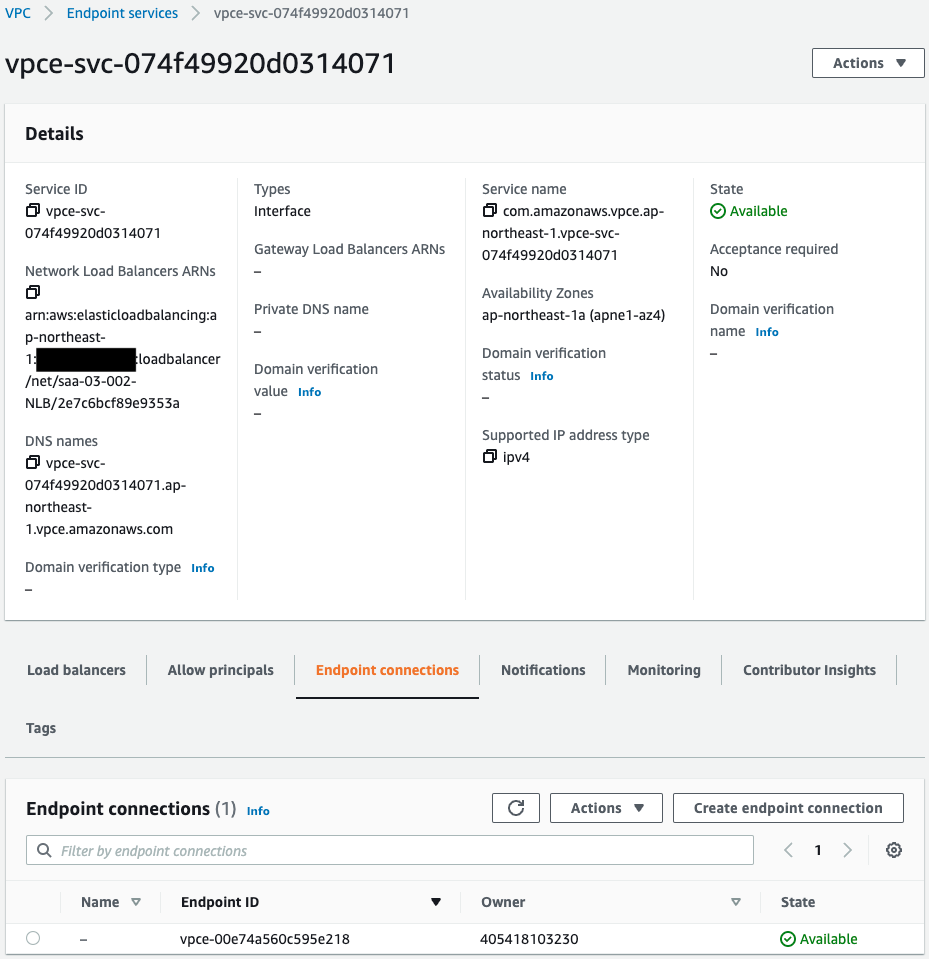
The associated load balancer shows that the aforementioned NLB is registered.
The endpoint connection shows that the VPC endpoint described below is registered.
Check VPC endpoints for NLB.
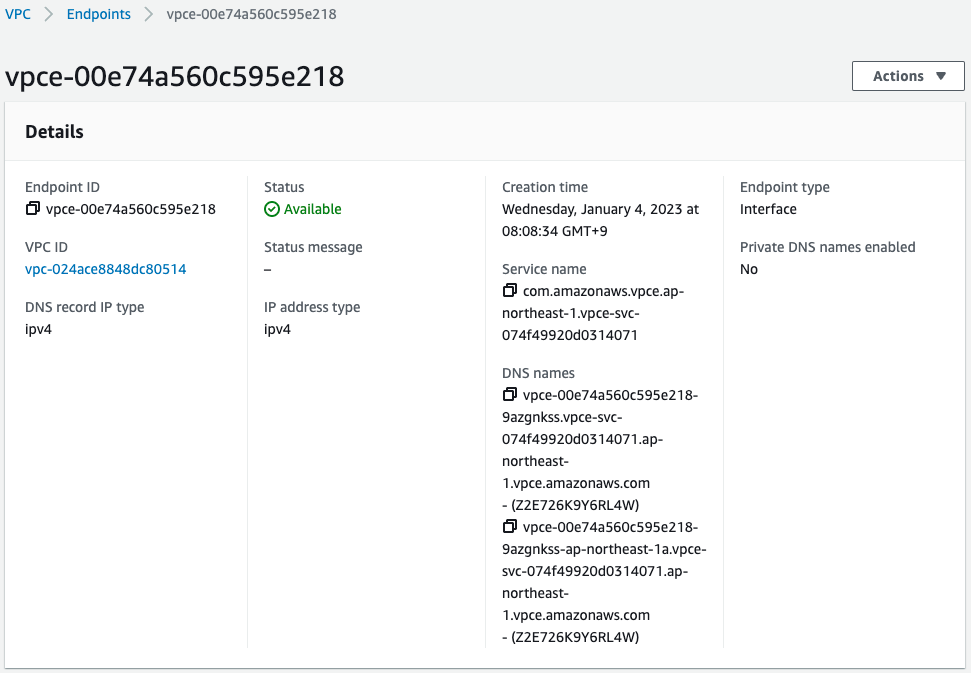
Looking at the service name, a string containing the ID of the aforementioned VPC endpoint service is set.
You will see that the following two DNS names are set
vpce-00e74a560c595e218-9azgnkss.vpce-svc-074f49920d0314071.ap-northeast-1.vpce.amazonaws.com
vpce-00e74a560c595e218-9azgnkss-ap-northeast-1a.vpce-svc-074f49920d0314071.ap-northeast-1.vpce.amazonaws.com
Operation Check
Now that you are ready, access the test instance.
Access is via SSM Session Manager.
% aws ssm start-session --target i-08a48ca7d3b86d91d
…
sh-4.2$
Code language: Bash (bash)For more information on SSM Session Manager, please refer to the following page.

Access VPC endpoints for NLB.
sh-4.2$ curl http://vpce-00e74a560c595e218-9azgnkss.vpce-svc-074f49920d0314071.ap-northeast-1.vpce.amazonaws.com
instance-id: i-086f1f474294d9822
sh-4.2$ curl http://vpce-00e74a560c595e218-9azgnkss-ap-northeast-1a.vpce-svc-074f49920d0314071.ap-northeast-1.vpce.amazonaws.com
instance-id: i-086f1f474294d9822
Code language: Bash (bash)Both responses were received.
The responses are from instances in the NLB target group.
This means that traffic destined for the VPC endpoint for NLB was sent for the VPC endpoint service in another VPC, and from there it went through NLB to the instance.
summary
We have identified a way to access NLB on another VPC using the VPC endpoint service.